A method and system for user identity authentication based on mobile equipment
A user identity authentication, mobile device technology, applied in digital data authentication, neural learning methods, instruments, etc., can solve the problems of not being able to mass-produce smart devices, permanently unproven, and difficult to miniaturize products, so as to improve user experience. , The effect of realizing data privacy protection and simplifying the process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The preferred embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
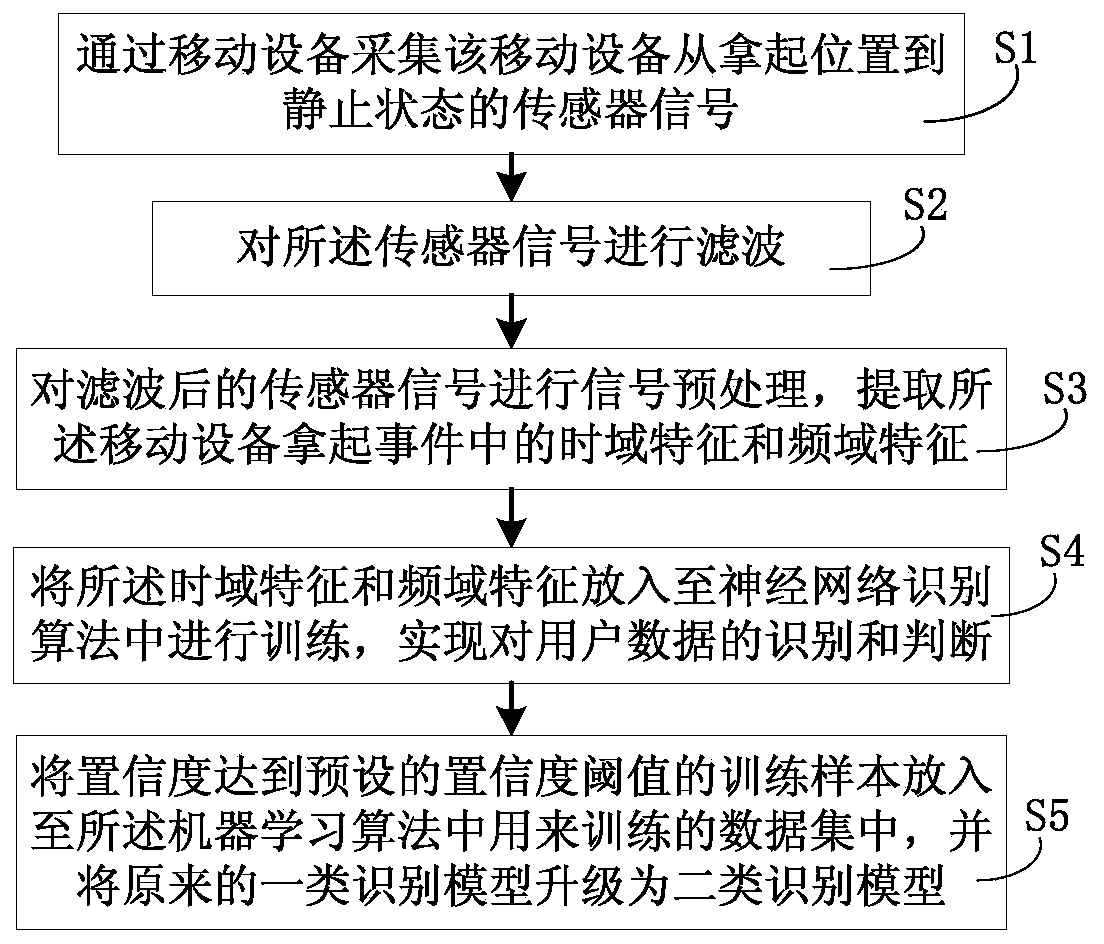
[0030] Such as figure 1 As shown, this example provides a mobile device-based user identity authentication method, including the following steps:
[0031] Step S1, collecting the sensor signal of the mobile device from the pick-up position to the static state through the mobile device;
[0032] Step S2, filtering the sensor signal;
[0033] Step S3, performing signal preprocessing on the filtered sensor signal, and extracting time-domain features and frequency-domain features in the event of picking up the mobile device;
[0034] In step S4, the time-domain features and frequency-domain features are put into a neural network identification algorithm for training, so as to realize identification and judgment of user data.
[0035] The mobile devices mentioned in this example refer to existing mobile smart devices, including smar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com