Method and device for tampering authentication of paper documents
A paper-based document and paper-based technology, applied in character and pattern recognition, instruments, calculations, etc., can solve problems such as slow speed, low accuracy, and inability to accurately locate tampered positions, achieving fast speed, high accuracy, and easy operation The effect of simple process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
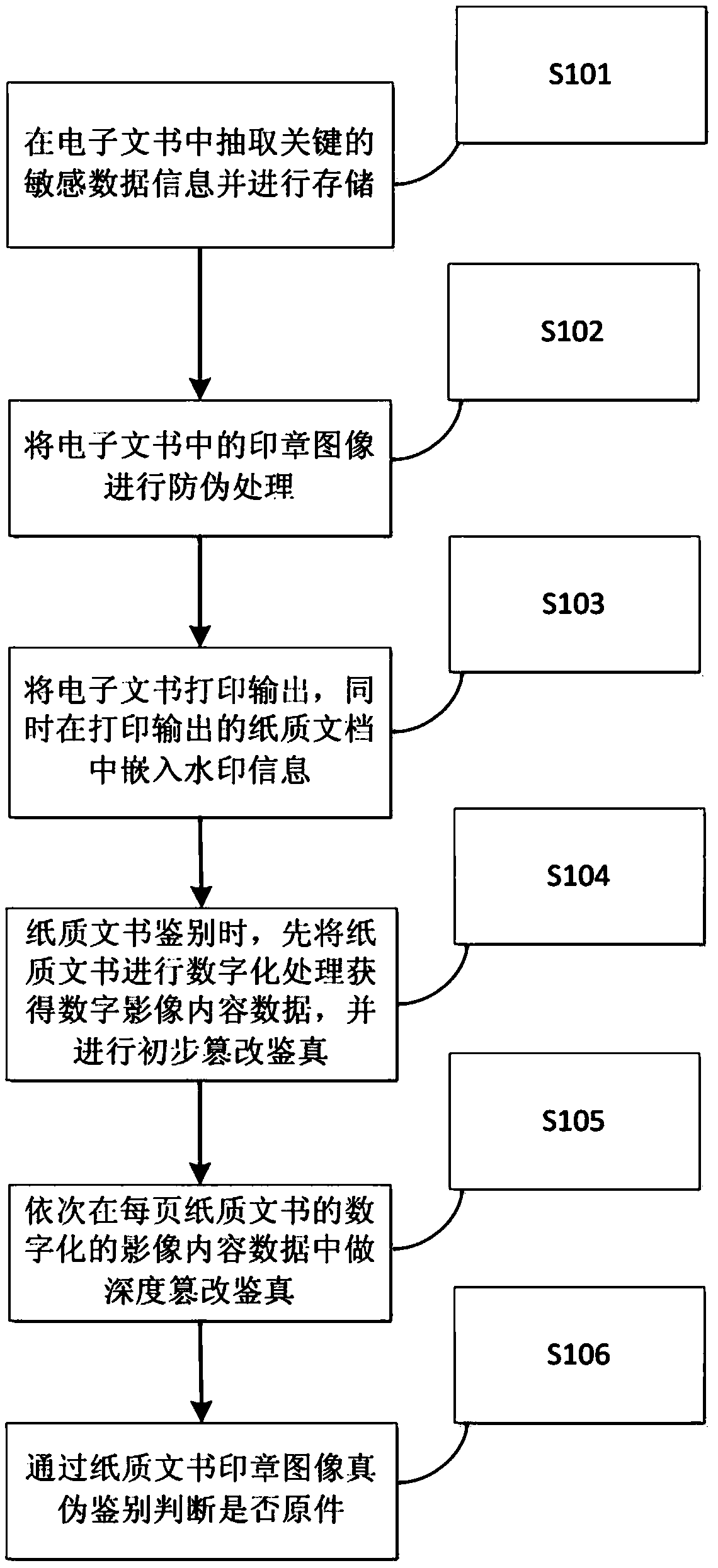
[0046] figure 1 It is a schematic flow chart of the implementation of a paper document tampering authentication method described in the embodiment.
[0047] S101. Extract and store key sensitive data information in the electronic document.
[0048] Important paper documents such as general financial business contracts and legal documents will contain a lot of key sensitive data information, including the unique ID information of electronic documents, page number information, sensitive digital information, the name of Party A and Party B, and one of the contract dates. or more. This information is very important. Once it is illegally tampered with, it will directly lead to excessive economic losses and conflicts. In order to quickly and accurately check whether the key sensitive data information has been tampered with, it needs to be stored in advance, that is, the sensitive data information extracted from the electronic document is stored in the background audit information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com