Video anti-counterfeiting system, method and device
An anti-counterfeiting system and video technology, applied in the field of data processing, can solve the problems of cumbersome steps, the inability to detect the authenticity at one time, and the lack of value protection on the Internet, so as to achieve the effect of improving the accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
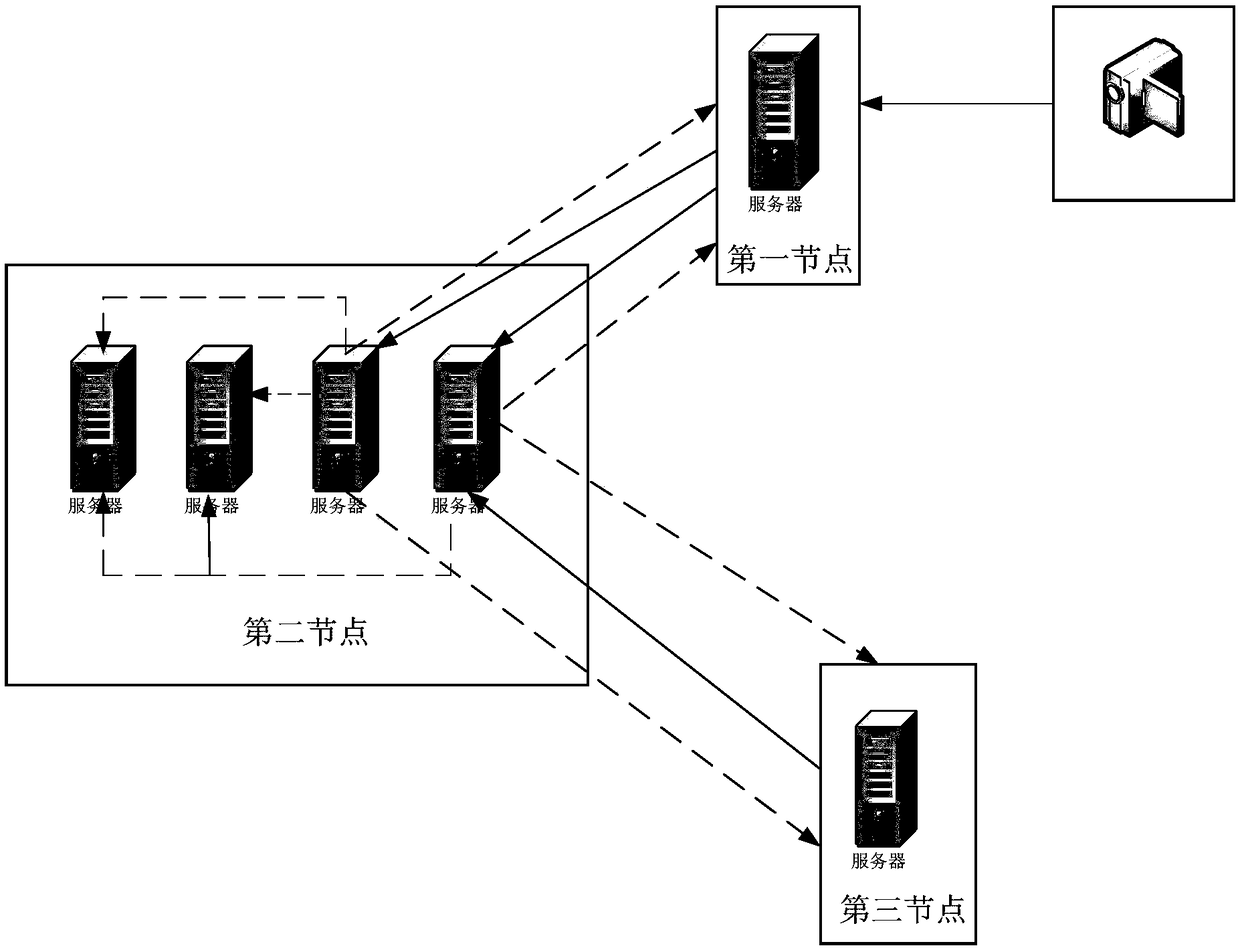
[0048] The embodiment of the present application provides a video anti-counterfeiting system. The above-mentioned video anti-counterfeiting system adopts block chain technology, and a block chain network is formed by building a node network on multiple servers in the Internet. A node refers to a server in the block chain network. . Nodes can communicate based on application layer protocols. The communication protocols used include, for example: Hypertext Transfer Protocol (HyperText Transfer Protocol, HTTP), File Transfer Protocol (File Transfer Protocol, FTP) and Transmission Control Protocol (Transmission Control Protocol, TCP). )Wait. Bootstrapping and interconnection are achieved through Domain Name System (DNS) seeds, node seeds, and enumeration of specified network segments, so that each node can send and receive messages with each other.
[0049] refer to figure 1 As shown, it is a structural diagram of a video anti-counterfeiting system provided by an embodiment of t...
Embodiment 2
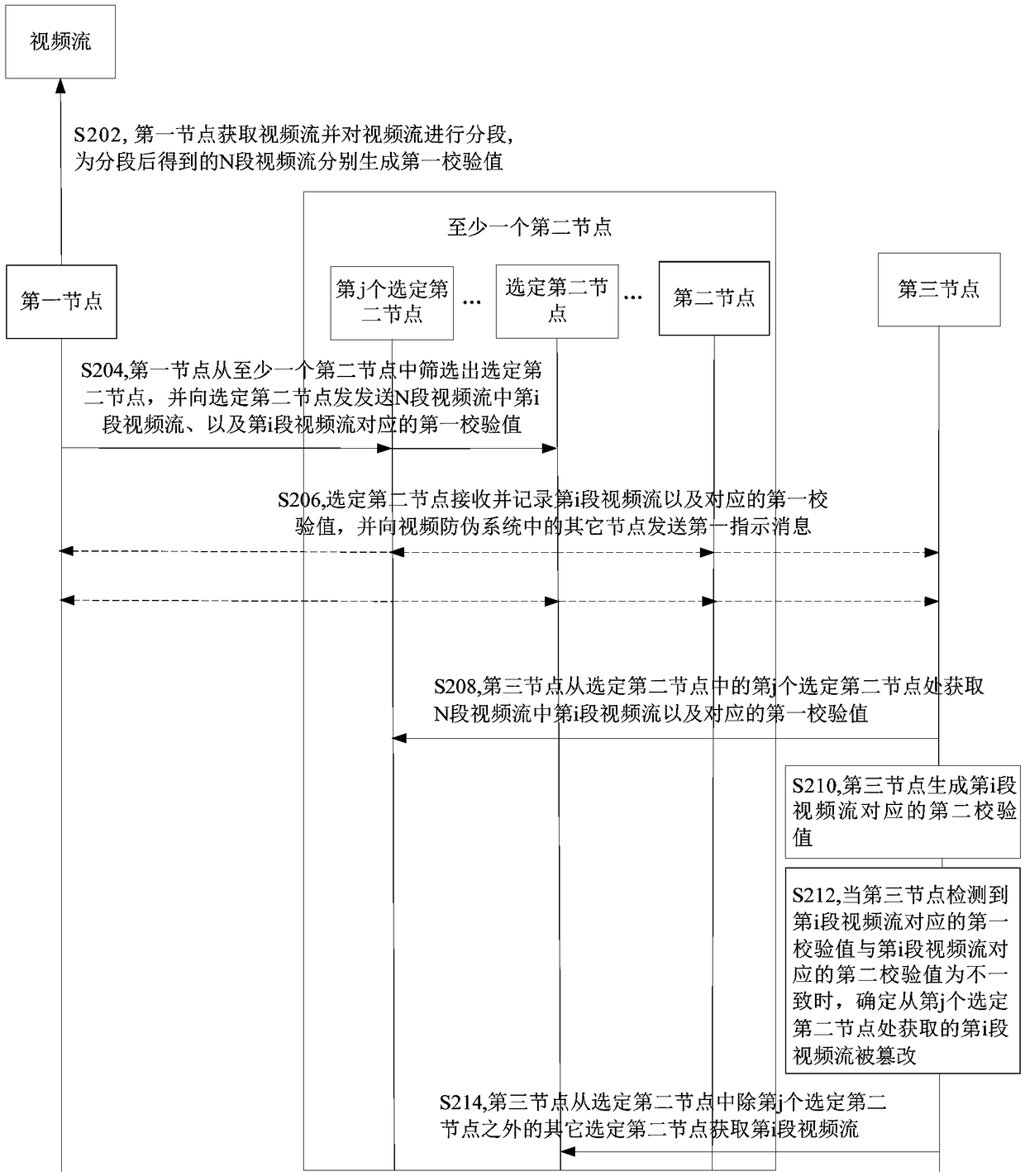
[0075] The embodiment of the present application also provides a video anti-counterfeiting method. For better illustration, image 3 Shown is a schematic flow chart of a video anti-counterfeiting method, the steps are as follows:
[0076] In step S302, the first node obtains the video stream and segments the video stream; the first node generates first check values for N segments of the video stream obtained after segmentation, where N is a positive integer.
[0077] In step S304, the first node screens out a selected second node from at least one second node.
[0078] Step S306, the first node sends to the selected second node the i-th video stream in the N video streams and the first check value corresponding to the i-th video stream, where i is any positive integer less than or equal to N, where , the second node is selected to provide the i-th video stream and the corresponding first check value to the third node, and the third node generates the second check value base...
Embodiment 3
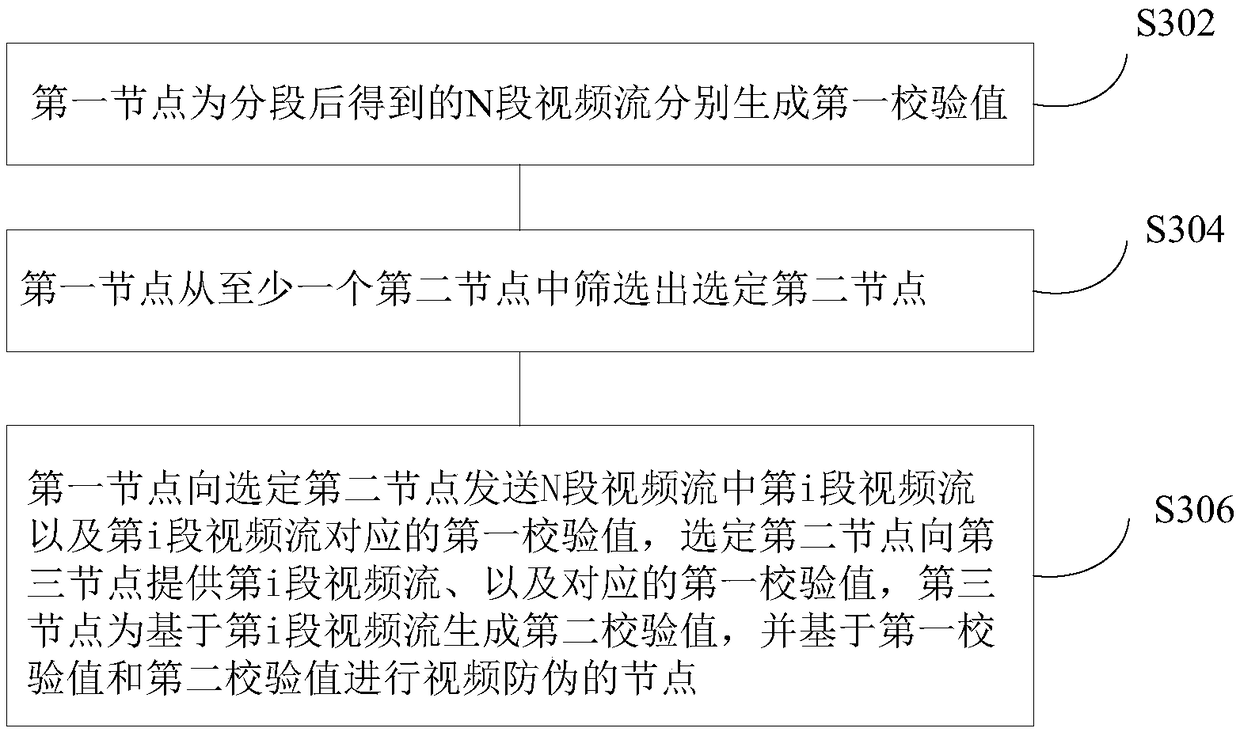
[0081] The embodiment of the present application also provides a video anti-counterfeiting method. For better illustration, Figure 4 What is shown is a schematic flow chart of another video anti-counterfeiting method, and the steps are as follows:
[0082] In step S402, the second node is selected to receive the i-th video stream among the N video streams sent by the first node, and the first check value corresponding to the i-th video stream.
[0083] Step S404, the selected second node sends a first indication message to other nodes in the video anti-counterfeiting system, the first indication message is used to indicate that the selected second node records the i-th video stream and the corresponding first check value.
[0084] Step S406, after the selected second node receives the acquisition request sent by the third node, it sends the i-th video stream and the corresponding first check value to the third node; the third node generates the i-th video stream based on A s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com