A Cross-Platform Association Detection Method for Firmware Vulnerability
A detection method and cross-platform technology, which is applied in the field of cross-platform correlation detection of firmware vulnerabilities, can solve certain problems such as accuracy, and achieve the effects of improving accuracy, high detection efficiency, and improving accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with accompanying drawing:
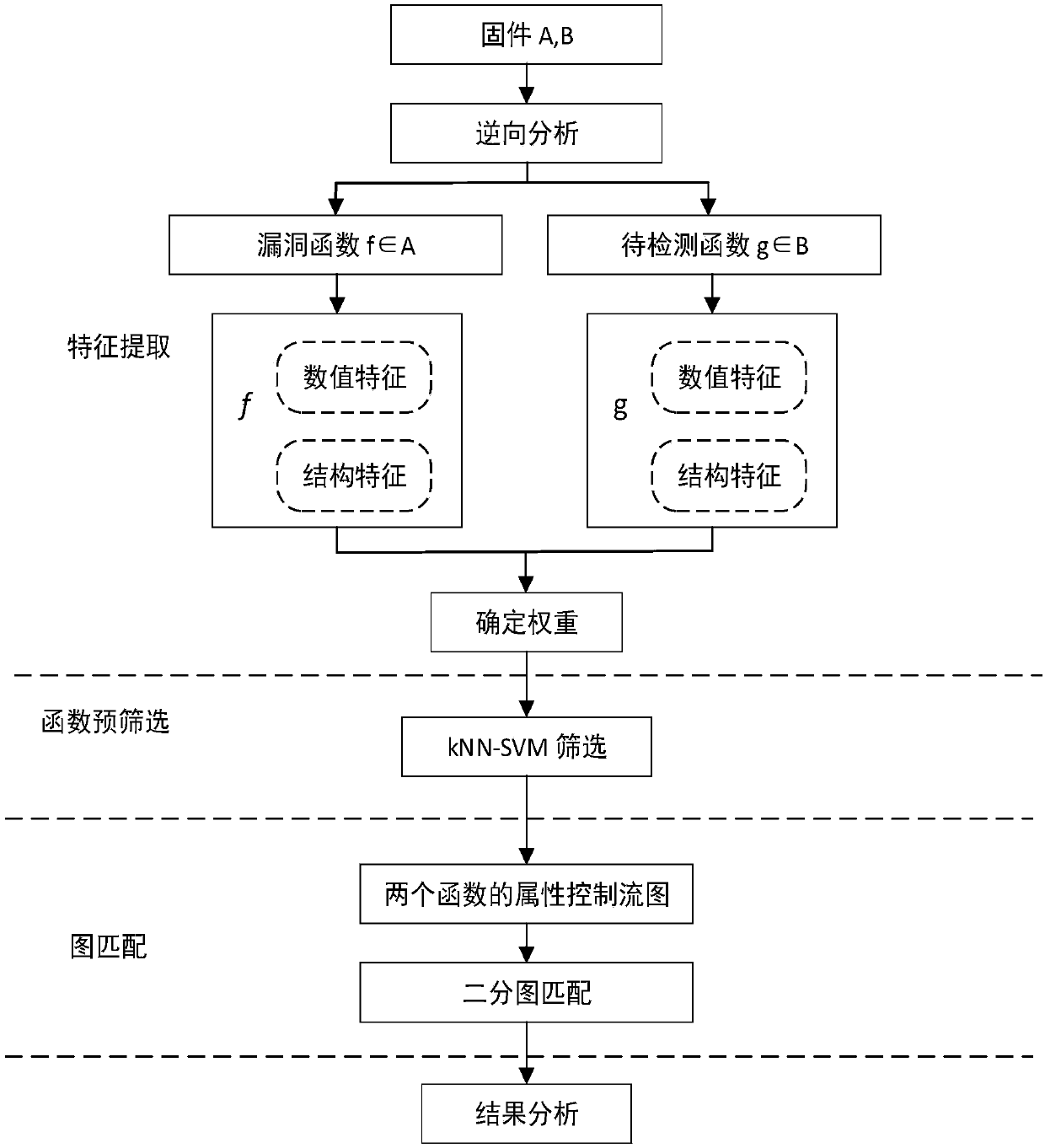
[0032] Such as figure 1 and figure 2 Shown: the present invention comprises the following steps:
[0033] S1: In the firmware acquisition stage, the firmware can be obtained by downloading the manufacturer's image or manually uploading by the user;
[0034] S2: Firmware decompression and disassembly stage, use the firmware decompression tool to obtain the binary files related to the firmware, and obtain the firmware disassembly function through firmware decompression and disassembly;
[0035] S3: extracting firmware function features;
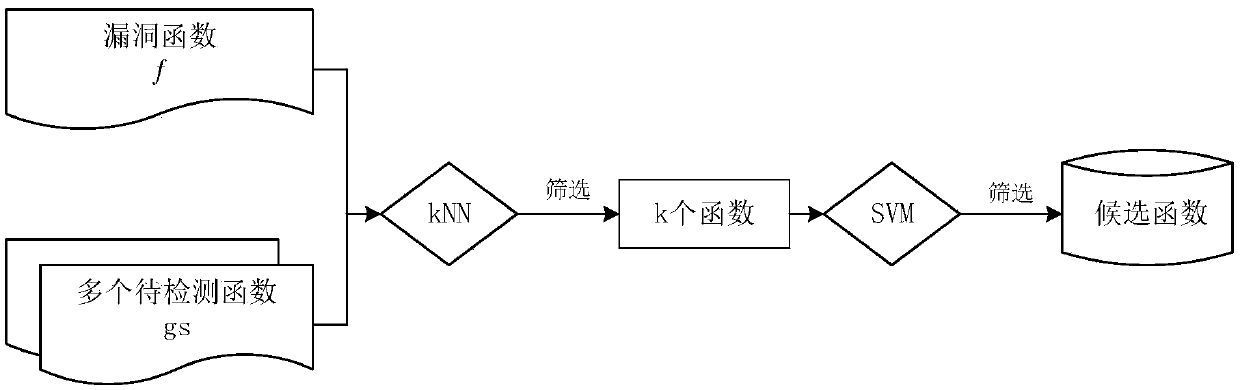
[0036] S4: Use the weighted Euclidean distance-based kNN-SVM to quickly screen and accurately match the functions to be detected, and judge the accuracy of the correlation between the functions to be detected and known vulnerability functions;
[0037] S5: Confirm that the function to be detected is a suspected vulnerability.
[0038] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com