API request encryption method, data interaction method and system
An encryption method and data interaction technology, applied in the field of communication, can solve problems such as low security factor, and achieve the effects of ensuring security, unifying data standards, and expanding access capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
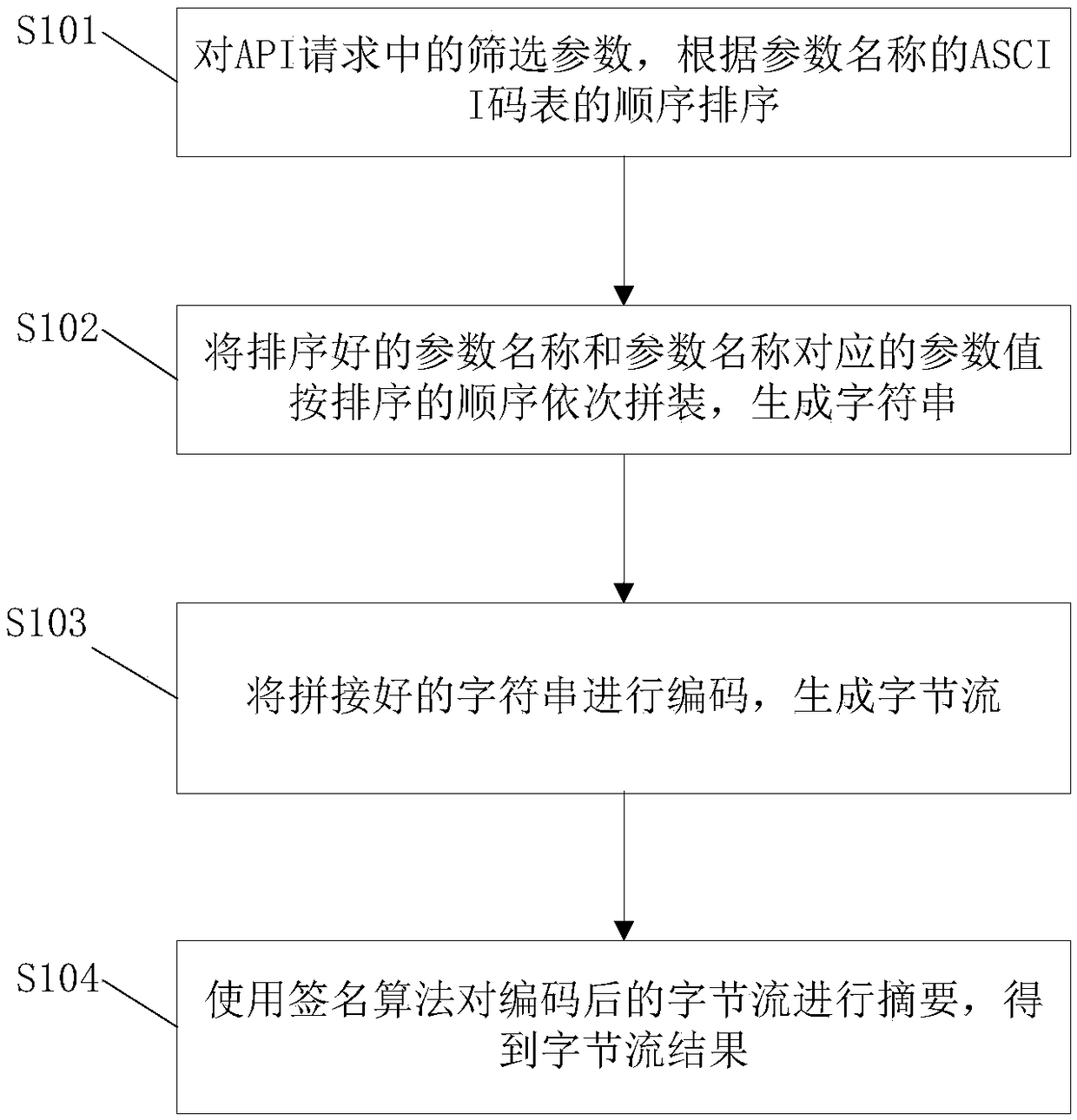
[0062] Such as figure 1 As shown, the embodiment of the present invention provides an encryption method for an API request, which is executed by an electronic device (such as a client or a server), and the method may include the following steps:
[0063] Sorting step S101: sort the screening parameters in the API request according to the order of the ASCII code list of the parameter names.
[0064] Wherein, the above-mentioned screening parameters are request parameters excluding parameters whose parameter name is sign and parameters whose parameter name is byte[].
[0065] Specifically, when encrypting, the client and the server sort the screening parameters in the API request according to the order of the ASCII code table of the parameter names.
[0066] For example: foo=1, bar=2, foo_bar=3, foobar=4 The sorted order is bar=2, foo=1, foo_bar=3, foobar=4.
[0067] Concatenation step S102: Concatenate the sorted parameter names and parameter values corresponding to the par...
Embodiment 2
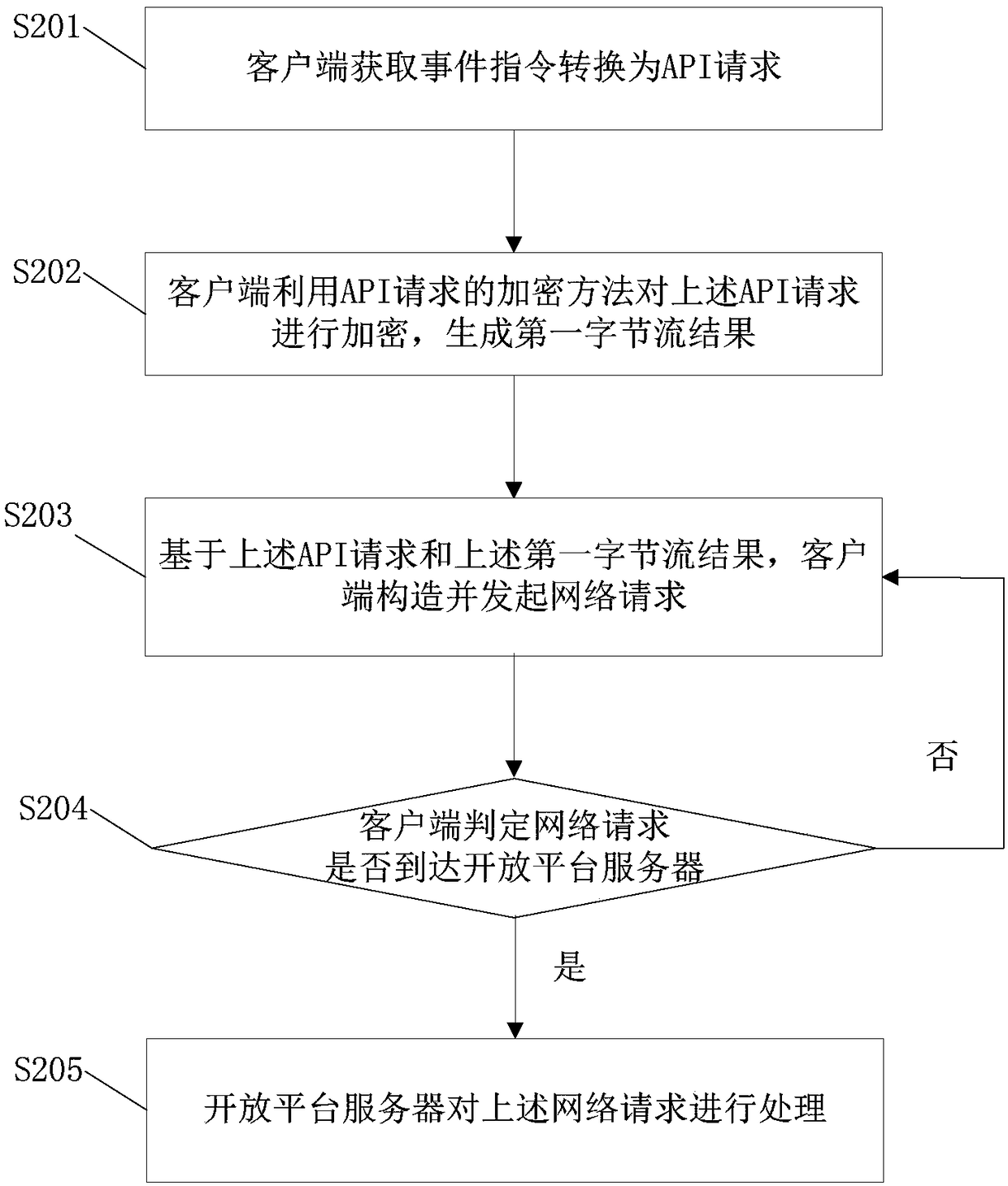
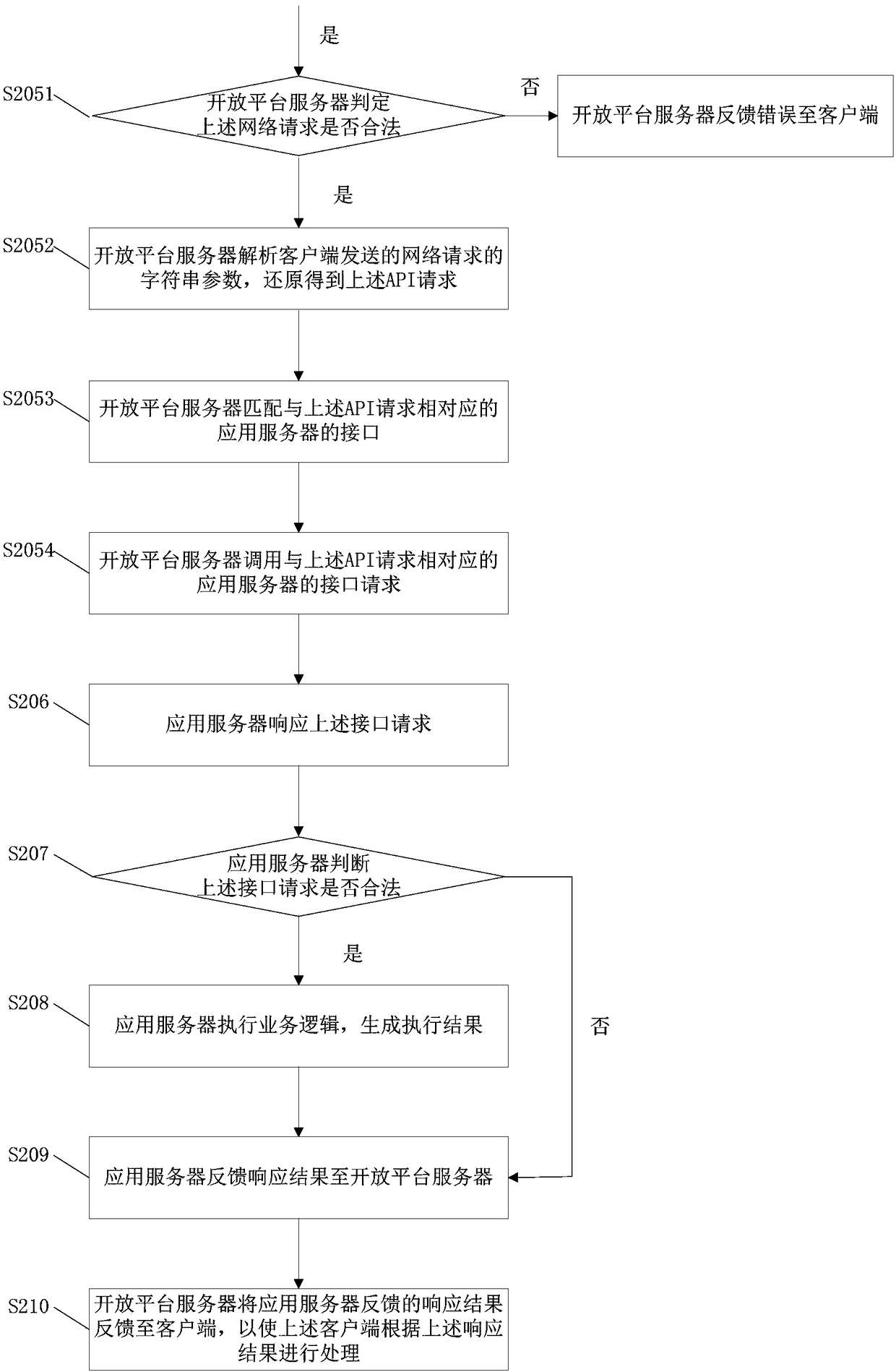
[0085] Such as figure 2 and image 3 As shown, the embodiment of the present invention provides a data interaction method, which can be applied to multi-terminal data synchronization, that is, the data interaction method can realize multi-client data synchronization.
[0086] Specifically, the data interaction method includes:
[0087] Step S201: The client acquires an event command and converts it into an API request.
[0088] Wherein, the above-mentioned event instruction includes an event instruction manually triggered and / or an event instruction automatically triggered by a client hardware device; the above-mentioned API call request is used to initiate a call request of an open platform, and the above-mentioned API request includes public parameters and service parameters.
[0089] Specifically, the hardware system where the client is located will generate system events by means of automatic triggering or manual operation. Through the triggering of hardware system eve...
Embodiment 4
[0166] Such as Figure 4 As shown, the data interaction system in the prior art includes dubbo server cluster, tomcat cluster, registration center cluster and redis cluster, wherein, dubbo server cluster and tomcat cluster can be dynamically expanded, and the registration center cluster provides registration and consumption between services Redis clusters provide data caches with higher access performance than traditional databases. When a user visits a site, they reach the corresponding server cluster through the reverse proxy, and one of the servers responds and sends the information back to the user's terminal PC. Although the data interaction system in the prior art can solve the computing power of the server under high concurrency, in the current business model, various terminals are no longer limited to smart terminals such as PCs and mobile phones. In fact, such a technical solution has not been able to provide effective support.
[0167] Aiming at the problems caused...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com