Remote distribution method for terminal master key and system thereof
A terminal master key and distribution system technology, which is applied to the remote distribution method and system field of terminal master key, can solve the problems of cumbersome process, high operation and maintenance cost, etc., and achieves the effect of reducing labor cost and improving the speed of business expansion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
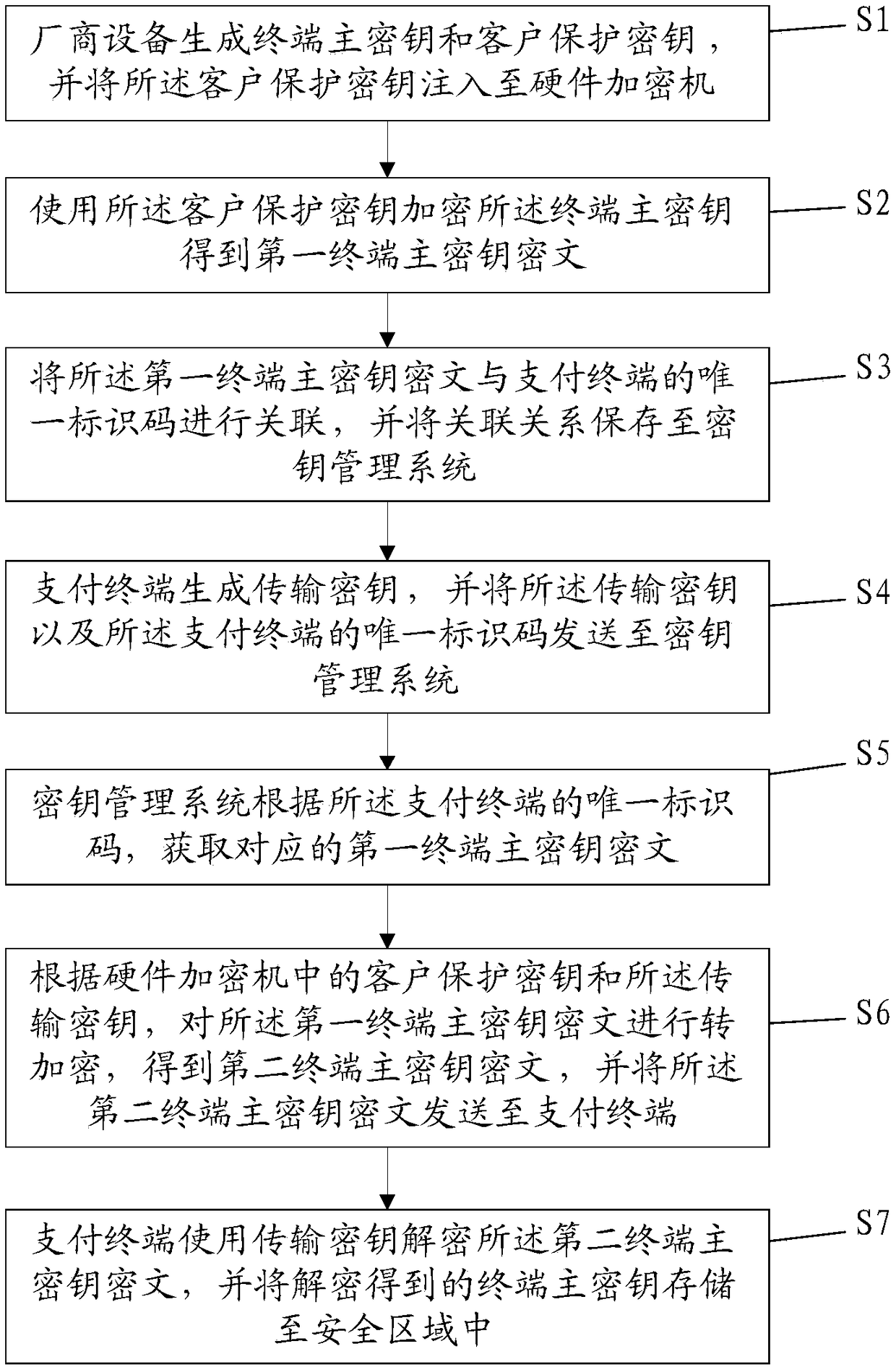
[0109] Please refer to figure 1 , Embodiment 1 of the present invention is: a method for remotely distributing terminal master keys, which can complete the remote distribution of terminal master keys during the generation phase, and is applicable to any type of financial terminal equipment, such as POS machines, ATMs Wait. Before carrying out this method, it is necessary to build a key management system ZKMS, which is equivalent to the role of the key master POS, and completes the key distribution to the sub-POS that leaves the factory. The method comprises the steps of:
[0110] S1: The manufacturer's device generates the terminal master key and customer protection key, and injects the customer protection key into the hardware encryption machine; specifically, before the payment terminal is produced, the payment manufacturer's device randomly generates the terminal master key TMK and the customer protection key. key CPK, and inject the customer protection key CPK into the h...
Embodiment 2
[0121] This embodiment is a further extension of Embodiment 1, and the similarities will not be repeated. The difference is that before step S4, that is, before the payment terminal sends the transmission key to the key management system ZKMS, the hardware encryption machine generates an asymmetric key Yes, including the public key of the production line and the private key of the production line, and then send the public key of the production line to the payment terminal through a digital certificate, that is, the digital certificate including the public key of the production line can be sent to the payment terminal, and the payment terminal will check the digital certificate After verification, obtain the public key of the production line.
[0122] When the payment terminal sends the transmission key to the key management system ZKMS, that is, in step S4, the payment terminal uses the production line public key to encrypt the transmission key and the unique identification cod...
Embodiment 3
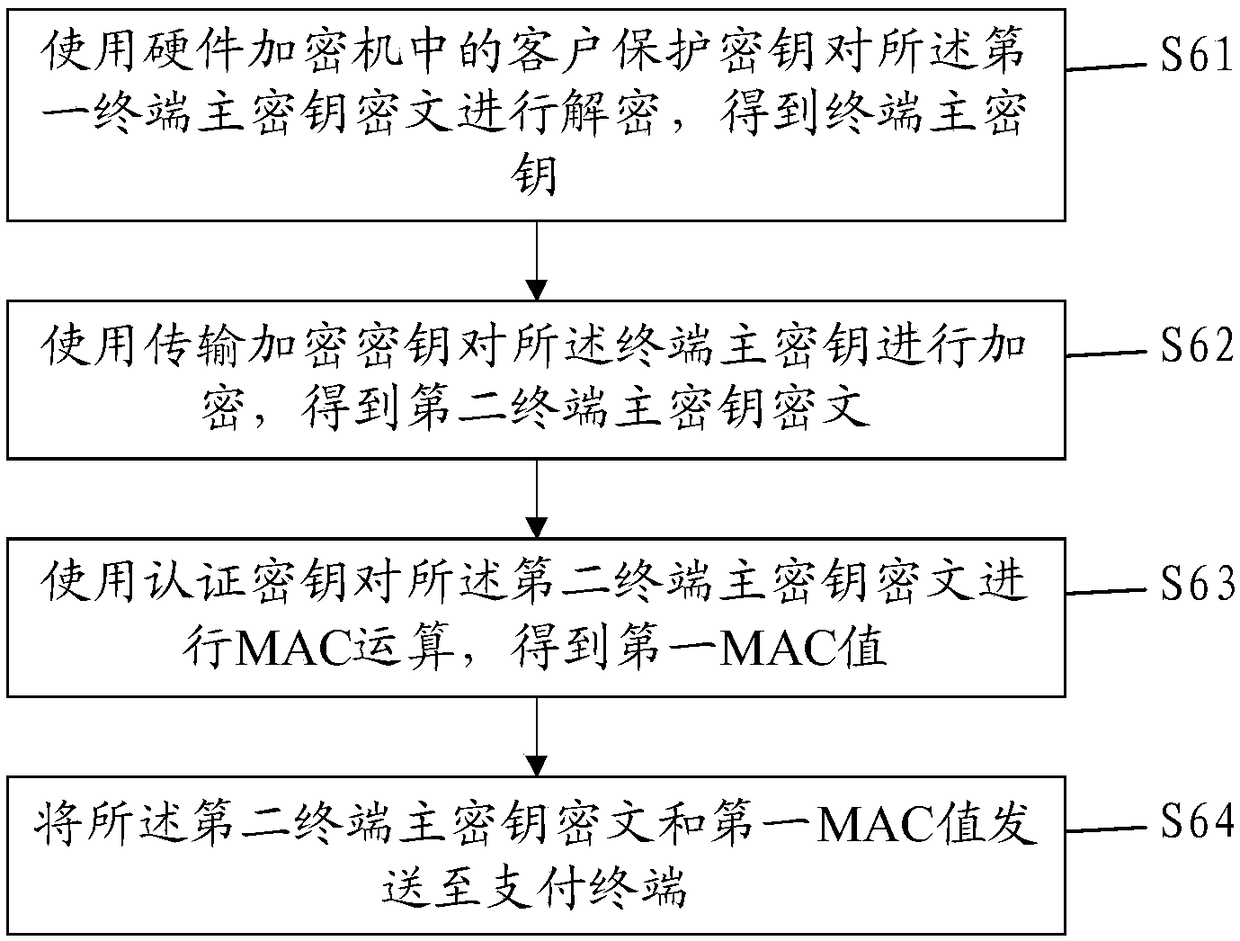
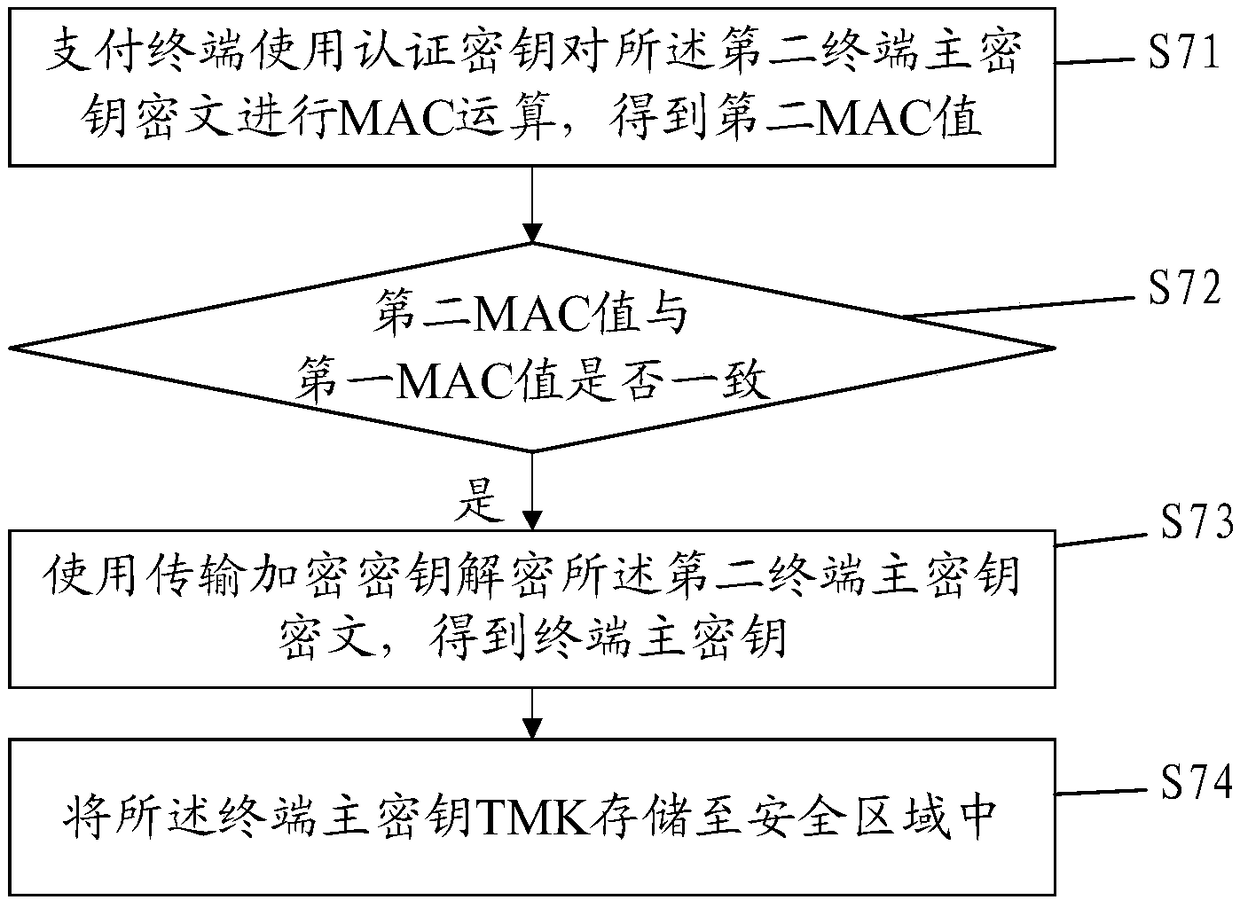
[0125] Please refer to Figure 2-3 , this embodiment is a further extension of steps S6 and S7 in the first embodiment.
[0126] In this embodiment, the transmission key TK includes a transmission encryption key TK-TEK and an authentication key TK-AUK.
[0127] Such as figure 2 As shown, step S6 includes the following steps:
[0128] S61: Use the customer protection key CPK in the hardware encryption machine to decrypt the ciphertext of the first terminal master key to obtain the terminal master key TMK;
[0129] S62: Use the transmission encryption key TK-TEK to encrypt the terminal master key TMK to obtain a second terminal master key ciphertext;
[0130] S63: Use the authentication key TK-AUK to perform a MAC operation on the ciphertext of the second terminal master key to obtain a first MAC value;
[0131] S64: Send the second terminal master key ciphertext and the first MAC value to the payment terminal.
[0132] Such as image 3 As shown, step S7 includes the foll...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com