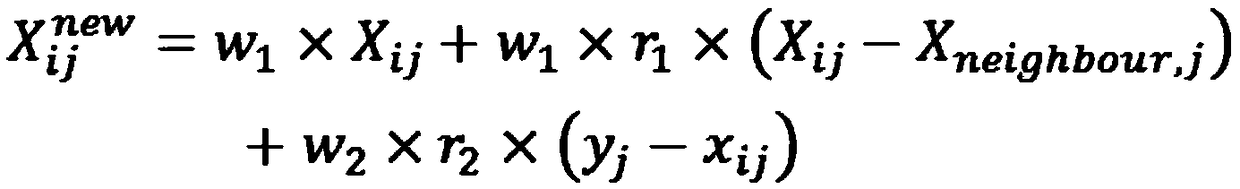Intrusion detection method and system of BP algorithm based on artificial swarm optimization
A technology of artificial bee colony optimization and BP algorithm, applied in the intrusion detection method of BP algorithm and its system field, can solve problems such as easy to fall into local minimum point, slow convergence speed of BP neural network, and large amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
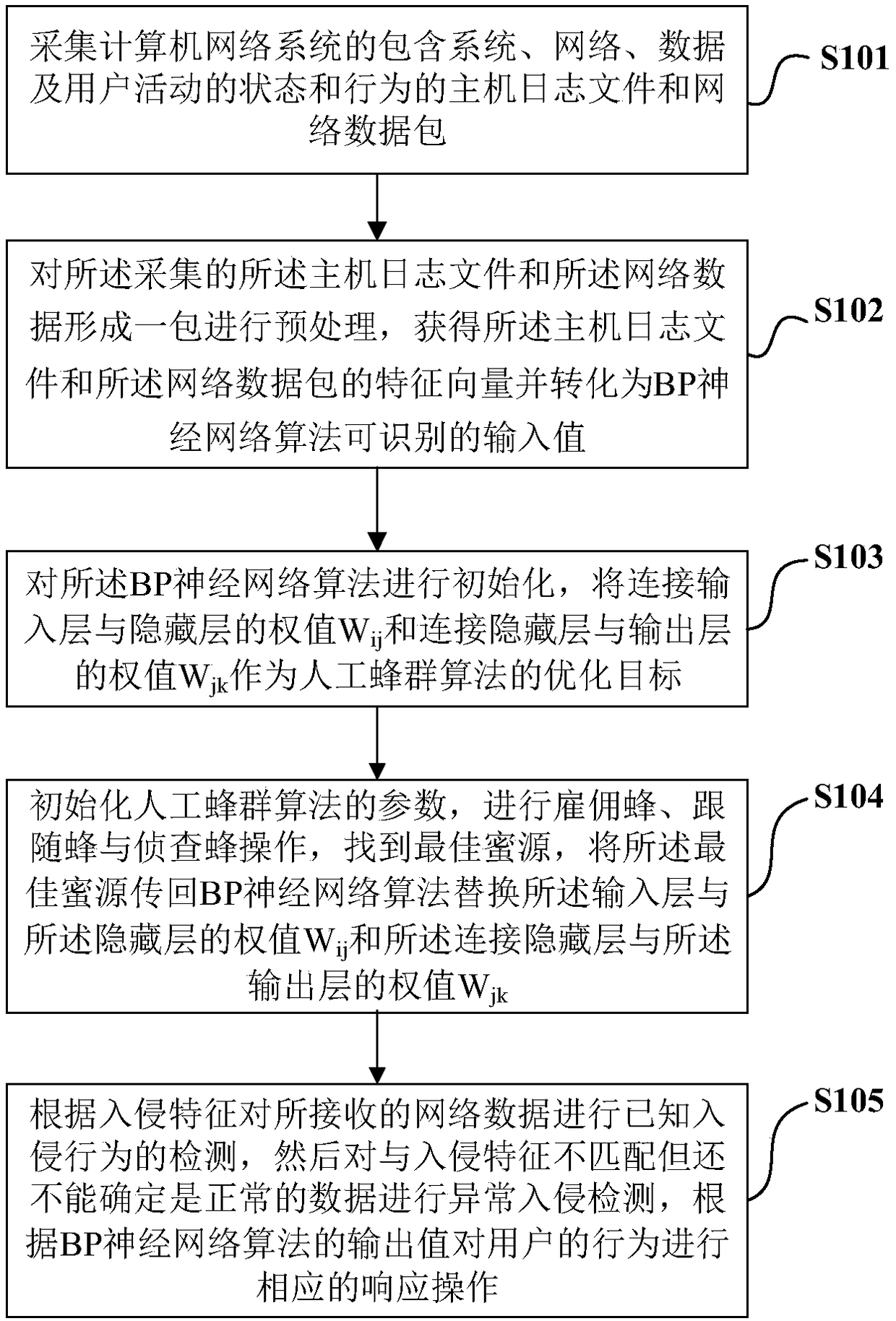
[0076] Such as figure 1 Shown, a kind of intrusion detection method based on artificial bee colony optimization BP algorithm, this method comprises the following steps:
[0077] S101. Collect host log files and network data of the computer network system including the status and behavior of the system, network, data and user activities;
[0078] The network system information used by intrusion detection generally comes from the following four aspects:
[0079] First, system and network log files
[0080] Hackers often leave their traces in system log files, so making full use of system and network log file information is a necessary condition for intrusion detection. Logs contain evidence of unusual and unexpected activity on systems and networks that can indicate that someone is breaking into or has successfully broken into a system. By viewing log files, successful intrusions or intrusion attempts can be found, and corresponding emergency response procedures can be activa...
Embodiment 2
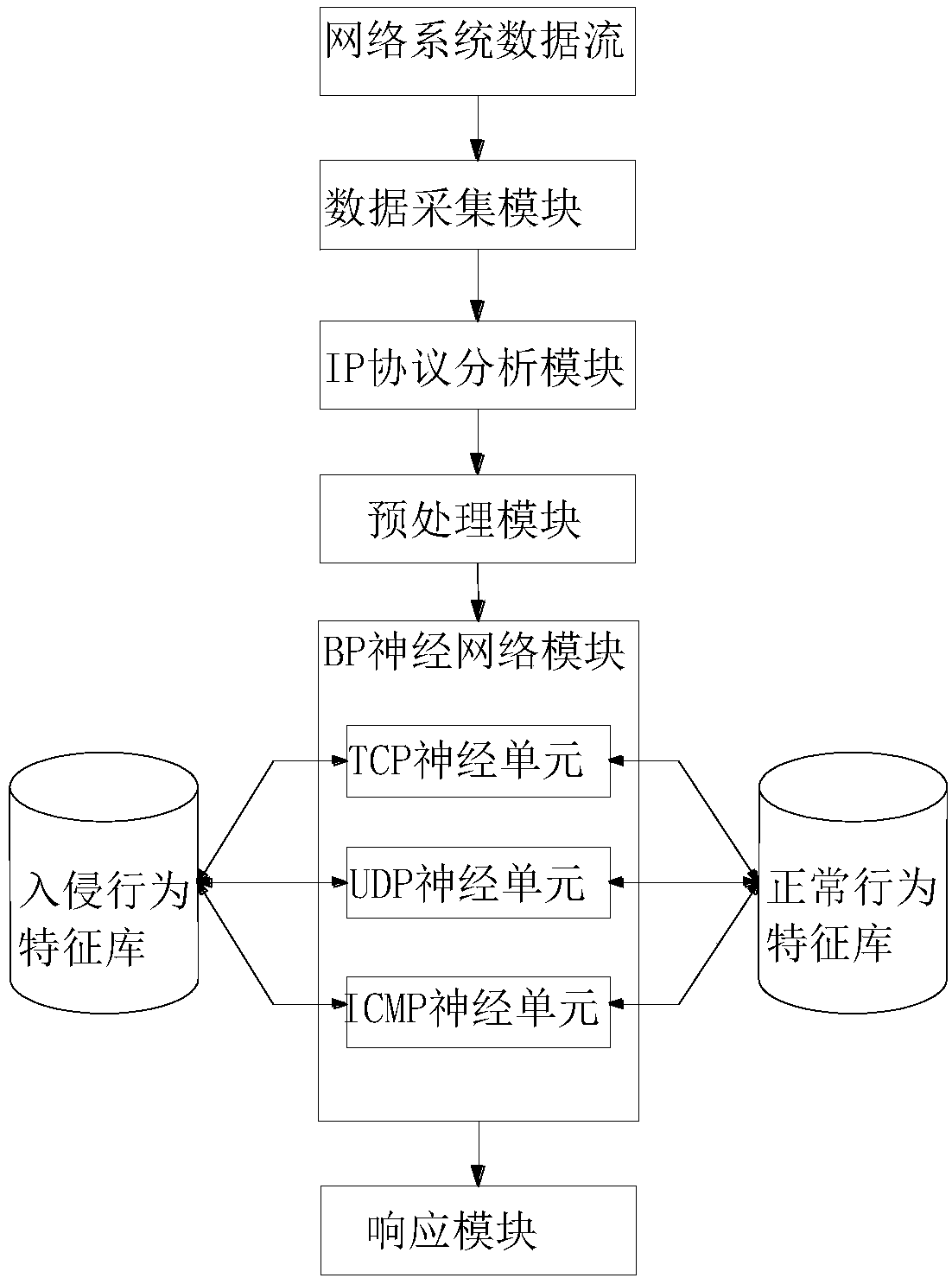
[0137] Based on the same inventive concept, another aspect of the present invention, such as figure 2 As shown, an intrusion detection system based on artificial bee colony optimization BP algorithm is provided, and the system includes:
[0138] The data collection module is used to collect host log files and network data including the state and behavior of the system, network, data and user activities of the computer network system;
[0139] A preprocessing module, configured to preprocess the collected host log files and the network data into a package, obtain the feature vectors of the host log files and the network data and convert them into BP neural network algorithms the identified input value;
[0140] The BP neural network module is used to perform sample training on the feature vector of the input network data, and optimize the weight W of the input layer and the hidden layer in conjunction with the artificial bee colony algorithm ij and the weight W connecting th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com