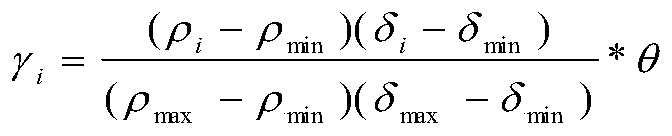A method of intrusion detection for android platform based on cfsfdp clustering
An intrusion detection and clustering technology, applied in the field of network information security, can solve the problems of occupying system resources, large differences in detection performance of different methods, lack of unknown attack detection capabilities, etc., to achieve accurate feature models, reduce computational complexity, reduce The effect of storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with accompanying drawings and implementation.
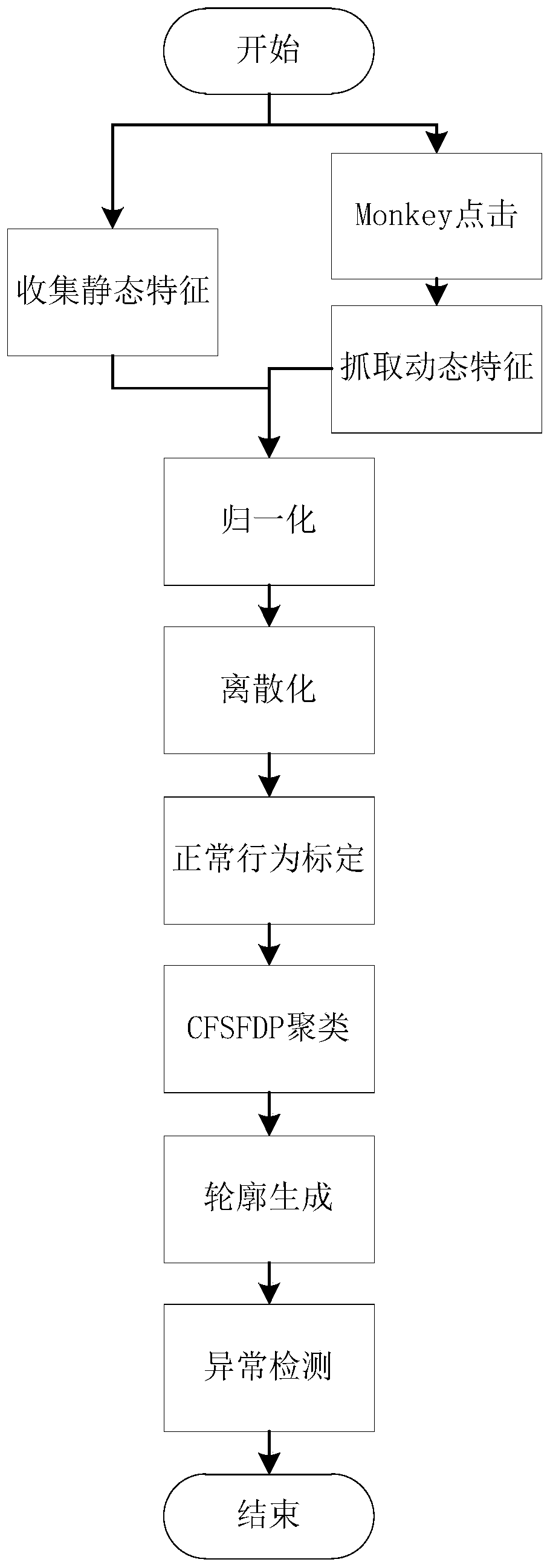
[0032] Such as figure 1 As shown, the present embodiment provides a method for Android platform intrusion detection based on CFSFDP clustering, which specifically includes the following steps:
[0033] Step 1: Collect and capture the static and dynamic features of the Android platform. Static features include permissions, Intent-filter, Java Code, etc., and dynamic features include System Call, Network Traffic, System Component, and user behavior. Static feature data is collected in a longer time span, and dynamic feature data is time-shared in a shorter time span;
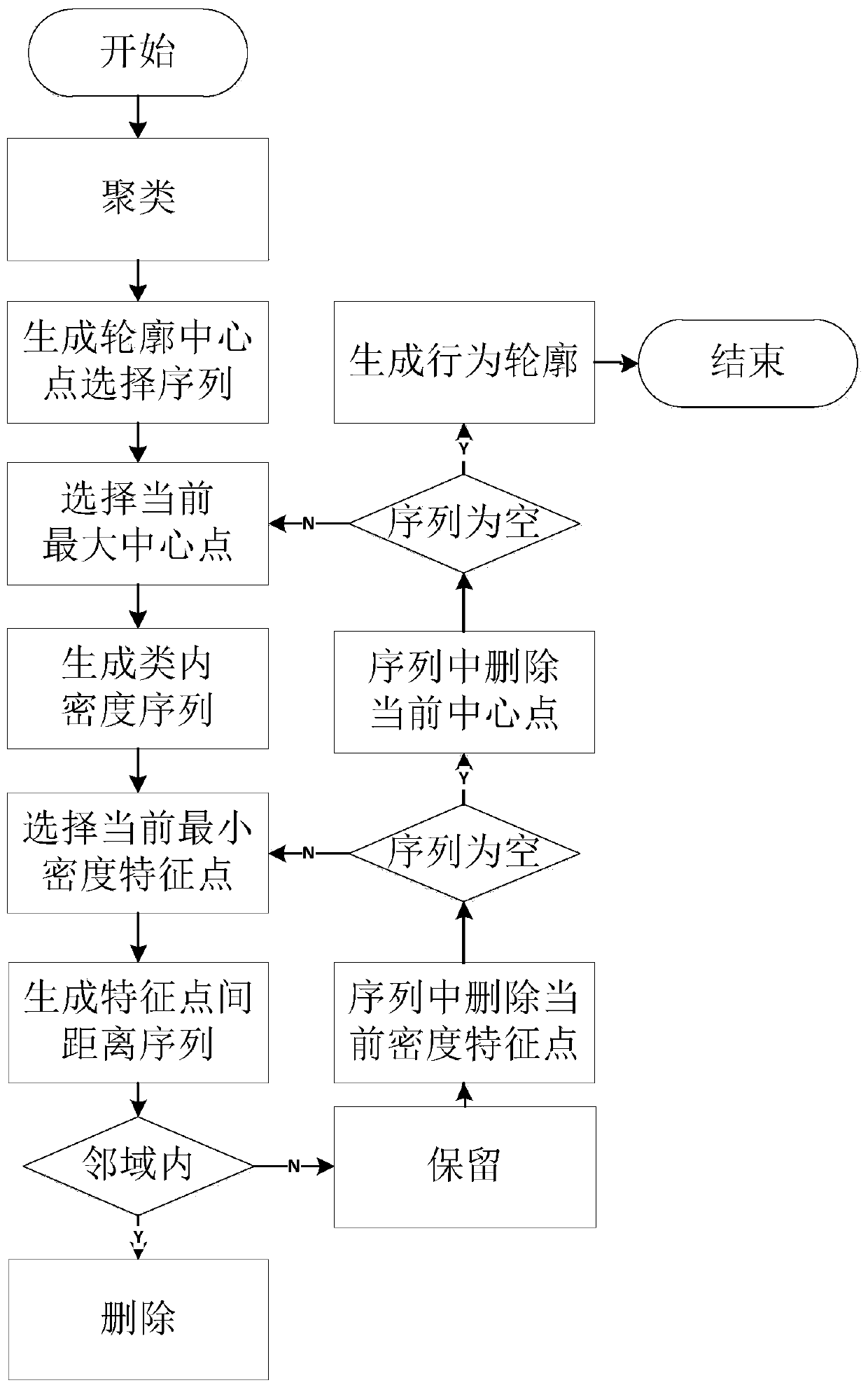
[0034] Step 2: Normalize and discretize the feature data, obtain the normal behavior feature data, and calibrate the normal feature data. We use the robot monkey program to click on the native Android system and record its behavior. This part of the behavior is collected in a virus-free a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com