Cloud storage data de-duplication method supporting efficient convergence key management
A key management and cloud storage technology, applied in the fields of cloud storage data deduplication and data security outsourcing, can solve the problems of inability to resist cloud server collusion attacks, high computing and communication overhead, deceiving directory servers, etc., to save computing and Communication overhead, convenient and efficient use of keys, and effect of saving storage resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
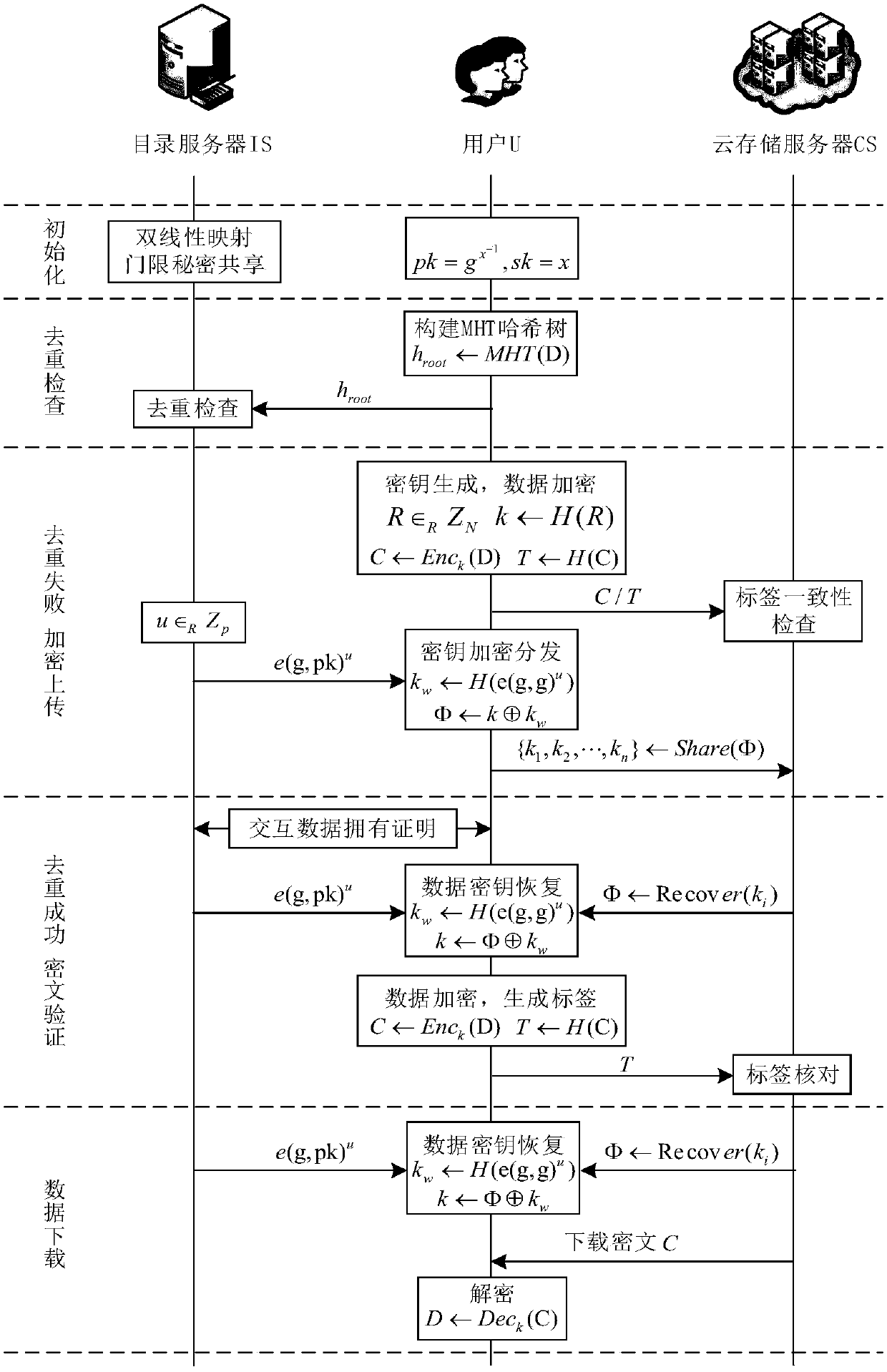
[0032] Below in conjunction with accompanying drawing and specific embodiment, the present invention is described in further detail:
[0033] The usage scenario of the present invention includes three valid entities:
[0034] Cloud Storage Server (CS): CS provides storage and computing services to users, with powerful computing capabilities and huge storage space. Generally, users will purchase storage space from cloud servers in the form of leasing, and store their own data on the cloud for future use.
[0035] Directory Server (IS): As a trusted entity, IS provides indexes for users and their data, can fairly prove data ownership, and can ensure the consistency of data, keys, and ciphertexts.
[0036] User (U): A user can be an individual or an enterprise, who has a large amount of data that needs to be stored on the cloud, and relies on the cloud for data maintenance and management and related calculations.
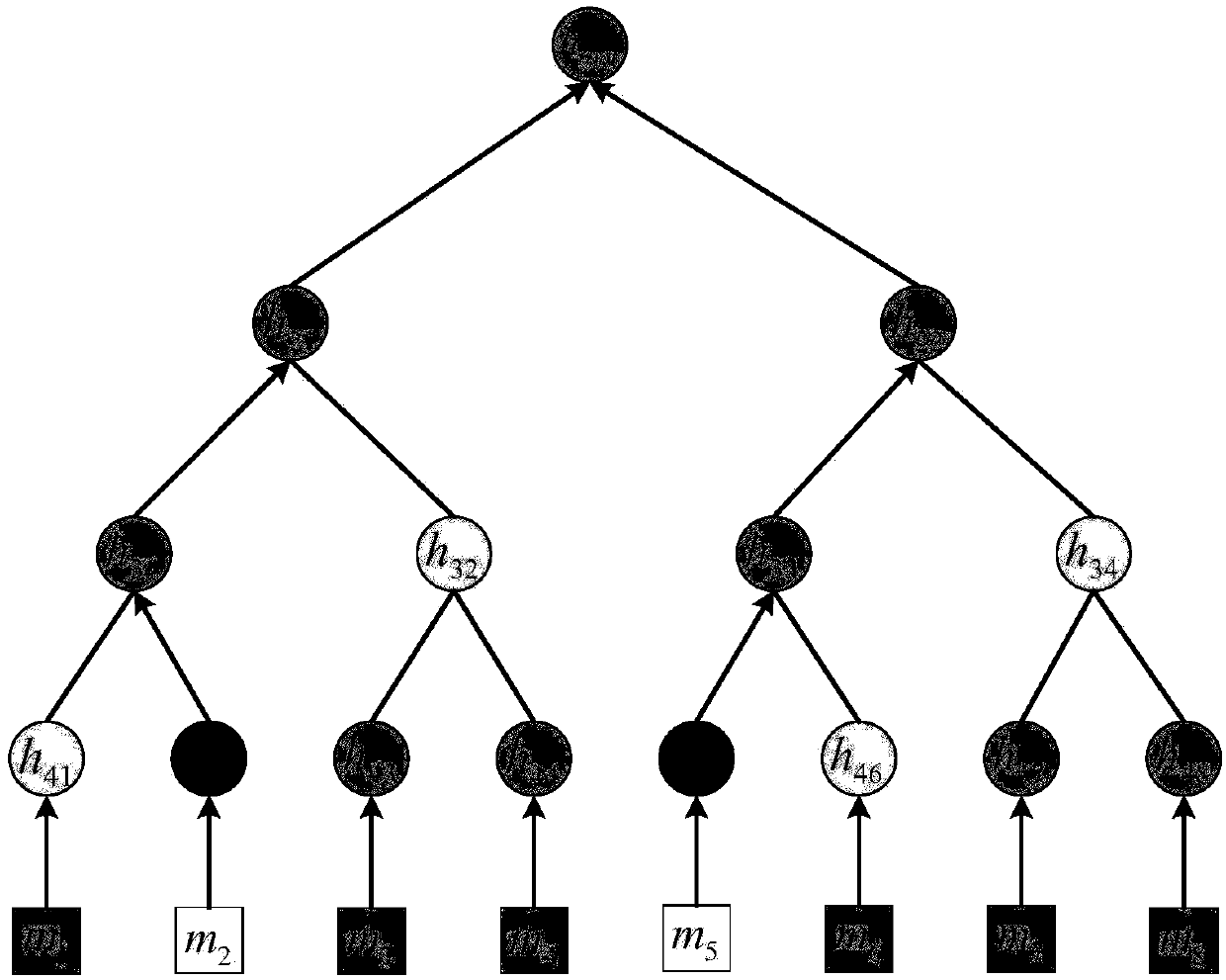
[0037] refer to figure 1 , the implementation steps of the pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com