Mobile social network user identity falseness identification method based on behavioral modeling
A user identity and user technology, which is applied in the field of mobile social network user identity identification, can solve the problem that the identification method is easy to be stolen and so on.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] (case)
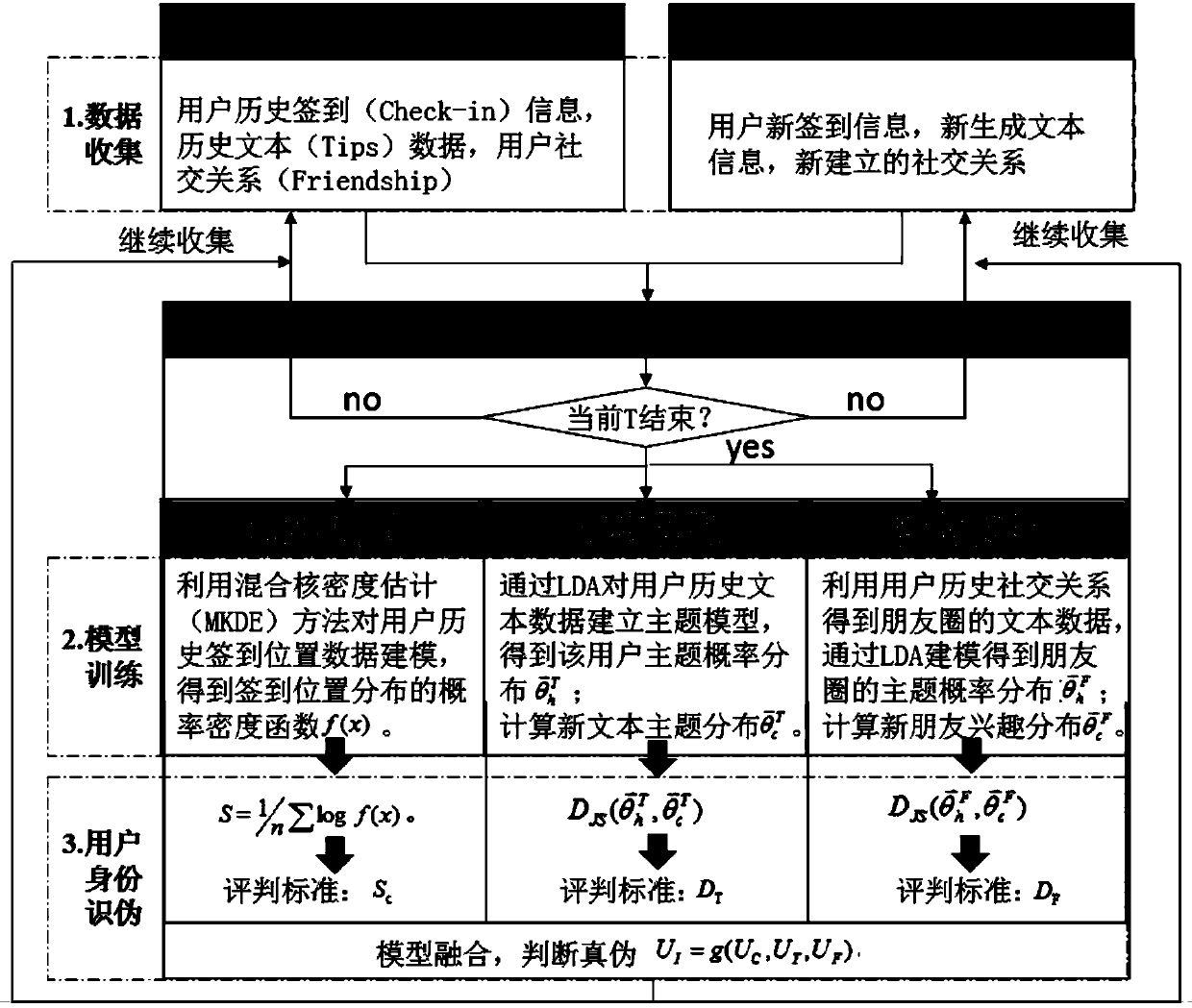
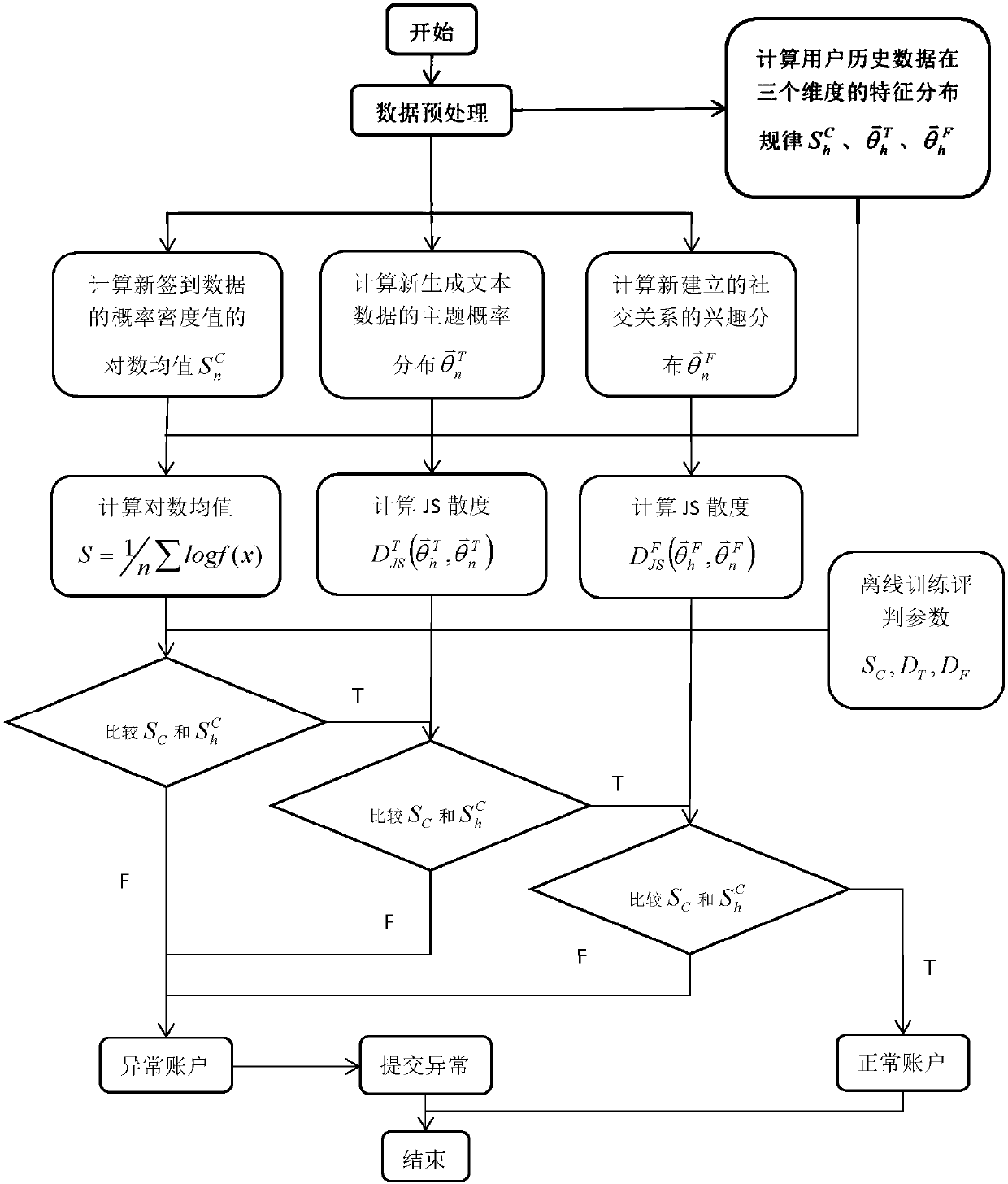
[0023] System structure diagram of mobile Internet user identification method based on behavior modeling, such as figure 1 shown. The whole program is divided into three phases:
[0024] In the first stage, a user offline model is established for historical data, which is responsible for the collection and processing of user historical data, and generates the distribution rules of user behavior characteristics of corresponding dimensions; (a conventional technology in the field)
[0025] The second stage is the online collection behavior record generation current feature stage, which is responsible for the collection and processing of the user's current data, and calculates the distribution law of the behavior characteristics of the corresponding dimension; (a conventional technology in the field)
[0026] The third stage is the user identity verification stage, which is responsible for passing the many Dimension Fusion Give a judgment on the identity of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com