Identity authentication method, apparatus and system
A technology of identity authentication and identity information, which is applied in the field of identity authentication methods, devices and systems, can solve problems such as inconvenient operation and low interaction efficiency, and achieve the effects of simplifying user operations, improving interaction efficiency, and improving interaction security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
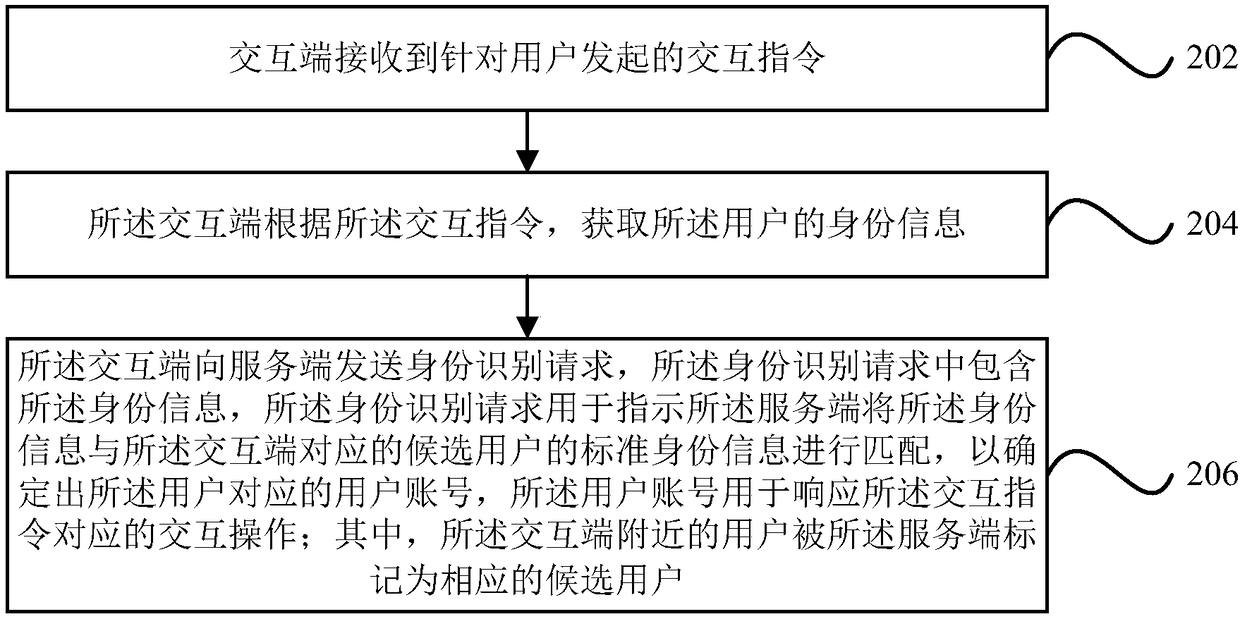
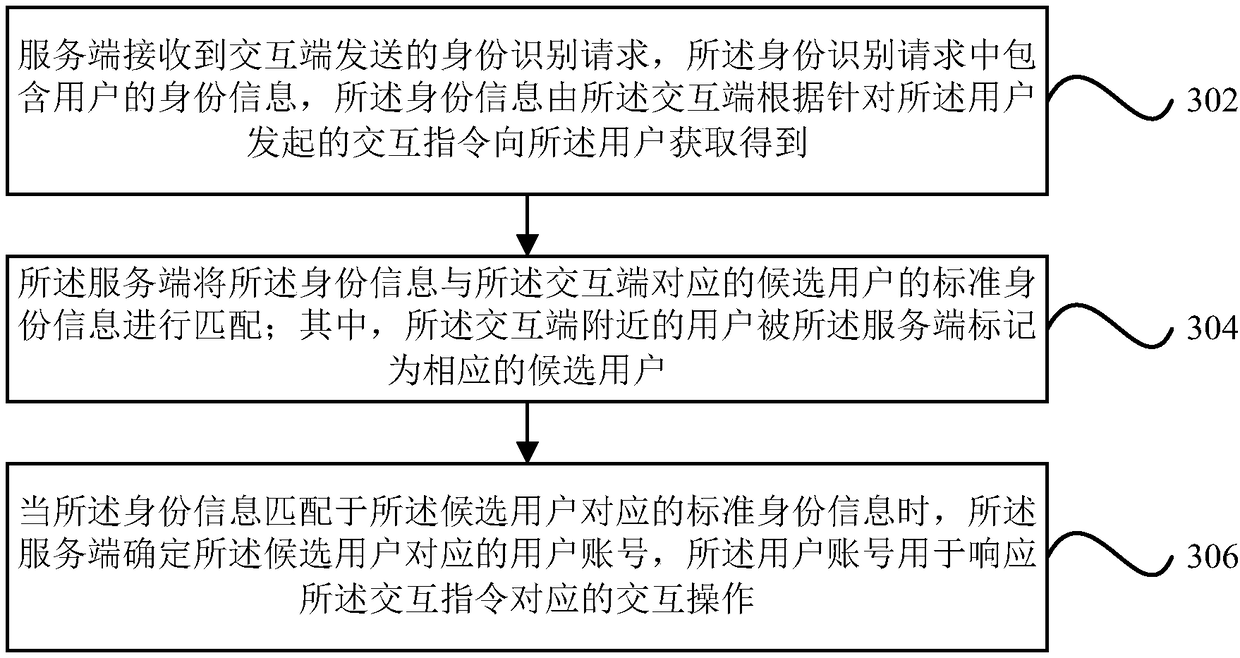
Embodiment Construction
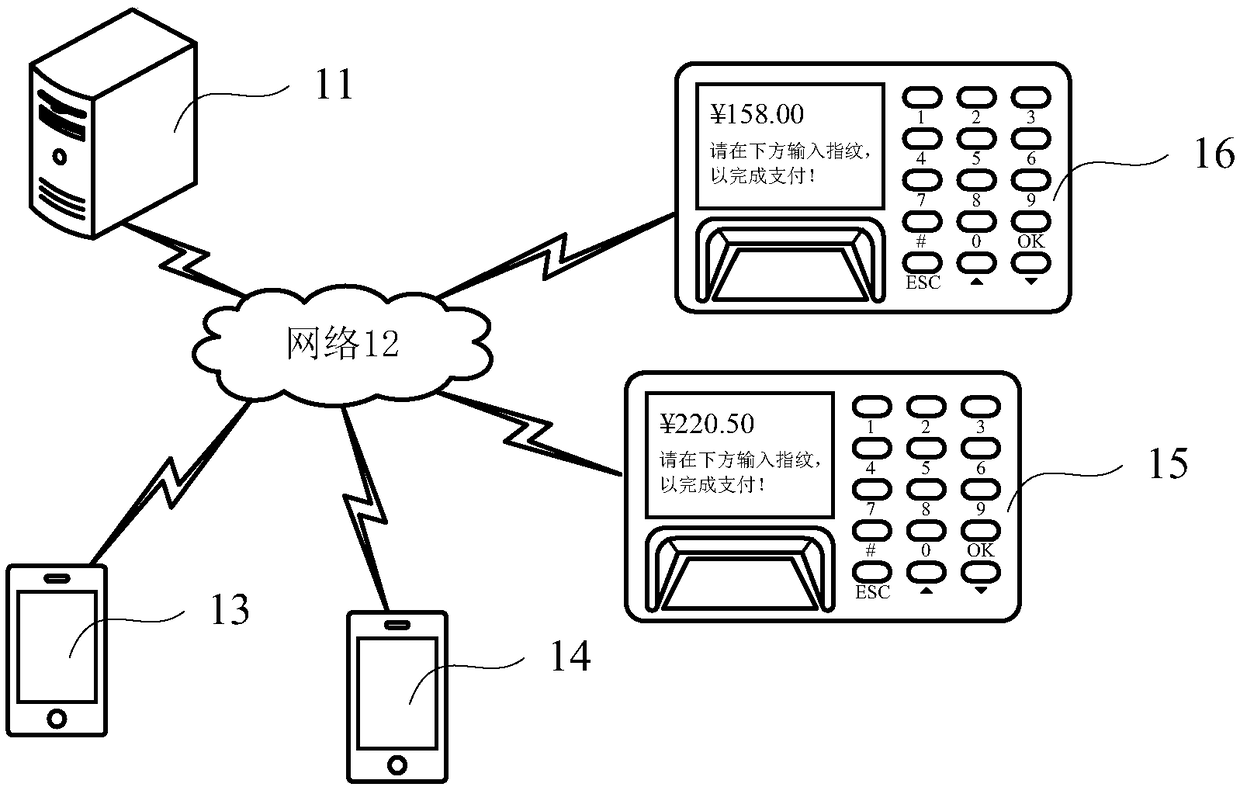
[0050] figure 1 It is a schematic structural diagram of an identity authentication system provided by an exemplary embodiment of the present application. Such as figure 1 As shown, the system may include a server 11, a network 12, several user devices (such as a mobile phone 13, a mobile phone 14, etc.) and interactive devices (such as a cash register device 15, a cash register device 16, etc.).
[0051] The server 11 may be a physical server including an independent host, or the server 11 may be a virtual server hosted by a host cluster, or the server 11 may be a cloud server. During operation, the server 11 can run a server-side program of a certain application to realize the relevant business functions of the application. For example, when the server 51 runs an interactive operation program, it can be configured as a service for realizing the interactive function end.
[0052] A cell phone 13-14 is just one type of user equipment that a user may use. In fact, users can ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com