Face recognition authentication method, device, and electronic equipment
A technology of face recognition and identification, which is applied in the field of identity recognition, can solve problems such as low efficiency, and achieve the effect of improving efficiency and reducing the amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
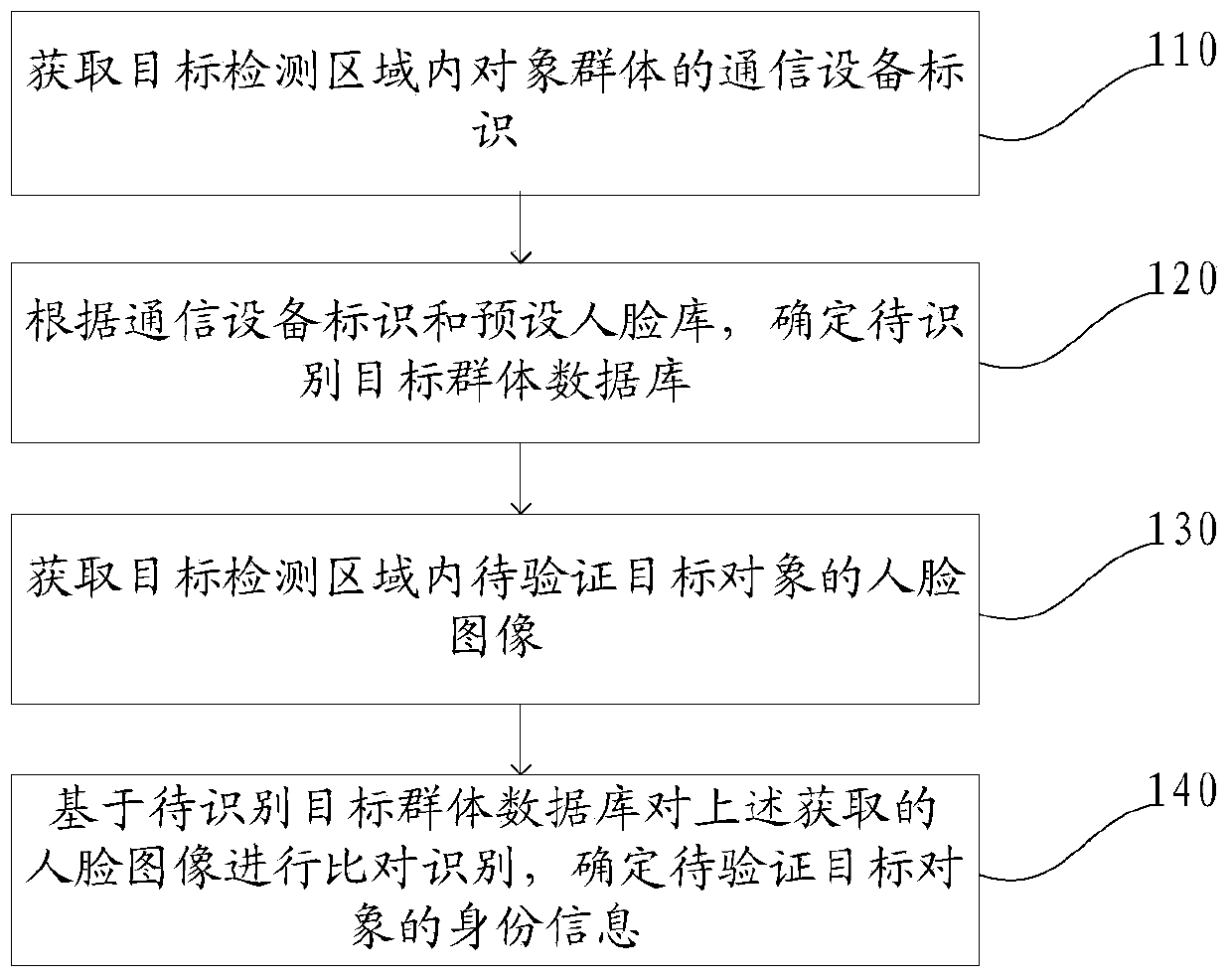
[0060] A face recognition identity verification method disclosed in this embodiment, such as figure 1 As shown, the method includes: step 110 to step 140.
[0061] Step 110, acquiring communication device identifiers of object groups in the object detection area.
[0062] The communication device in the embodiment of the present application may be: a mobile phone, a phone watch, etc., which has a unique identifier bound to the user's identity information, wherein the communication device identifier may be a phone number or a phone number of the phone watch. The target object may be a person to be identified.
[0063] In the specific implementation process of the present application, the communication equipment held by the object in the object group in the target detection area can be detected through communication technology.
[0064] For example, the mobile base station broadcasts a communication query signal, and receives a feedback signal from a communication device, and ...
Embodiment 2
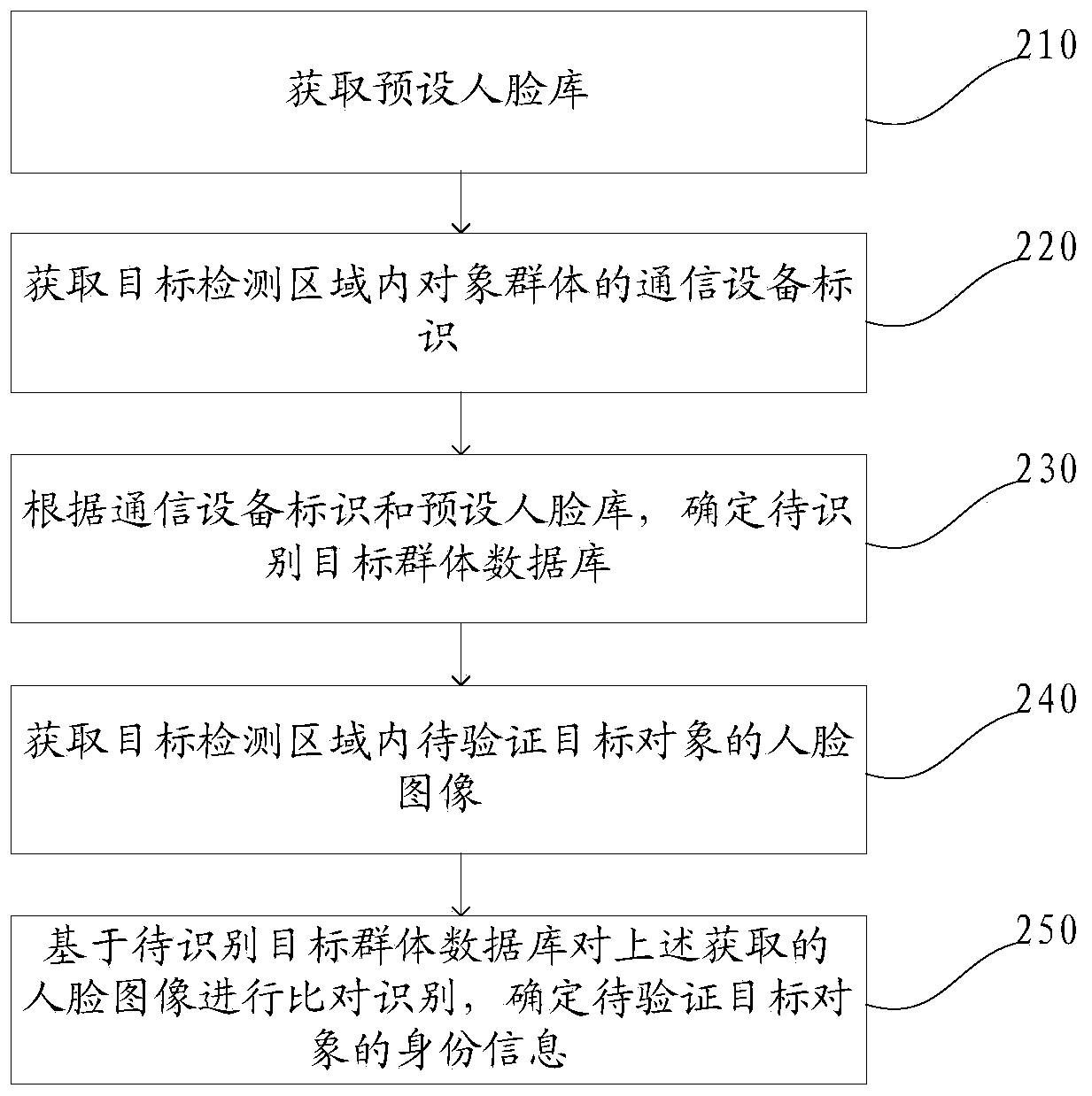
[0076] A face recognition identity verification method disclosed in this embodiment, such as figure 2 As shown, the method includes: Step 210 to Step 250.
[0077] Step 210, acquiring a preset face library.
[0078] In some embodiments of the present application, the above-mentioned face library includes a corresponding relationship consisting of at least a communication device identifier, identity information, and face information.
[0079] For example, the preset face library includes multiple sets of correspondences, and the format of each set of correspondences is as follows (communication device identification, identity information, face information). As more and more systems require real-name registration, such as mobile phone numbers or phone number applications, opening bank accounts, and handling certificate information, face databases including mobile phone numbers, identity information, and face images are easy to obtain.
[0080] During specific implementation, ...
Embodiment 3
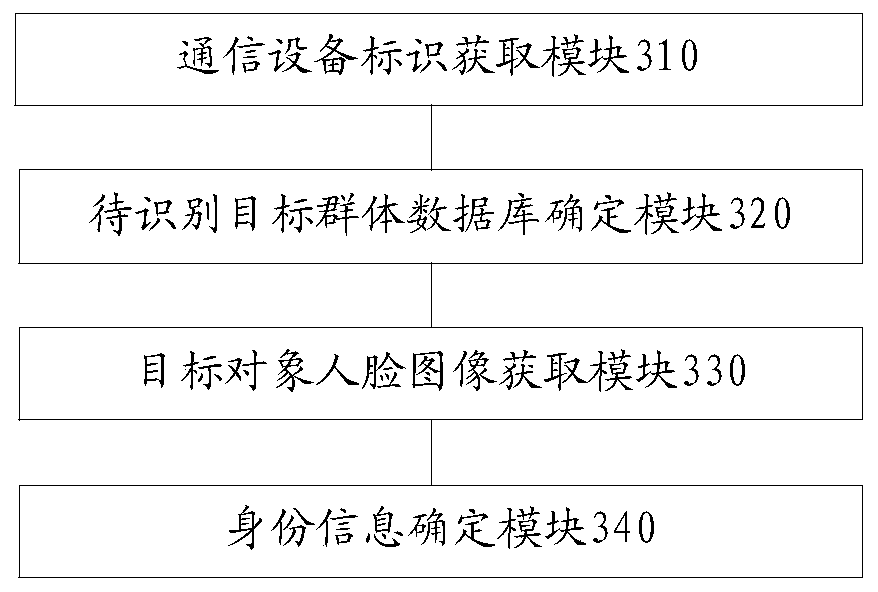
[0116] A face recognition authentication device disclosed in this embodiment, such as image 3 As shown, the above-mentioned devices include:
[0117] A communication device identification acquisition module 310, configured to acquire communication device identifications of object groups in the target detection area;
[0118] The target group database to be identified module 320 is used to determine the target group database to be identified according to the communication device identification and the preset face library;
[0119] The face image acquisition module 330 of the target object is used to acquire the face image of the target object to be verified in the target detection area;
[0120]The identity information determination module 340 is used to compare and identify the face images obtained by the target object face image acquisition module 330 based on the target group database to be identified determined by the target group database determination module 320 to dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com