A chip computing method based on edge trusted cryptography technology
A computing method and cryptography technology, applied in the field of chip computing based on edge trusted cryptography technology, can solve the problems of forgery, alteration, damage and other problems of micro-cloud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
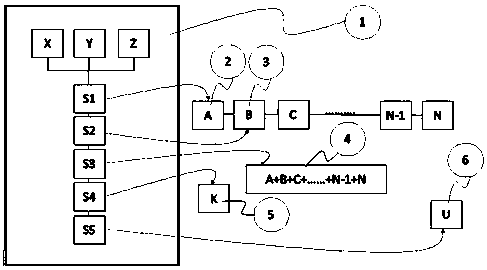
[0019] Attached below figure 1 And embodiment will further illustrate technical scheme of the present invention.
[0020] The chip computing method based on edge trusted cryptography technology includes the following steps:
[0021] First design and manufacture a cryptographic algorithm chip 1 including ECC, AES, Hash,
[0022] The cryptographic algorithm chip 1 includes X digital signature technology, Y digital authentication technology, and Z digital authentication technology;
[0023] The steps required to complete the algorithm are realized, including: S1 genesis block digital signature step, S2 superposition block digital signature step, S3 ledger data chain formation step, S4 consensus ledger Merkle hash tree digital authentication step, S5 customer hash public key ID digital authentication steps.
[0024] 2 is the schematic representation of step S1 of the digital signature of the genesis block, including making a data block of the root of trust in the micro-cloud ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com