Malicious code homologous judgment method based on deep learning
A malicious code, deep learning technology, applied in the field of Internet information security, can solve problems such as no description or report found, and data not yet collected, to achieve the effect of system automation and improved accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
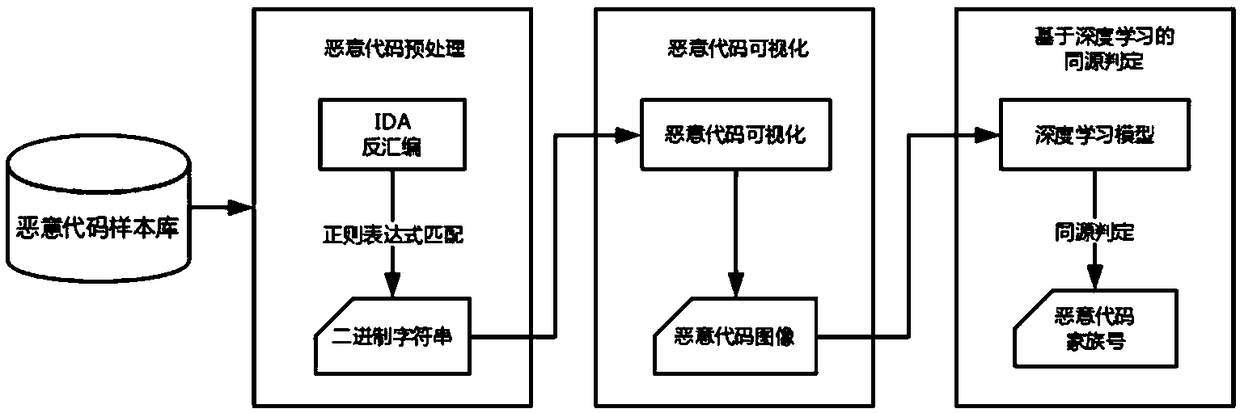
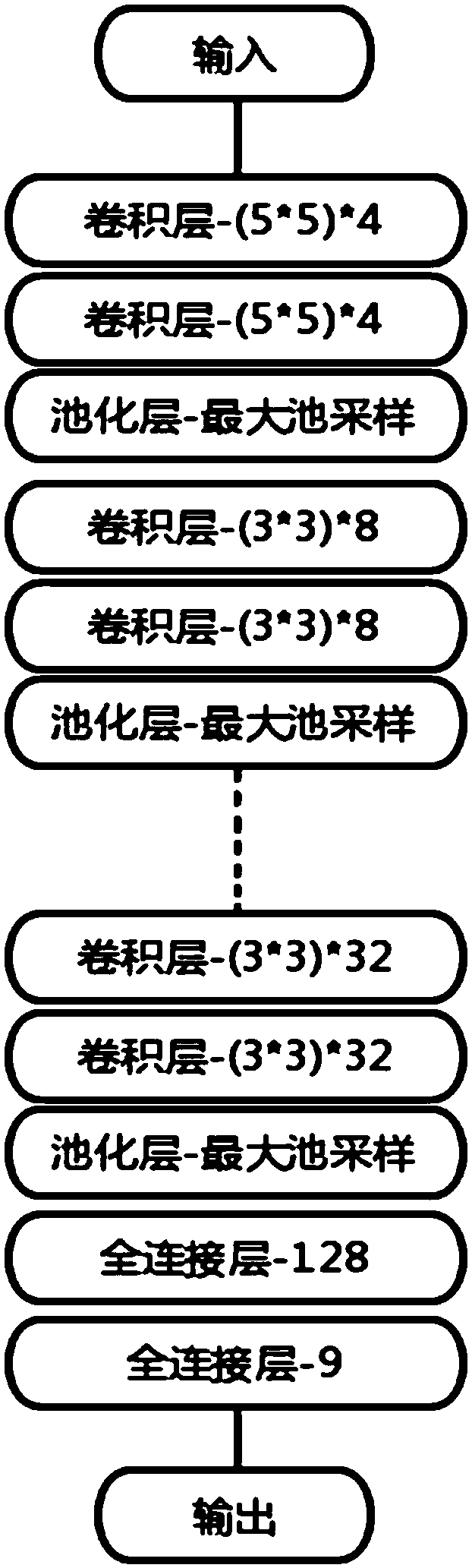
[0035] This embodiment provides a method for judging the same source of malicious code based on deep learning, including the following steps:
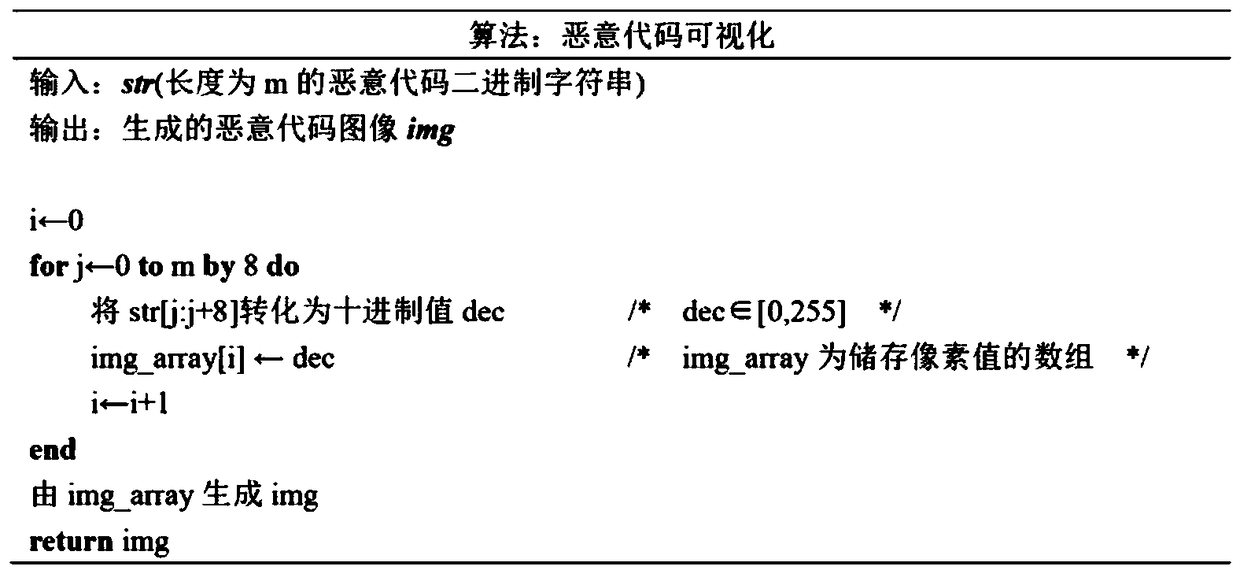
[0036] Step 1: Malicious code preprocessing. Use the IDA tool to disassemble the malicious code to be determined, and get the core binary content through regular expression matching, and remove useless information at the same time.
[0037] The core binary content is specifically, after the malicious code is disassembled, the assembly code is obtained, and the IDA tool marks the code segment (".text"), data segment (".data", ".rdata", ". .idata") and the resource segment (".rsrc"). In this embodiment, the code segment and the data segment are regarded as the core content of the malicious code, and the resource segment is ignored.
[0038] The removal of useless information specifically means that there is a data alignment pseudo-instruction (align) in the code to improve access efficiency, which has no practical significance for judgm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com