Method, system and apparatus for defending bypassing of file uploading verification, and medium
A file upload and file technology, which is applied in the field of server security, can solve data hazards and other problems, and achieve the effects of accurate detection, high security, and reduced possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
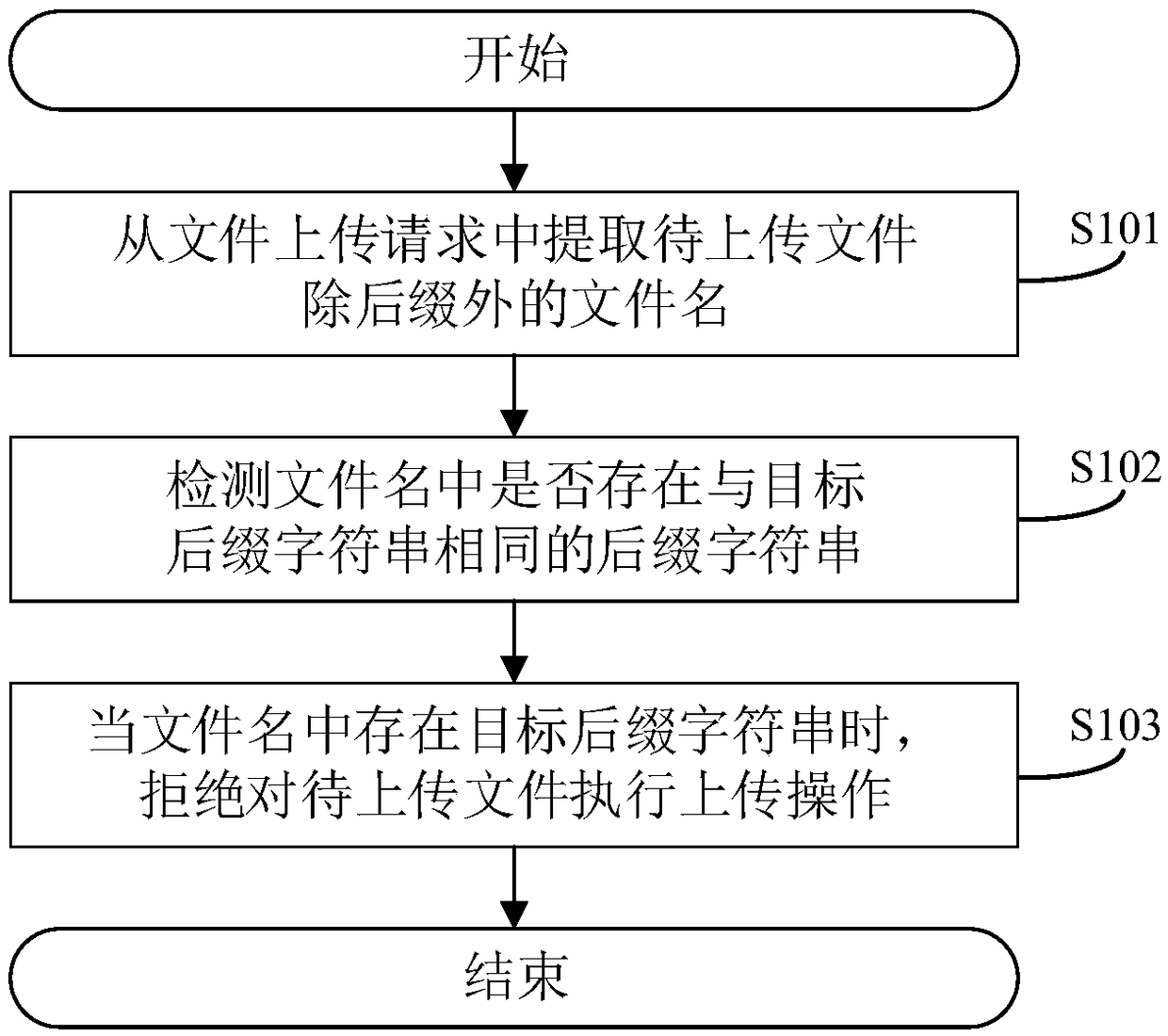
[0073] Combine the following figure 1 , figure 1 It is a flow chart of a method for defending file upload verification bypass provided by the embodiment of this application, which specifically includes the following steps:
[0074] S101: Extract the file name of the file to be uploaded except the suffix from the file upload request;
[0075] This step aims to obtain the file name of the file to be uploaded except the suffix, and the removed part is the part that can be recognized as the suffix by the prior art. Take the xxxxx.txt file as an example. The file name obtained in this step is "xxxxx", and the part identified as .txt is removed.
[0076] Wherein, the file name will be included in the file upload HTTP request as part of the feature information of the file to be uploaded, and the upload file verification mechanism will extract the file name from the preset position of the HTTP request. HTTP requests formed based on different specific protocols may contain different...
Embodiment 2
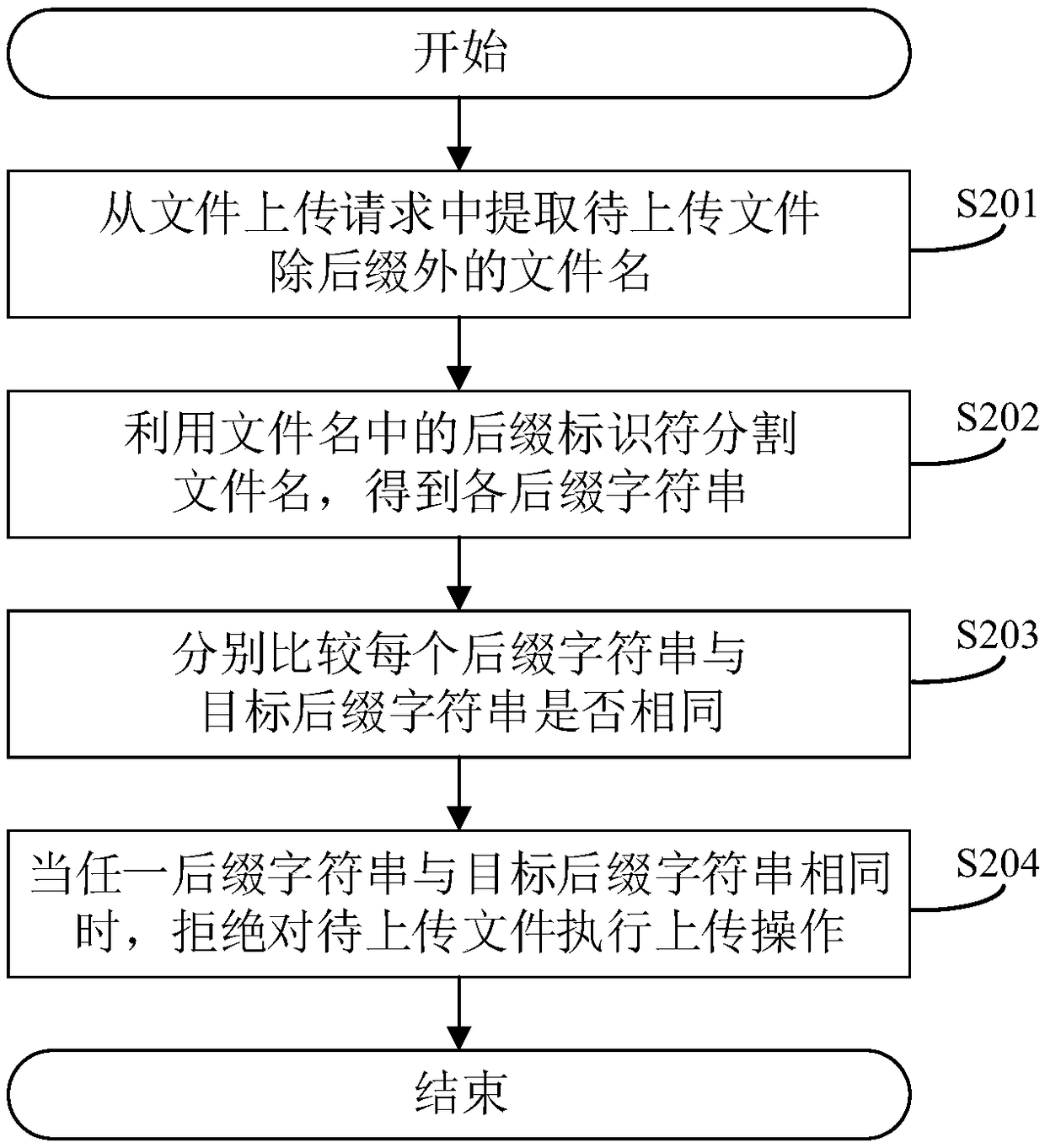
[0096] The following combination figure 2 , figure 2 The flow chart of another method for defending file upload verification bypass provided by the embodiment of this application is different from the first embodiment. This embodiment uses S202 and S203 to detect the file name in the first method mentioned in S102. Whether there is a suffix string identical to the target suffix string, S204 provides a specific strategy for rejecting the upload operation, and the specific steps are:
[0097] S201: Extract the file name of the file to be uploaded except the suffix from the file upload request;
[0098] S202: Split the file name by using the suffix identifier in the file name to obtain each suffix character string;
[0099] Still taking xxxx.jpg;.txt as an example, you will find that there are two suffix identifiers—“.”, which will be used as a separator to obtain two different suffix strings: “jpg;” and “txt”.
[0100] Normally, when there are interfering characters such as...
Embodiment 3
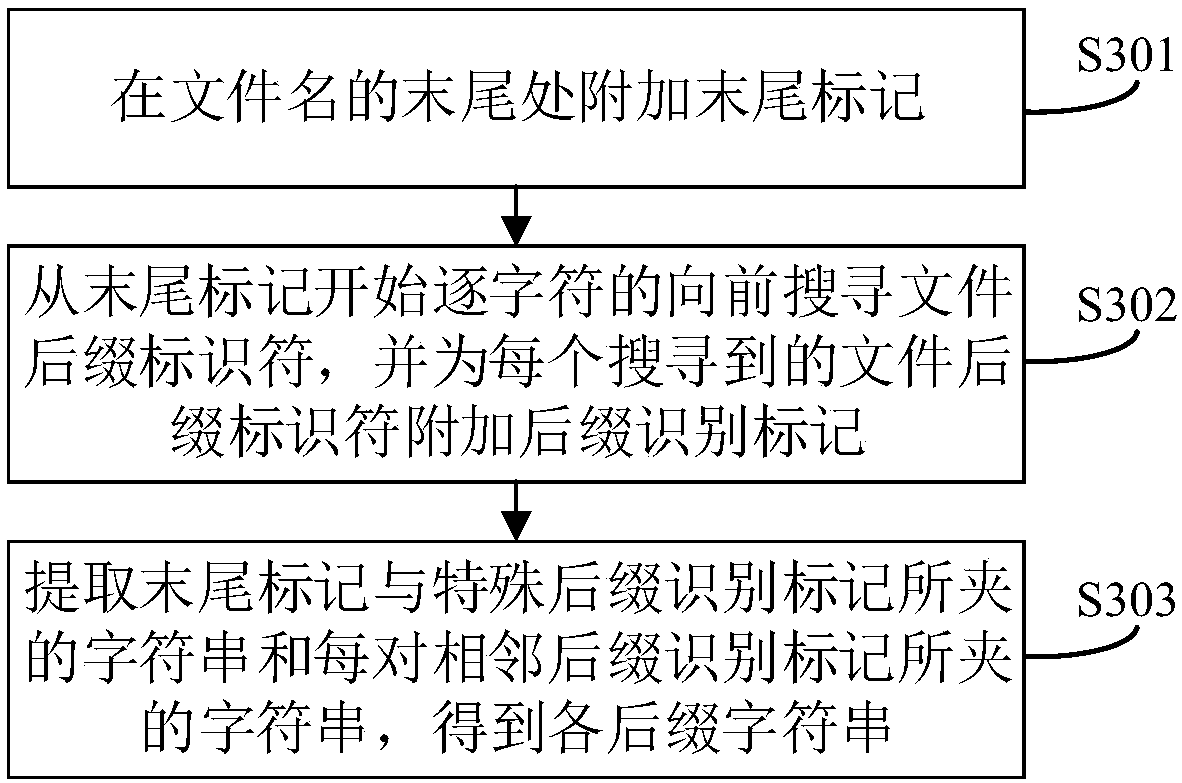
[0108] The following combination image 3 , image 3 It is a flow chart of a method for obtaining a suffix character string by segmenting a suffix identifier in the method for defending against file upload verification bypass provided by the embodiment of this application. This embodiment provides a specific implementation method for S202, and the remaining steps Do not make changes, specifically include the following steps:
[0109] S301: append an end mark at the end of the file name;
[0110] Take xxxx.jpg;.txt as an example, the end tag should be appended after txt.
[0111] S302: Search for the file suffix identifier character by character forward from the end mark, and attach a suffix identification mark to each searched file suffix identifier;
[0112] Wherein, the suffix identifier is ".", that is, this step starts from the end mark of the file name to identify whether each character is "." character by character, and attaches a suffix identification mark to each "....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com