A Complexity-Based Emd(n,m,δ) Adaptive Image Steganography Method
A complex and adaptive technology, applied in image communication, electrical components, etc., can solve the problems of not considering the complexity of different textures of images, maintaining the visual quality of embedded dense carriers, and different visual masking effects.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
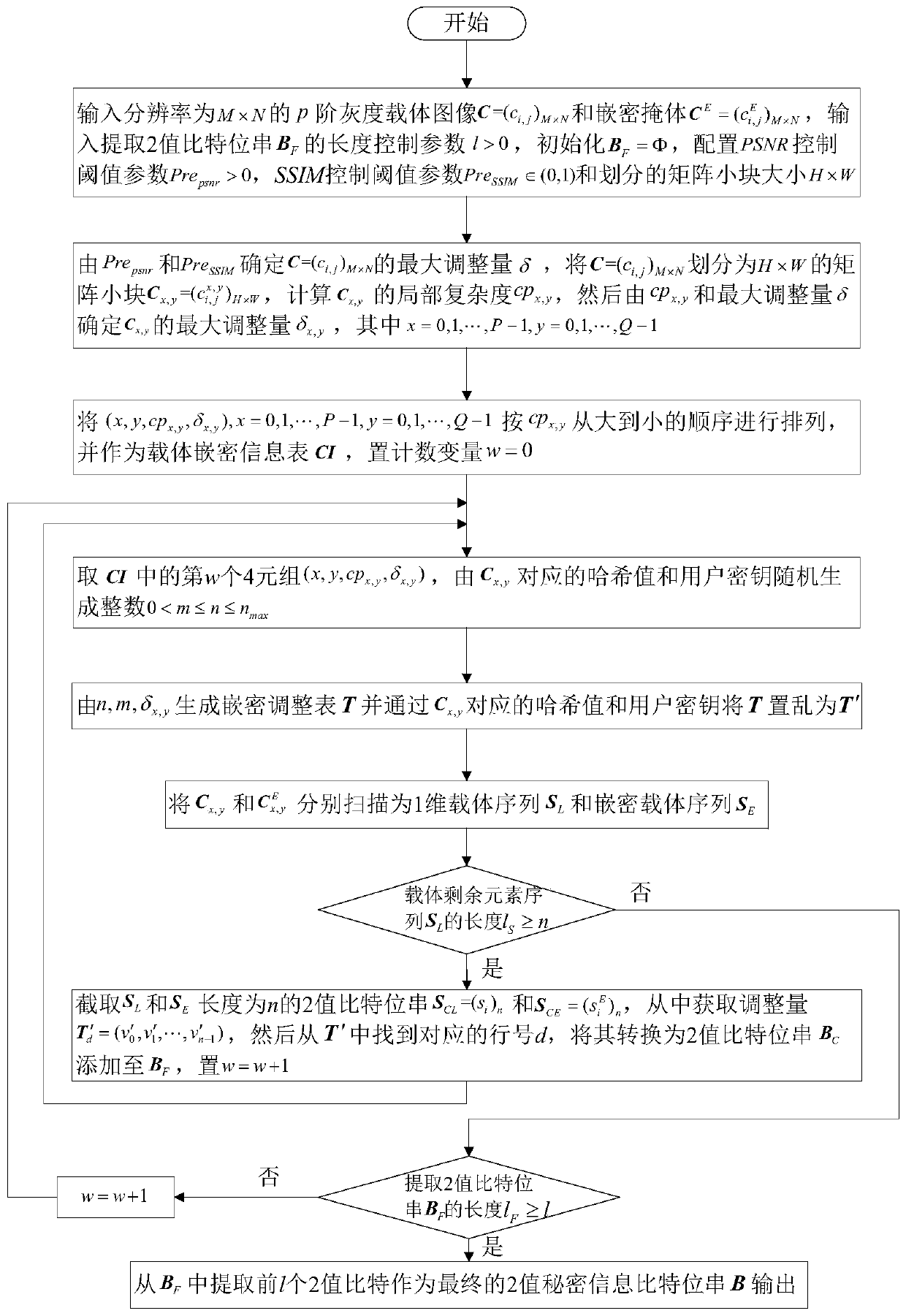
[0174] The following takes JAVA jdk1.8.0_65 as the case implementation environment, and describes the implementation of the present invention in detail in conjunction with the accompanying drawings, but is not limited to this implementation case, where figure 1 is the embedded flowchart, figure 2 is the extraction flow chart.
[0175] The specific implementation steps of the embedding method:
[0176] Step 1: Input the p-level grayscale carrier image C=(c i,j ) M×N , for example: if the input resolution is 4×4 8-level grayscale carrier image C, then M=4, N=4, p=8; input Pre psnr >0, Pre SSIM ∈(0,1], for example, you can enter Pre psnr = 45.91, Pre SSIM =0.87; Initialize the embedding bunker C equal to the resolution of C E =C, that is, C E and C are initialized to the same image; by Pre psnr and Pre SSIM Determine C=(c i,j ) M×N The specific method of the maximum adjustment amount δ is:
[0177] Step 1.1: Initialize δ=1, then apply integer random disturbance r to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com