Identity authentication method for IoT devices based on physical unclonable functions
An Internet of Things device and identity authentication technology, which is applied in the field of Internet of Things device identity authentication, can solve complex Internet of Things security issues and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
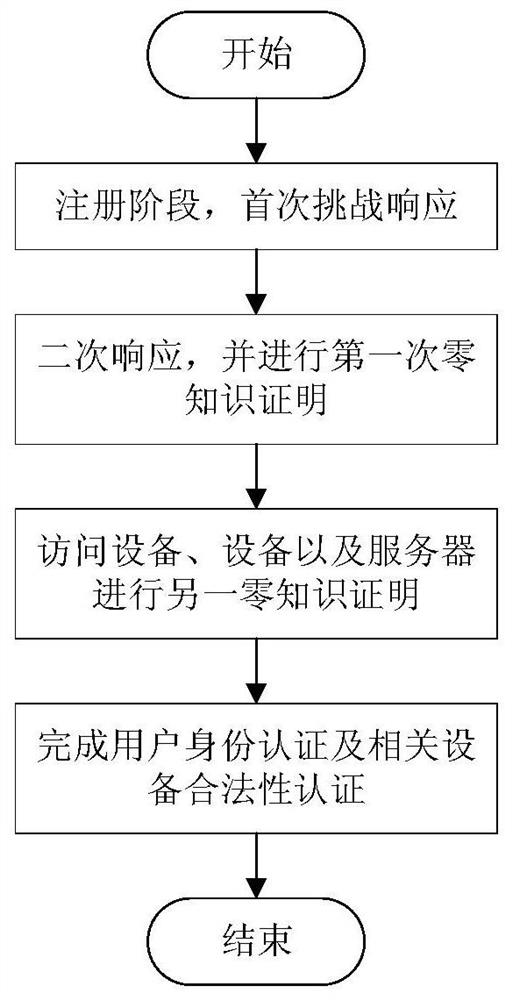
[0045] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
[0046] 1. PUF model
[0047] (1) PUF prediction and response game
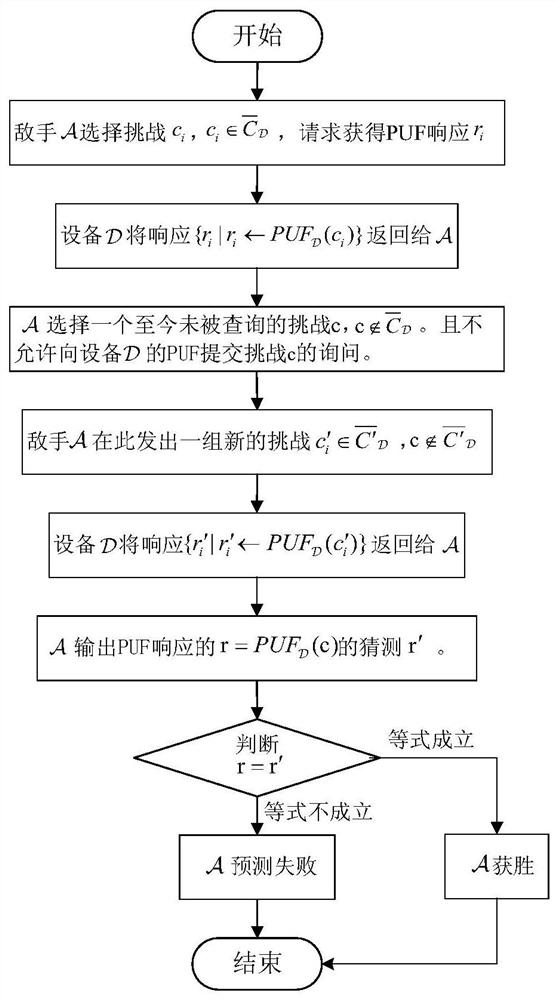
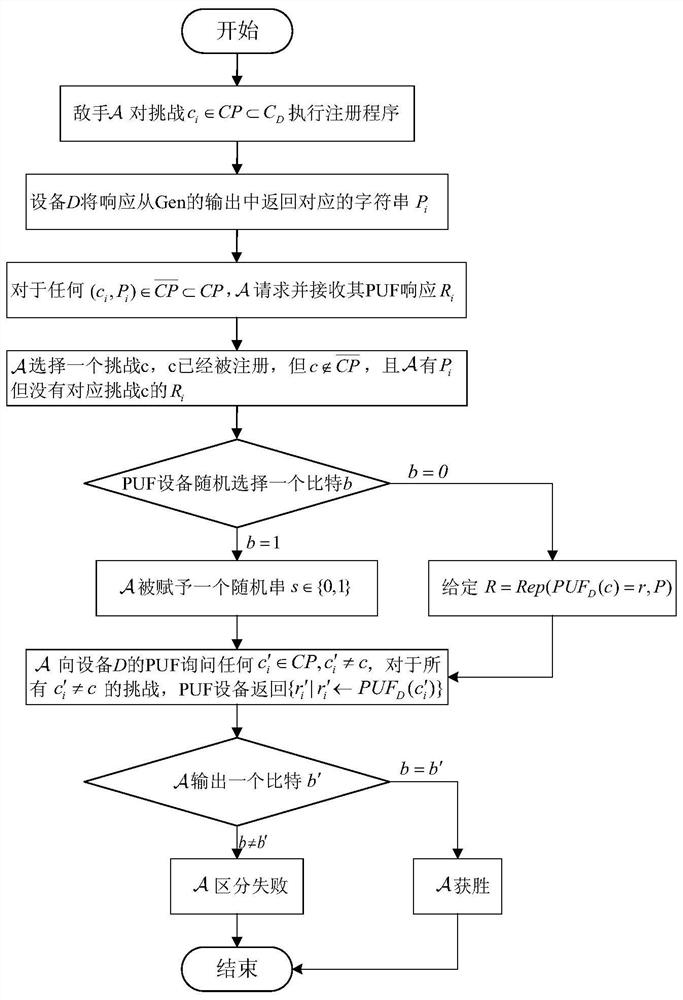
[0048] As in previous PUF literature, we made a standard assumption that without a physical device, the behavior of PUFs is unpredictable. Order U κ means from {0,1} κ A randomly selected set of strings. Let PUF be a function at length κ 1 Generates a length κ on the input 2 of skewers. Before giving the definition, let us first define the following PUF prediction response game (as figure 2 ):
[0049] Phase 1: Adversary c for any choice i , where challenge set is all challenge spaces A proper subset of , the request gets the PUF response r i .
[0050] Phase 2: PUF device will respond return to
[0051] Phase Three - Challenges: Choose a challenge c that has not been queried so far, i.e. Devices not allowed The PUF submits a query to challeng...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com