OPC UA (OPC Unified Architecture) key exchange method based on chaotic RSA encryption
A secret key exchange and key technology, which is applied to secure communication through chaotic signals, public keys for secure communication, user identity/authority verification, etc. Clients request at the same time and other problems to overcome inefficiency, high security, and good prime quality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
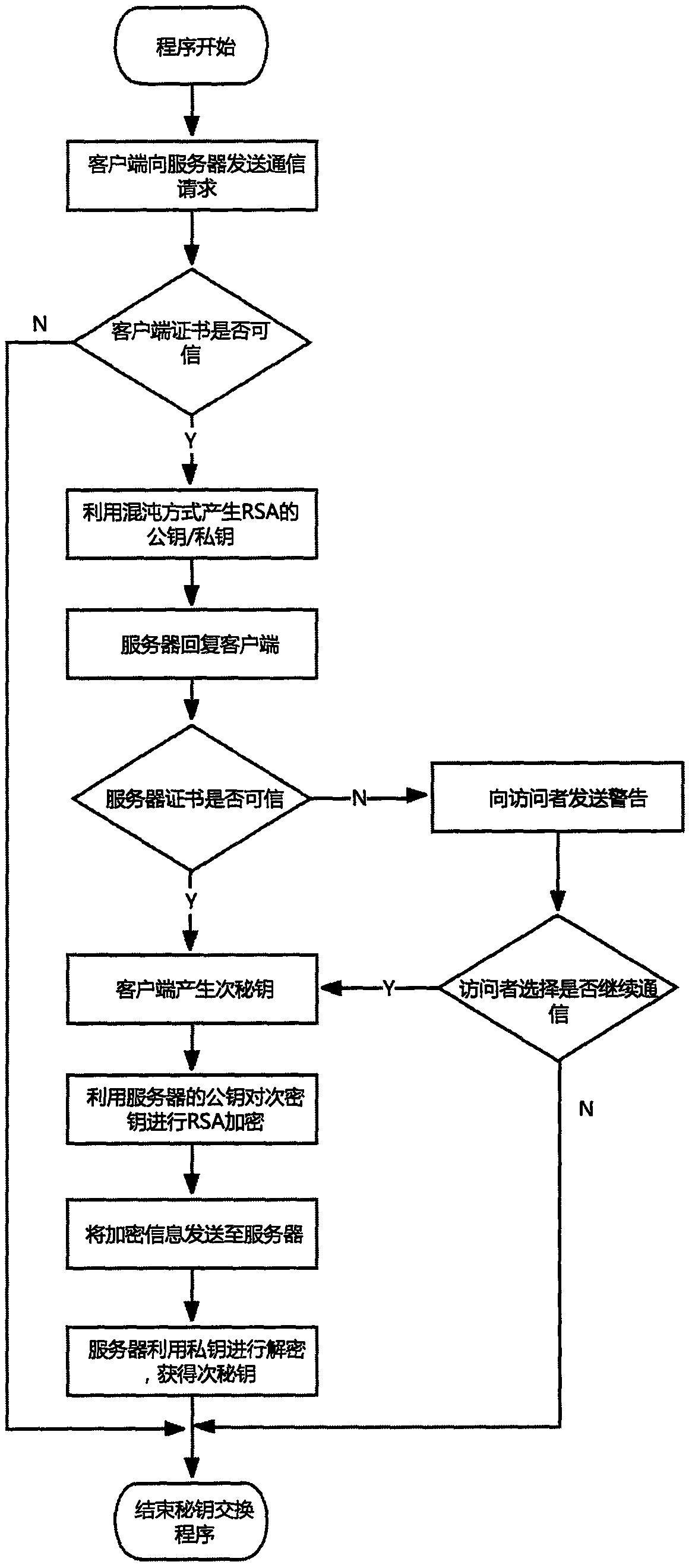
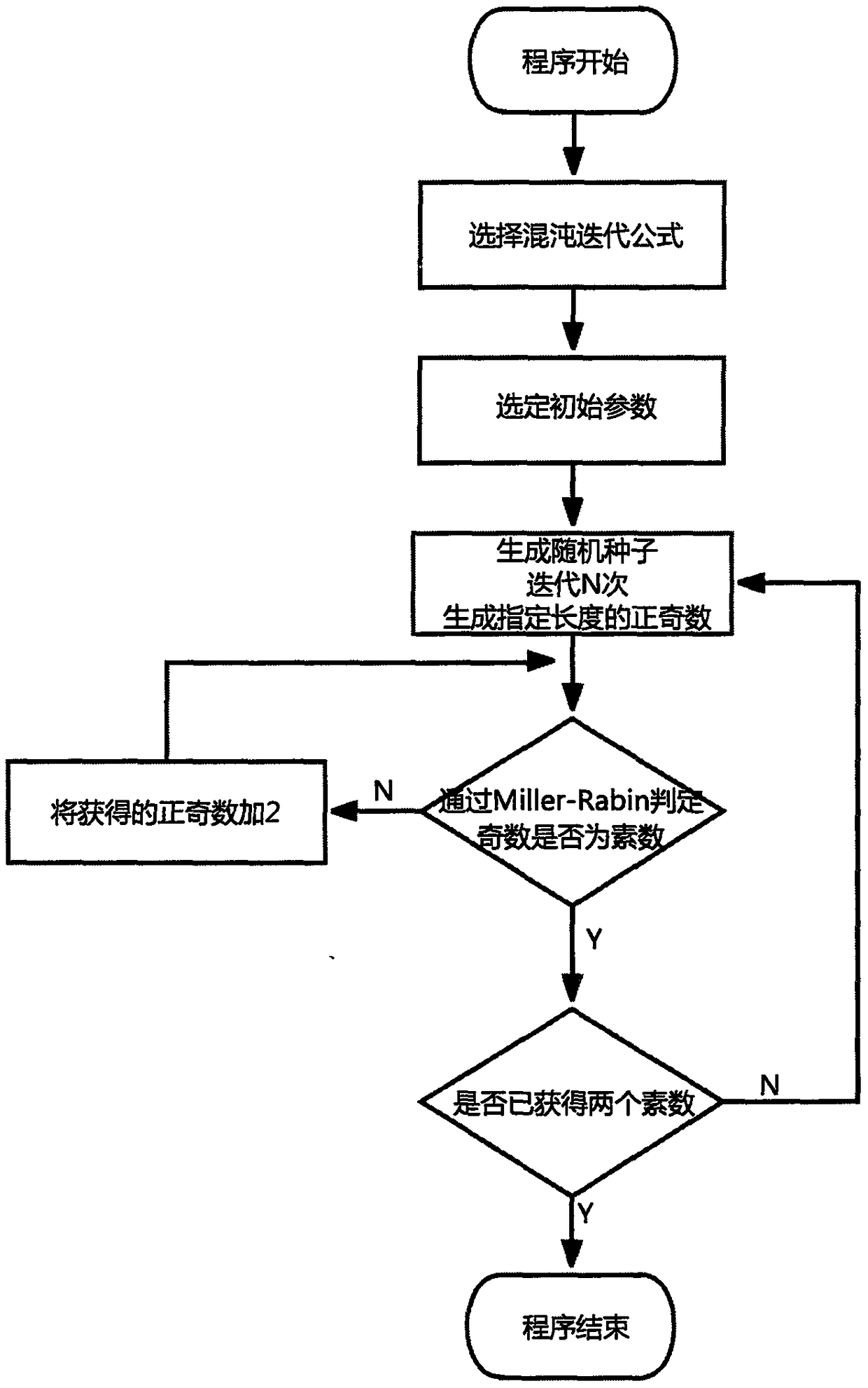
[0042] The present invention proposes an OPC UA secret key exchange method based on chaotic RSA encryption, which is characterized in that the pseudo-randomness of the chaotic sequence generates a large prime number that meets the requirements instead of the traditional RSA to generate a prime number, and then encrypts the key through RSA and sends it to the customer The key information is exchanged between the terminal and the server to realize key sharing. The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
[0043] figure 1 Provided is the flow chart of the secret key generation and secret key exchange method of the chaotic RSA based on OPC UA in the present invention, which is specifically implemented in this way:
[0044] 1. When the OPC UA client needs to communicate with the server, it first sends a communication request to the server; this request includes all the security mechanisms s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com