Permissioned blockchain constructing and controlling method based on Chameleon hash function
A hash function, chameleon technology, applied in the field of permission chain construction and control based on the chameleon hash function, can solve the problems of illegal content or wrong transaction information amending the law, criminal financial order, inability to supervise, etc., and achieve high-efficiency mechanism controllable , improve safety and ensure the effect of safe operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
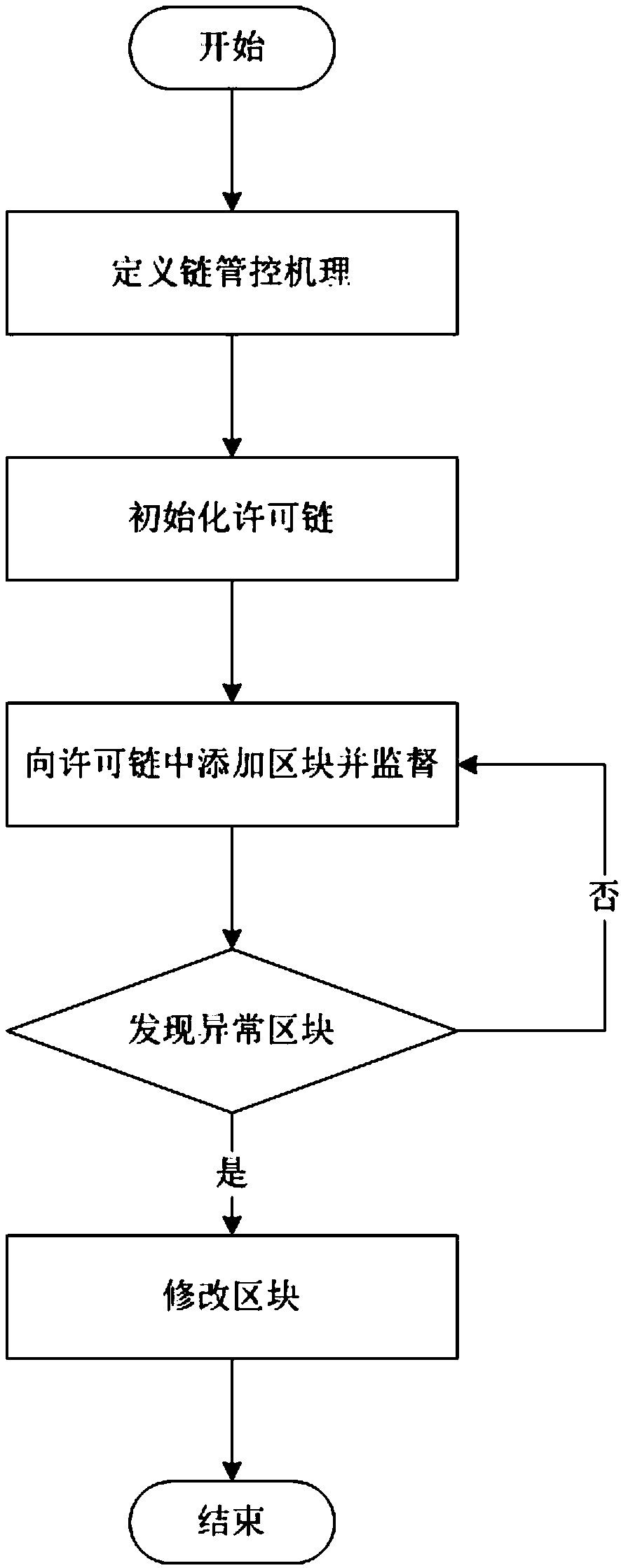
[0046] A permission chain construction and management method based on the chameleon hash function provided by the preferred embodiment of the present invention includes the following steps:
[0047] Step 1. Define the chain management mechanism and initialize the permission chain according to the chain management mechanism.
[0048] Step 2. Add a new block to the permissioned chain.
[0049] Step 3. Supervise the blocks in the permission chain according to the chain control mechanism, and control the blocks that do not meet the chain control mechanism.
[0050] Among them, the chain control mechanism includes block format and block control conditions. The block format includes block header and block body, and the block size is 1M. The block header includes the version number version, the hash value pre-hash of the previous block, the random number nonce, the workload proof difficulty value complex, the timestamp timestamp, the Merkle hash tree root node root, the chameleon r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com