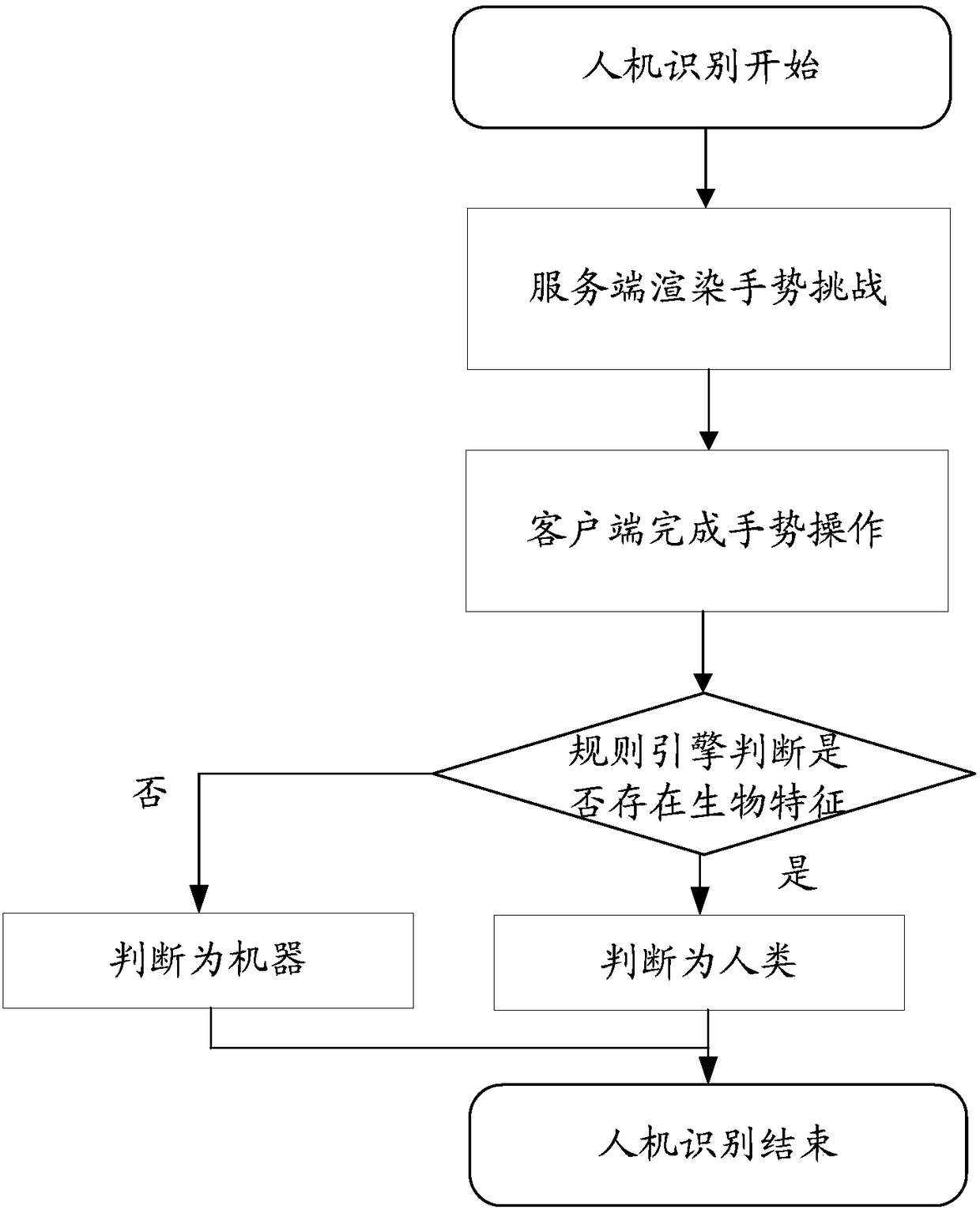
Human-machine recognition method, device and system
A human-machine identification and robot technology, applied in the field of human-machine identification, can solve the problem of low accuracy of human-machine identification, and achieve the effect of improving the accuracy and preventing machine request attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
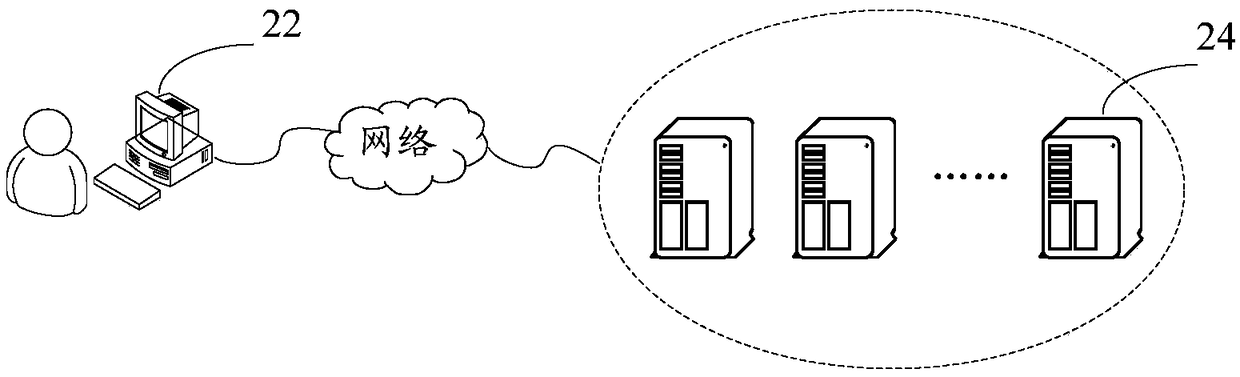
[0047] This application provides figure 2 The system of captcha is shown. figure 2 It is a schematic structural diagram of a human-machine recognition system according to Embodiment 1 of the present application, such as figure 2 As shown, the human-machine identification system includes: a terminal 22 and a server 24,
[0048] Terminal 22, used to collect user voiceprint information and behavior data information; server 24, connected to terminal 22, used to identify user voiceprint information and behavior data information uploaded by the terminal according to the pre-stored model, and judge user voiceprint information and behavior Whether the operation object to which the data information belongs is the same as the target object in the pre-stored model, output a corresponding judgment result according to the type of the target object, wherein the judgment result includes: the operation object is a natural person; or, the operation object is a robot.
[0049] Specifically...
Embodiment 2
[0077] According to an embodiment of the present application, an embodiment of a method for human-computer identification is also provided. It should be noted that the steps shown in the flow charts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0078] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on the server as an example, Figure 4 It is a block diagram of the hardware structure of the server of a human-computer identification method in the embodiment of the present application. Such as Figure 4 As shown, the server 40 may include one or more (only one is shown in the figure) processors 402 (the ...
Embodiment 3
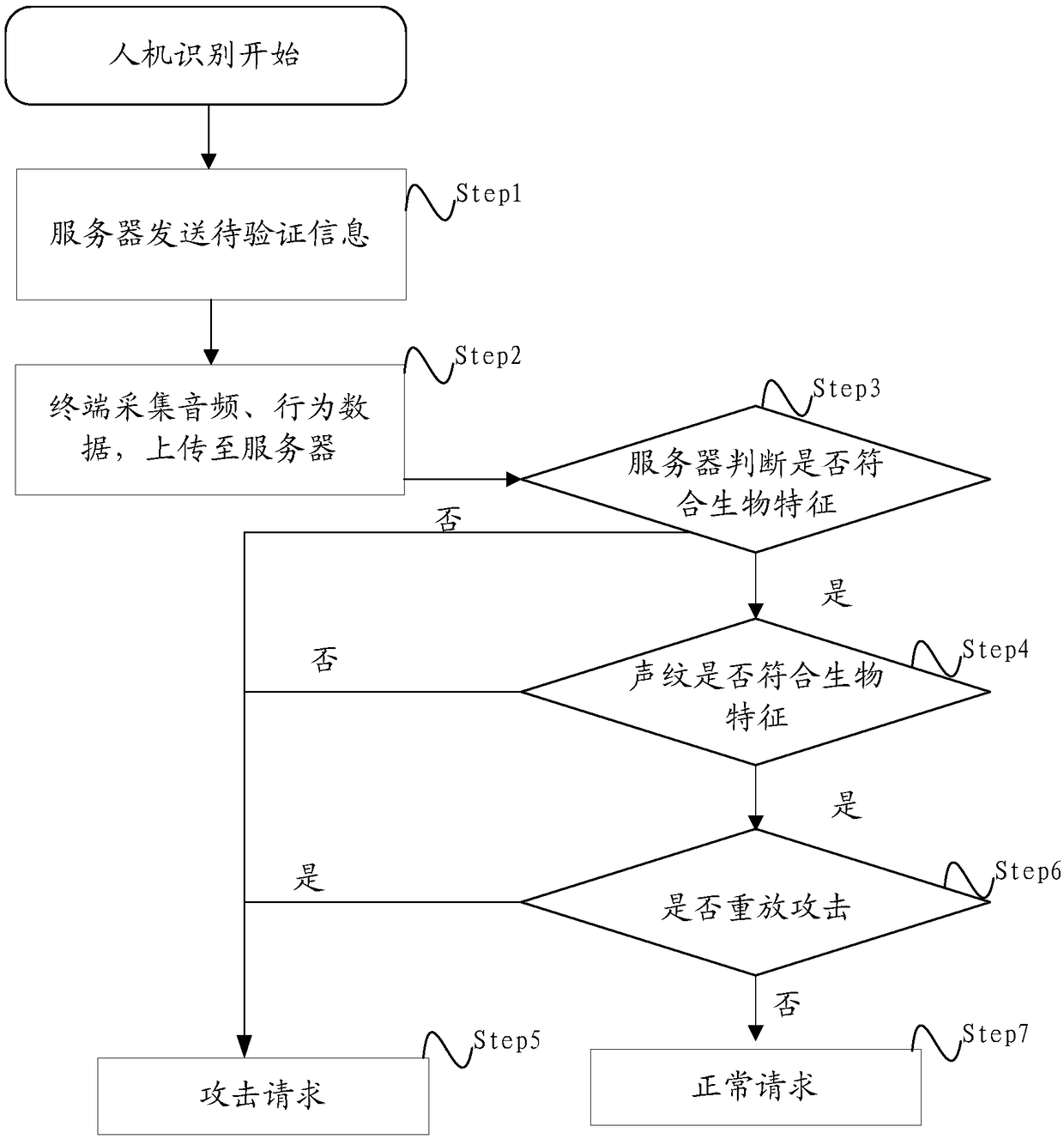
[0110] This application provides Figure 6 The method of human-computer identification is shown. On the terminal side, Figure 6 It is a flow chart of the human-computer identification method according to Embodiment 3 of the present application.
[0111] Step S602, sending a verification request to the server;
[0112] Step S604, receiving the information to be verified returned by the server according to the verification request, wherein the information to be verified includes: voice information to be verified and behavior information to be verified;
[0113] Step S606, collecting user voiceprint information corresponding to the voice information to be verified, and collecting behavior data information corresponding to the behavior information to be verified;
[0114] Step S608, sending the user's voiceprint information and behavior data information to the server.
[0115] Specifically, corresponding to the terminal in Embodiment 1, the human-machine identification method...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com