Network security protection method and network security protection device
A network security and protection device technology, applied in the field of network security, can solve problems such as stealing information and weak security, and achieve the effect of improving network security and avoiding the leakage of private information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
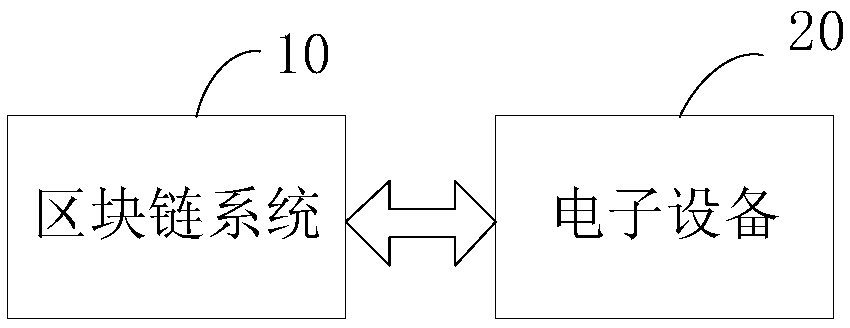
[0055] Please refer to figure 1 , is a schematic diagram of the interaction between the blockchain system 10 and the electronic device 20 provided by the embodiment of the present invention. The blockchain system 10 provided by the present invention and the electronic device 20 can establish a communication connection through a network for data interaction. The network can be, but is not limited to, a wired network or a wireless network. In this embodiment, the block chain system 10 can be used to identify and judge whether the file (including the installation file of the application program) to be downloaded by the electronic device 20 is safe, and only push the file to be downloaded to the electronic device 20 when the file is safe. To prevent the Trojan virus from being implanted into the files to be downloaded, thereby improving the network security of the electronic device 20 .
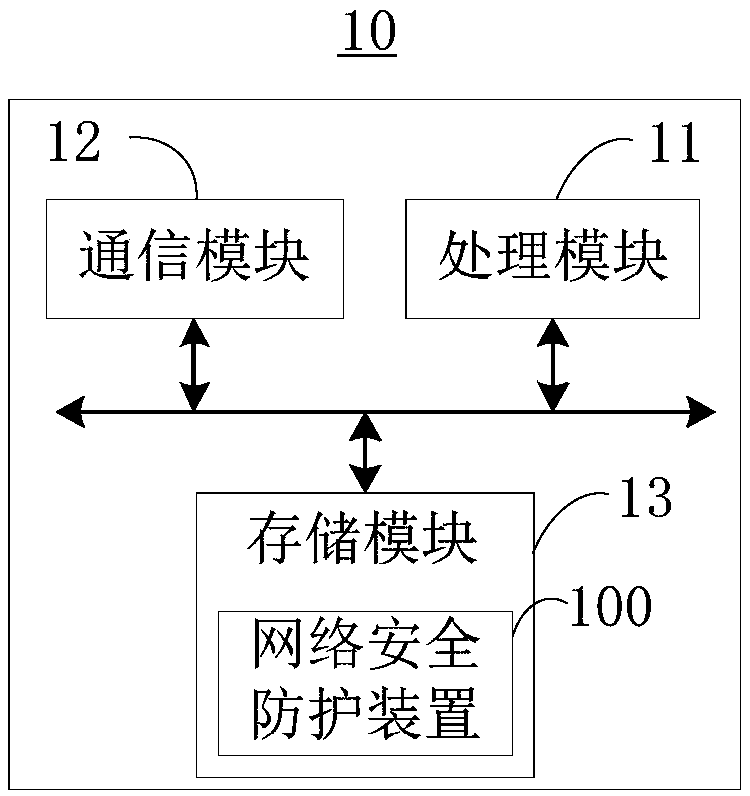
[0056] Please refer to figure 2 , is a schematic block diagram of the blockchain system 1...
no. 2 example
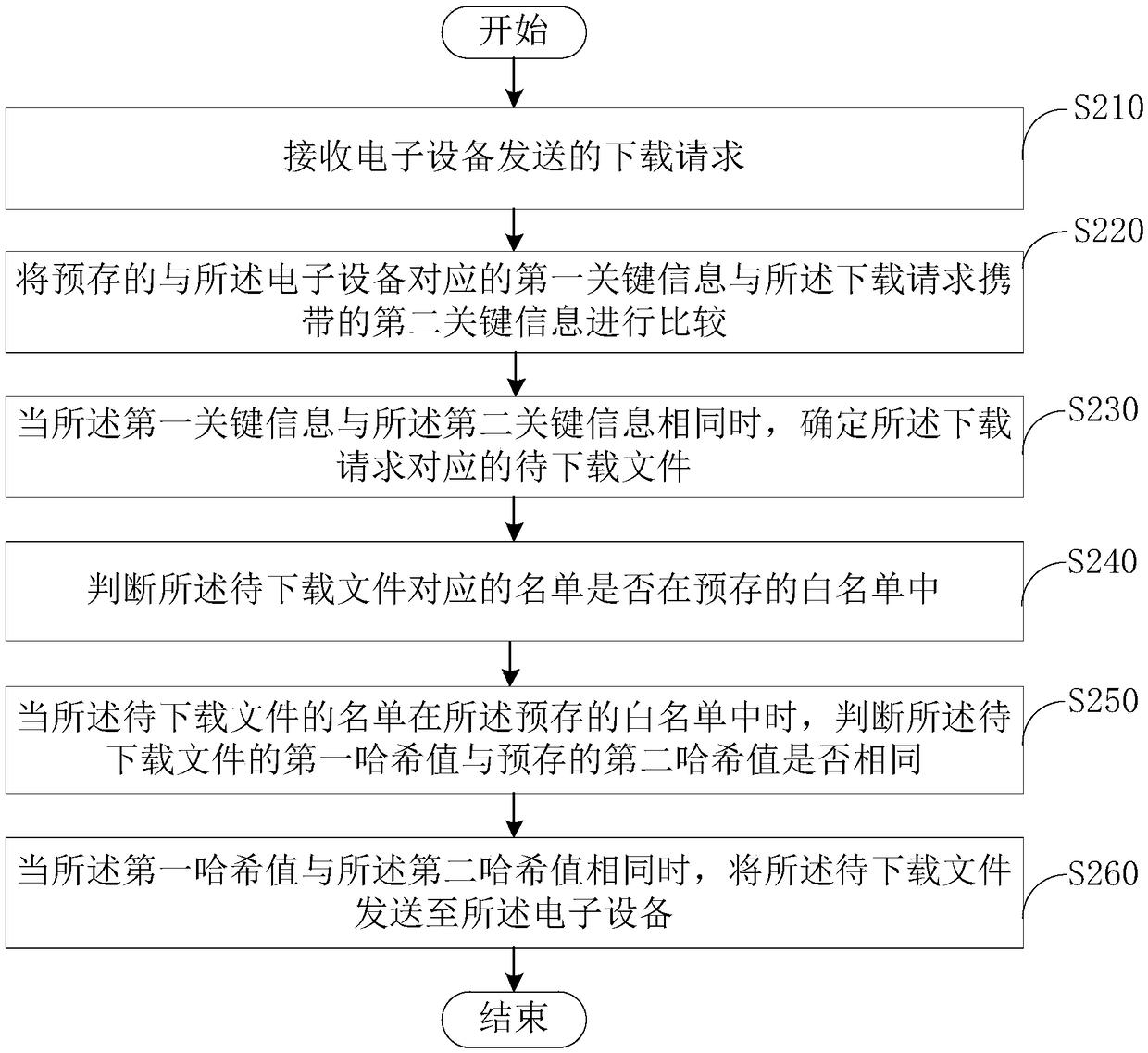
[0089] Please refer to Figure 4 , is the second schematic flowchart of the network security protection method provided by the embodiment of the present invention. The network security protection method provided in the second embodiment can be applied to the above-mentioned electronic device 20 , and the electronic device 20 executes each step of the network security protection method, so as to improve the network security of the electronic device 20 .
[0090] In the second embodiment, the network security protection method may include the following steps:
[0091] Step S310, sending a download request to the block chain system 10;
[0092] Step S320, receiving the file to be downloaded corresponding to the download request sent by the blockchain system 10, wherein the file to be downloaded is certified by the blockchain system 10 and encrypted according to preset encryption rules The file, wherein, the file to be downloaded includes an application program;
[0093] Step S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com