Network behavior characteristic clustering analysis-based malicious code detection method
A malicious code detection and cluster analysis technology, applied in the field of malicious code detection, can solve problems such as dependence and unsatisfactory accuracy of detection efficiency, and achieve the effect of solving too time-consuming
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
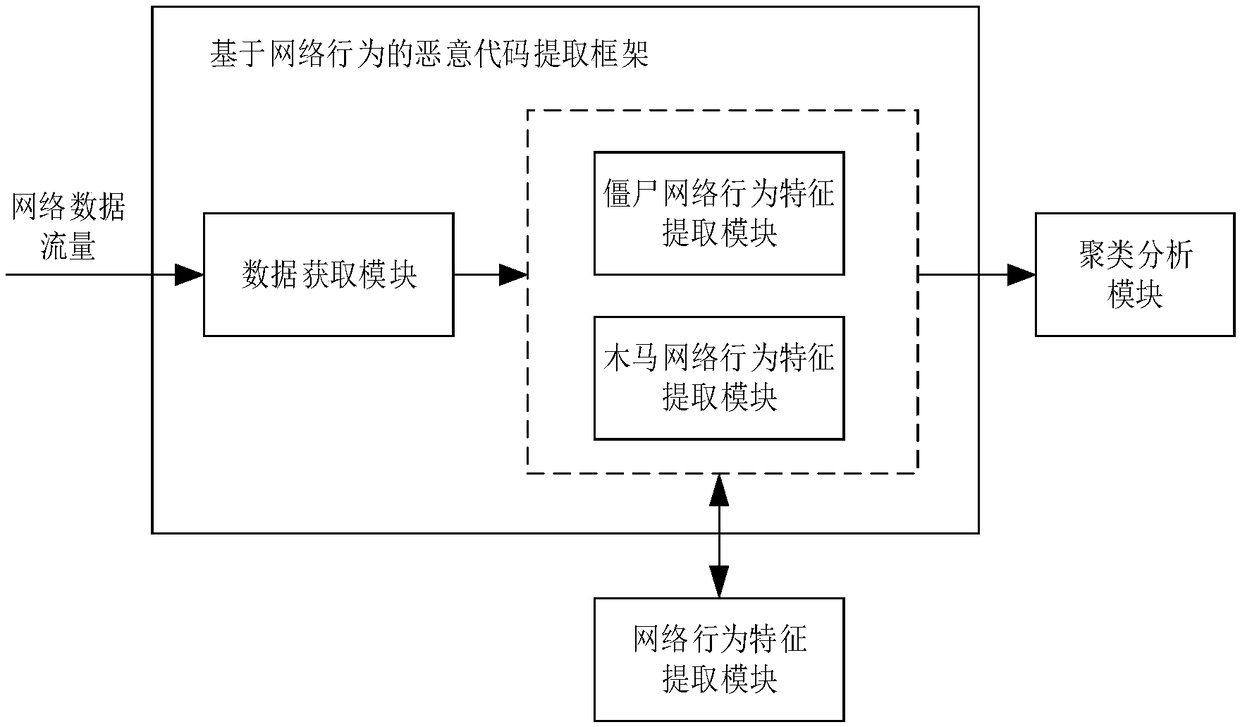
[0045] The malicious code detection method based on network behavior feature cluster analysis of the present invention specifically comprises the following steps:
[0046] Step 1. Feature analysis
[0047] Step 2. Feature extraction
[0048] Step 3, cluster analysis
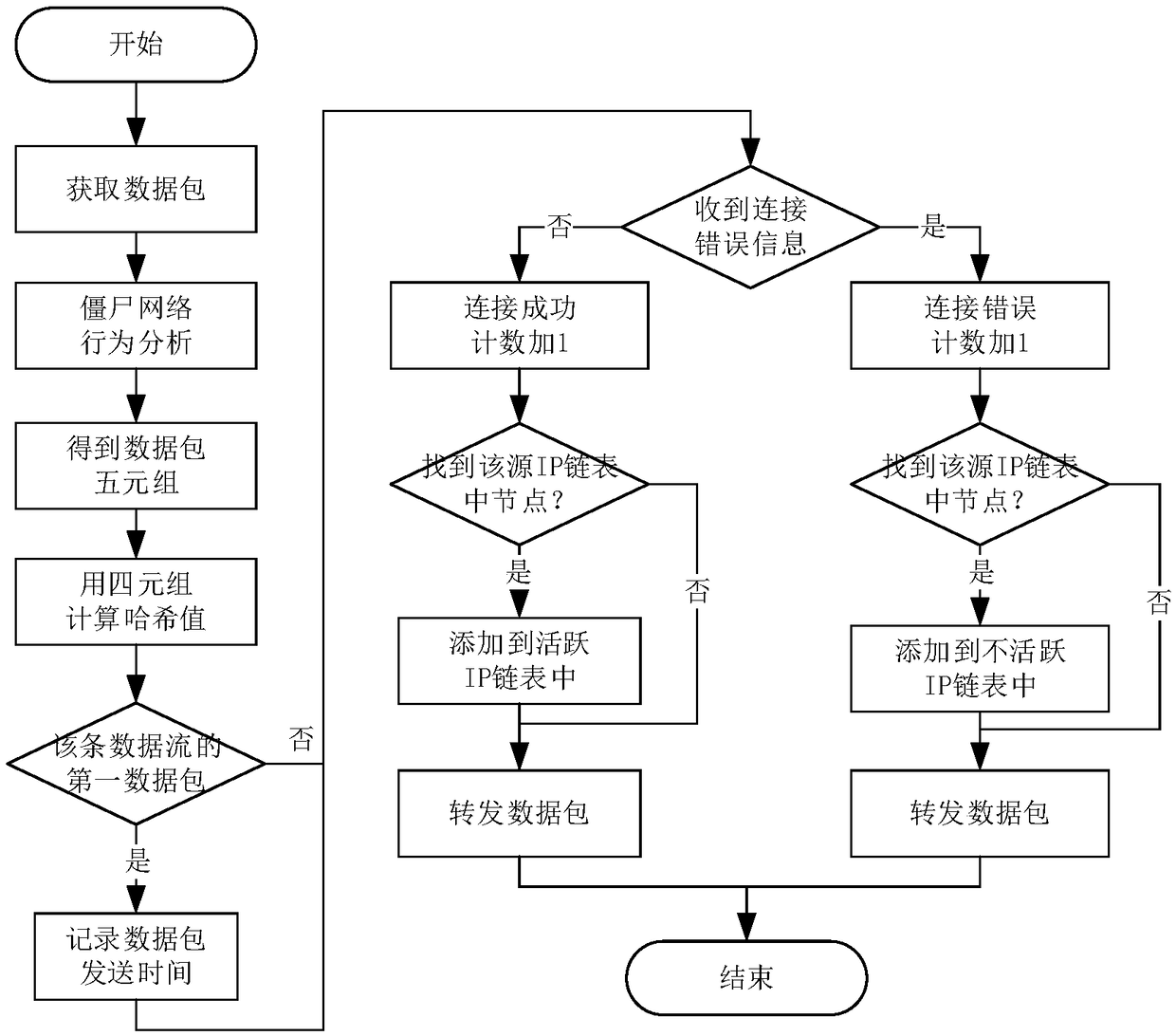
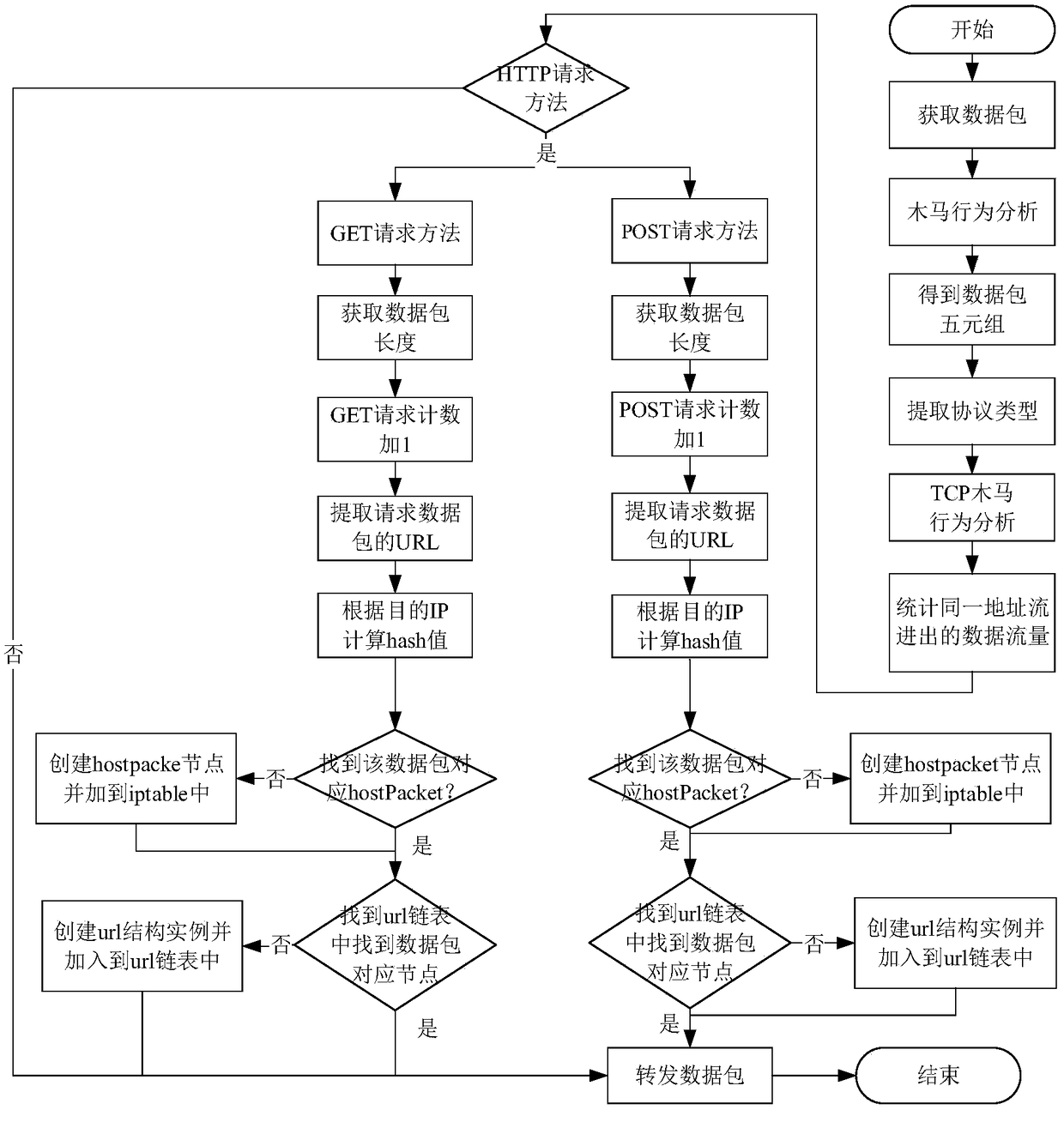
[0049] 1. The present invention is mainly aimed at analyzing the network behavior characteristics of botnets and Trojan horses.
[0050] (1) Active Behavior
[0051] Behavior of active connections and long-term communication with all suspicious servers (eg: unknown hosts). For suspiciously active connections from external network IP addresses to local area network IP addresses, it can be described by three characteristic values, including active time, active ratio and active weight. This network behavior reflects the behavior of long-term communication behavior with all suspicious external hosts. Therefore, these three characteristic values belong to the active behavior characteristics.
[0052] (2) Failu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com