History data processing method, system, and computer-readable storage medium
A technology of historical data and processing methods, which is applied in the fields of electronic digital data processing, computer security devices, calculations, etc., can solve the problems of information privacy leakage and achieve the effect of ensuring privacy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
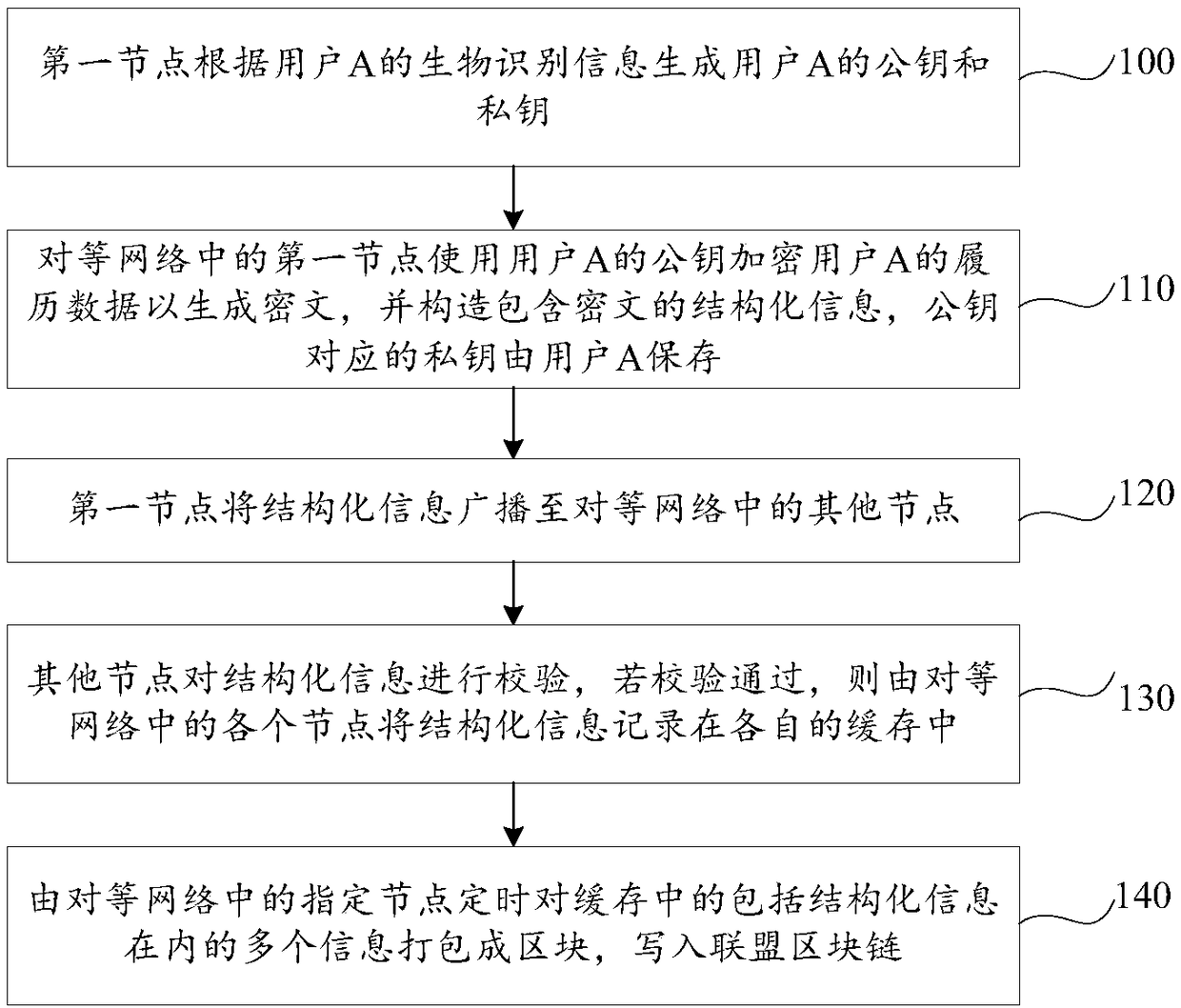
[0067] figure 1 It is a flow chart of the history data processing method provided by Embodiment 1 of the present invention, as shown in figure 1 As shown, the resume data processing method provided by the embodiment of the present invention may include the following steps:
[0068] 110. The first node in the peer-to-peer network uses user A's public key to encrypt user A's resume data to generate ciphertext, and constructs structured information including ciphertext, and the private key corresponding to the public key is stored by user A.
[0069] In an embodiment, a peer-to-peer network is composed of multiple peer-to-peer network nodes. The peer-to-peer network may be constructed using the Kademlia (Kad for short) protocol. Among them, Kademlia is a structured P2P overlay network, which belongs to a distributed hash table (DHT) technology. It uses a unique XOR algorithm (XOR) as the distance measurement basis to establish a DHT network topology. Has a very high routing qu...
Embodiment 2
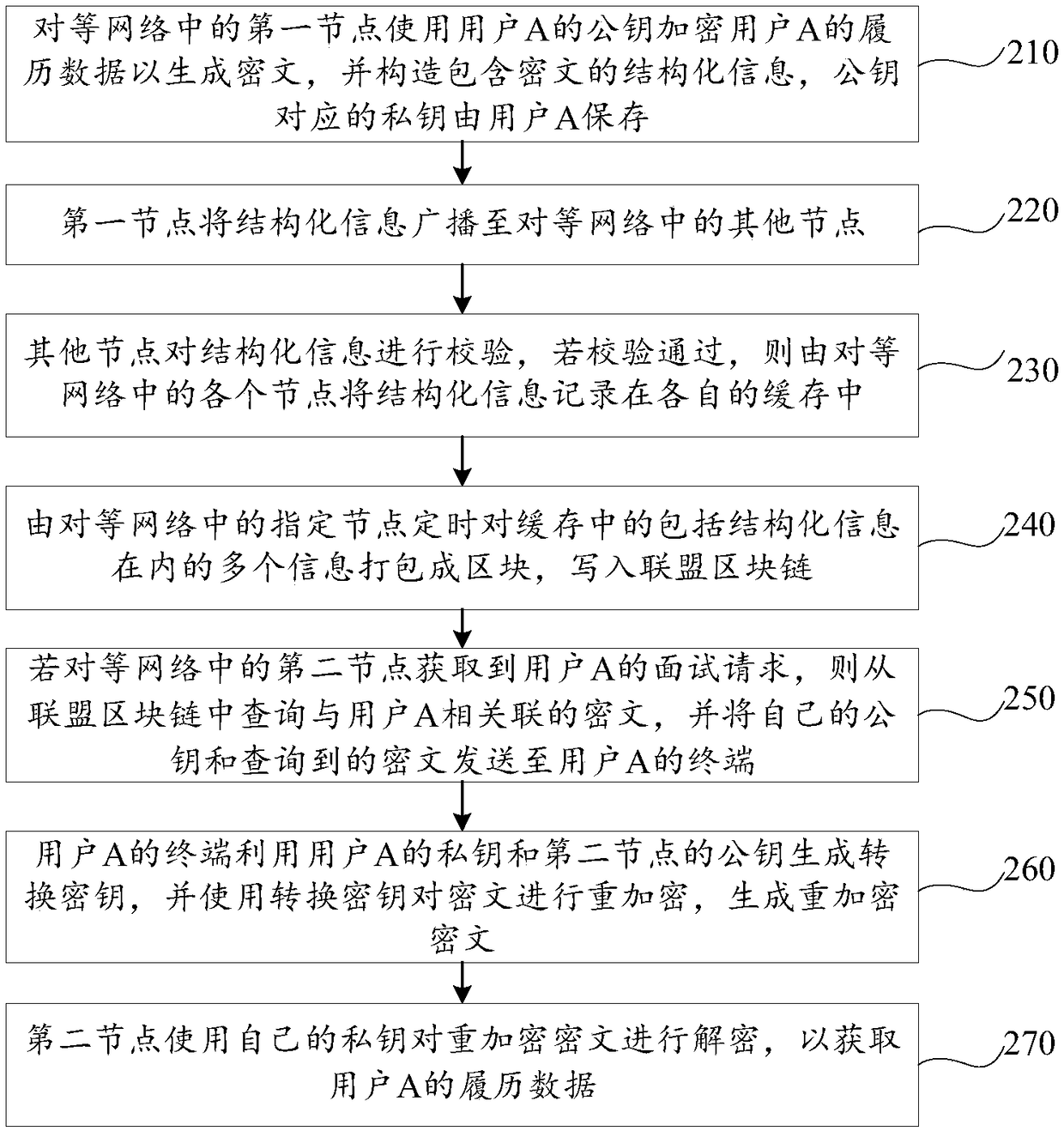
[0100] figure 2 It is a flow chart of the history data processing method provided by Embodiment 2 of the present invention, as shown in figure 2 As shown, the resume data processing method provided by the embodiment of the present invention may include the following steps:
[0101] 210. The first node in the peer-to-peer network uses the public key of user A to encrypt the resume data of user A to generate ciphertext, and constructs structured information including the ciphertext, and the private key corresponding to the public key is saved by user A.
[0102] Specifically, the implementation process of this step is the same as that of step 110, and will not be repeated here.
[0103] Optionally, before step 210, the method may also include:
[0104] The first node generates user A's public key and private key according to user A's biometric information.
[0105] Wherein, the biometric information includes any one or any combination of fingerprint information, face inform...
Embodiment 3
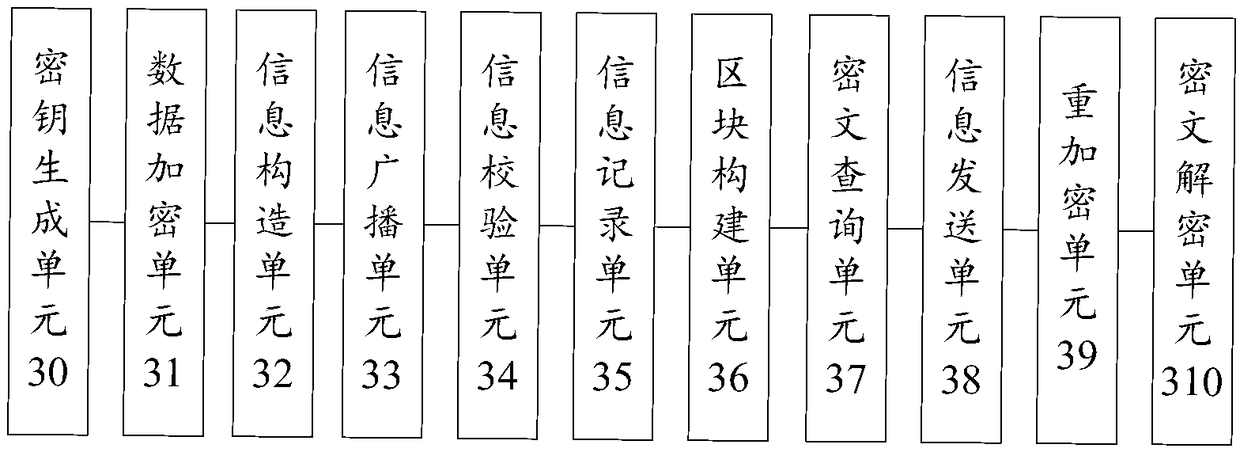
[0121] image 3 The block diagram of the resume data processing system provided for the third embodiment of the present invention, such as image 3 As shown, the resume data processing system provided by the embodiment of the present invention may include: .
[0122] The data encryption unit 31 is used for the first node in the peer-to-peer network to use the public key of user A to encrypt the resume data of user A to generate ciphertext, and the private key corresponding to the public key is saved by user A;
[0123] An information construction unit 32, configured for the first node to construct structured information including ciphertext;
[0124] An information broadcast unit 33, configured for the first node to broadcast structured information to multiple other nodes in the peer-to-peer network;
[0125] An information verification unit 34, used for other nodes to verify the structured information;
[0126] The information recording unit 35 is configured to record the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com