Authentication method and system, arbitration node, storage medium
A technology of arbitration nodes and verification methods, applied in the fields of storage media, verification methods and systems, and arbitration nodes, can solve problems such as monopoly of verification operations, false verification results issued by peripheral nodes, etc., and achieve the effect of improving accuracy and realizing randomness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
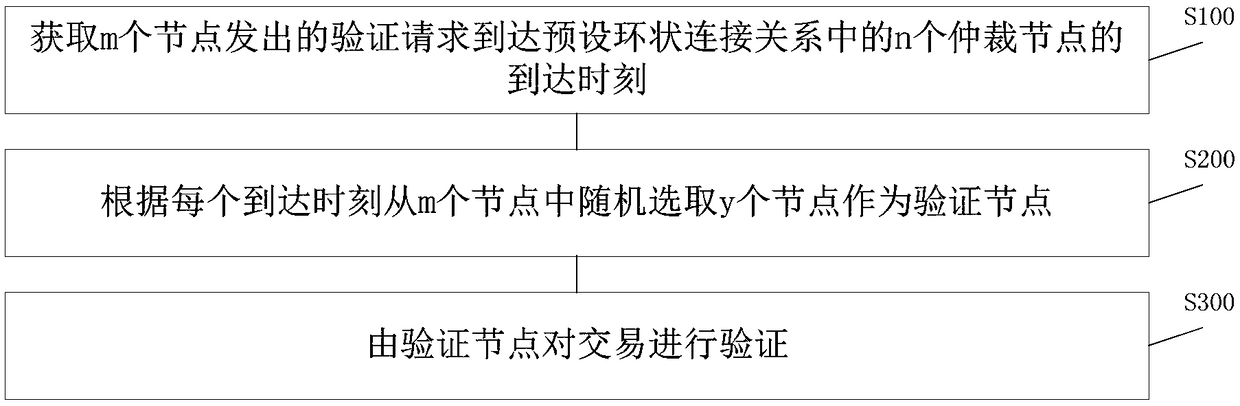
[0062] see figure 1 , figure 1 A schematic flowchart of a verification method provided by an embodiment of the present invention.
[0063] like figure 1 As shown, the method includes:
[0064] S100: Acquire the arrival times at which the verification requests sent by the m nodes arrive at the n arbitration nodes in the preset ring connection relationship.
[0065] The ring connection relationship includes multiple arbitration nodes. When a new transaction needs to be verified, each node in the blockchain has the right to send a verification request to any one of the n arbitration nodes. That is to say, in this embodiment, each node has an equal chance of sending a verification request. Regardless of the accounting ability of a node, and regardless of whether a node is near a node with strong accounting ability, a node, like other nodes, can send a verification request to the arbitration node.
[0066] Such as: a total of 20 nodes. Among them, the first node A is a node w...
no. 2 example
[0081] This embodiment is based on the first embodiment.
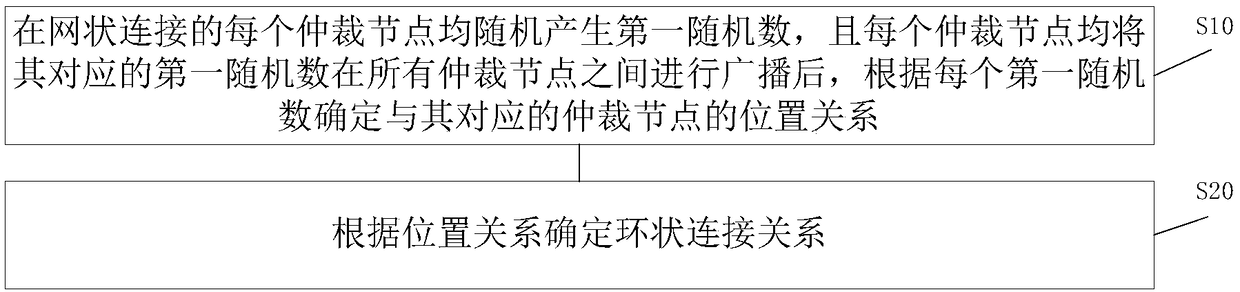
[0082] figure 2 A schematic flowchart of determining a ring connection relationship provided by an embodiment of the present invention. combine figure 1 and figure 2 It can be seen that before S100, the method also includes:
[0083] S10: After each arbitration node of the mesh connection randomly generates a first random number, and each arbitration node broadcasts its corresponding first random number among all the arbitration nodes, according to each first random number Determine the location relationship of its corresponding arbitration node.
[0084] When there are 20 quorum nodes, upon initialization, a mesh connection of 20 quorum nodes is established.
[0085] The mesh connection refers to a direct connection relationship between any two arbitration nodes.
[0086] The first random number determines the predecessor and successor relationship between the 20 arbitration nodes. That is, the positional rel...
no. 3 example
[0093] This embodiment is based on the second embodiment.
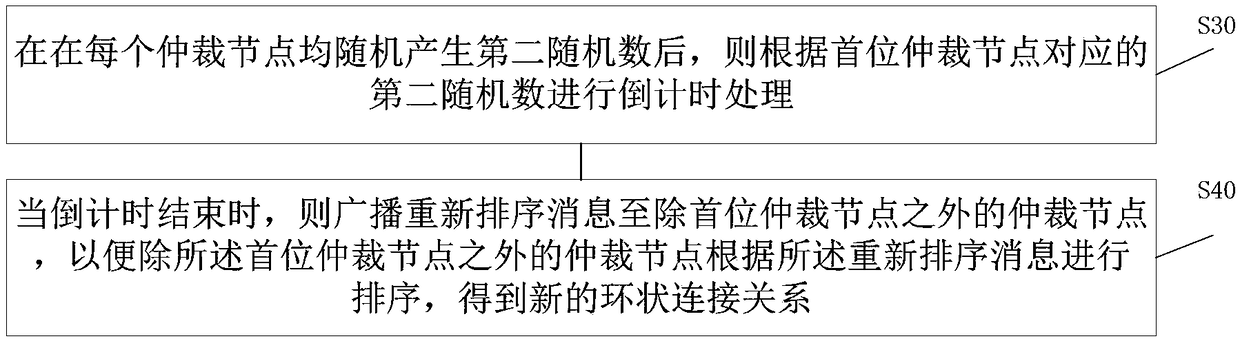
[0094] image 3 A schematic flowchart of determining a ring connection relationship provided by another embodiment of the present invention.
[0095] combine figure 1 , figure 2 and image 3 It can be seen that after S20, the method further includes:
[0096] S30: After each arbitration node randomly generates the second random number, perform countdown processing according to the second random number corresponding to the first arbitration node.
[0097] S40: When the countdown ends, broadcast the reordering message to the arbitration nodes other than the first arbitration node, so that the arbitration nodes other than the first arbitration node can sort according to the reordering message to obtain a new ring connection relation.
[0098] Among them, the n arbitration nodes include the first arbitration node.
[0099] The second random number determines when to initiate the change of the ring connection relat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com