A Lightweight Identity Authentication and Platform Identification Evaluation Method
An identity authentication and lightweight technology, applied in the direction of encryption devices with shift registers/memory, electrical components, security devices, etc., can solve the problems of high network quality and terminal platform computing capabilities, frequent TCA protocol communication, and implementation Difficulty and other issues, to achieve the effect of enhancing confidentiality and resisting replay attacks, reducing the number of network data exchanges and reducing computing load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
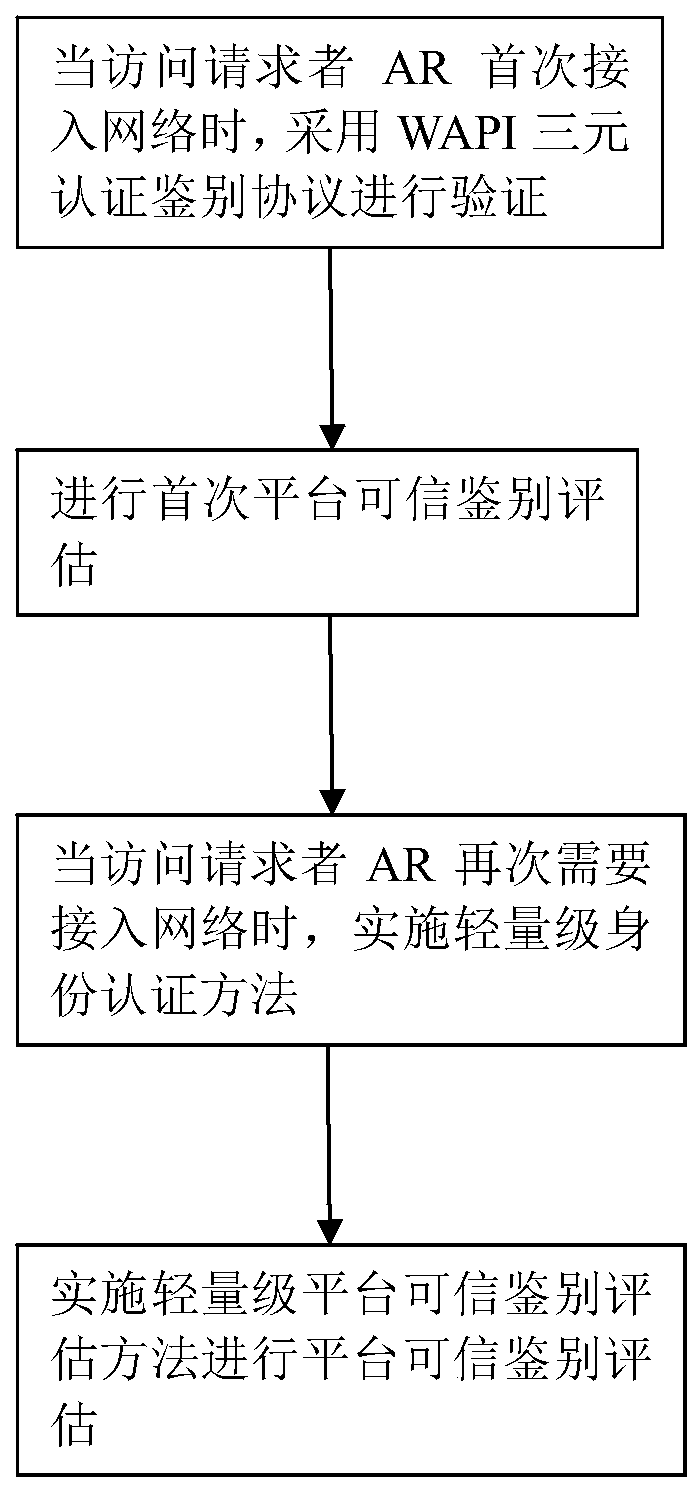
[0039] Such as figure 1 As shown, the present invention provides a lightweight identity authentication and platform identification evaluation method, comprising the following steps:
[0040] Step 1, when the access requester AR accesses the network for the first time, the identity authentication protocol between the access requester AR and the access controller AC adopts WAPI (WLAN Authentication and Privacy Infrastructure) three-element authentication protocol, and is verified by the policy manager PM The platform identity certificate and private key signature of the access requester AR and the access controller AC, confirm the platform identity, and return the verification result. If the verification is passed, go to step 2, otherwise, re-verify;
[0041] Step 2: Carry out the first platform credible authentication evaluation, if the evaluation is su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com