Fuzzy key communication system and confrontation network system based on deep learning
A deep learning and communication system technology, applied in the field of fuzzy key communication system and confrontation network system, can solve the problem that Bob cannot guarantee restoration, and achieve the effect of improving analysis depth, strengthening communication performance, and accurate communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
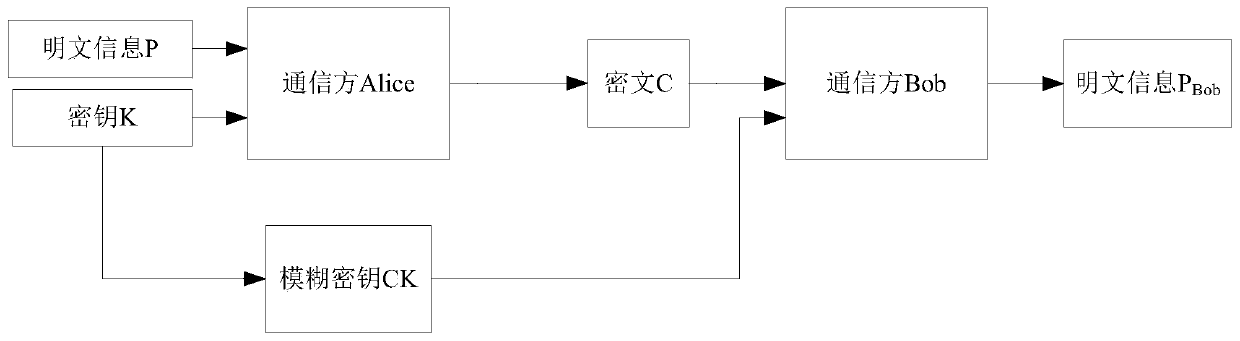
[0040] This embodiment 1 discloses a fuzzy key communication system based on deep learning, such as figure 1 As shown, including the communication party Alice and the communication party Bob.
[0041] The communicating party Alice includes an encryption model; the encryption model is obtained after deep learning of the first neural network model, and is used to input plaintext P and key K, and uses the input plaintext P and key K to form ciphertext C; the first neural network model Including the first fully connected layer and multi-layer convolutional layer from input to output;
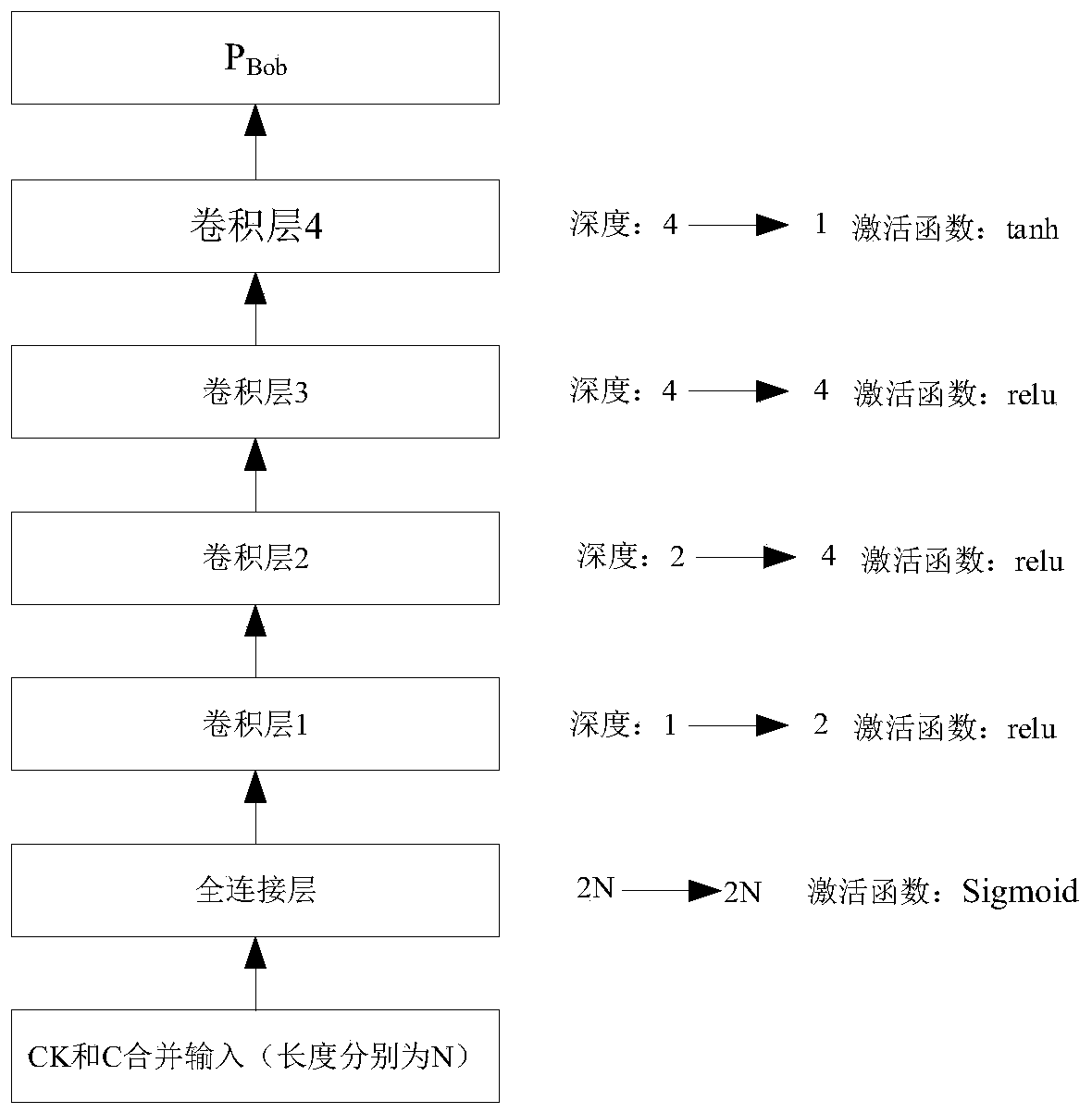
[0042] The communicating party Bob includes a decryption model; the decryption model is obtained after deep learning of the second neural network model, and is used to input the key and ciphertext, and decrypts the input ciphertext C according to the input key CK to obtain the plaintext information P Bob ;Such as Figure 2a As shown, the second neural network model includes the first fully connect...
Embodiment 2
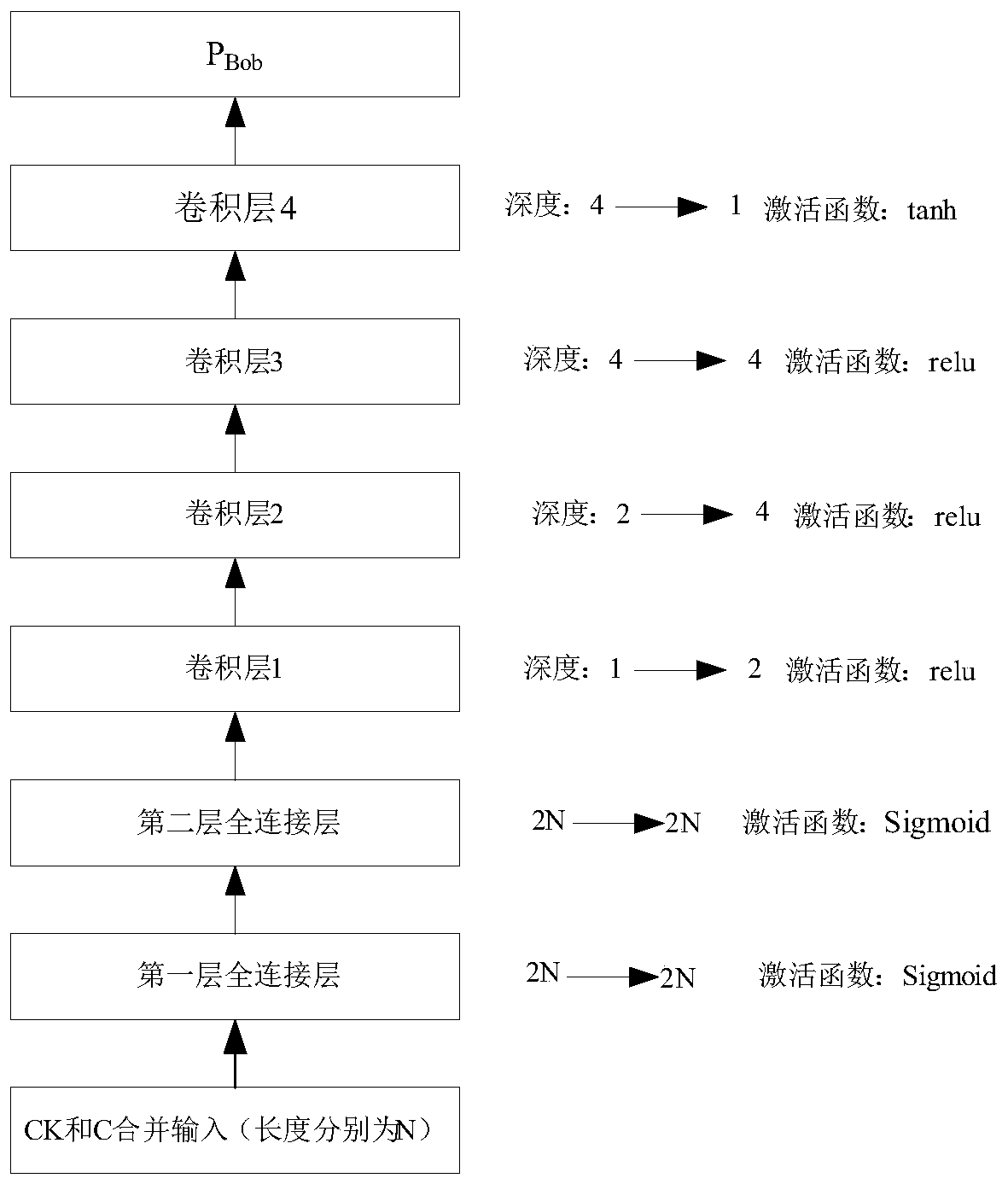
[0052] This embodiment discloses a fuzzy key communication system based on deep learning, such as Figure 4 As shown, the difference between this embodiment and Embodiment 1 is that the activation function of the layer close to the input end of the second neural network model in the second fully connected layer and the third fully connected layer of the second neural network model is set to tanh function.
[0053] In Embodiment 1, after adding a fully connected layer to the second neural network of the communication party Bob, the decryption ability of the entire communication system has been improved to a certain extent, but as Figure 3b As shown, it is impossible to implement error-free decryption for keys with a difference of 3 bits or more (n is greater than or equal to 3). After analyzing the system, it is found that in the second neural network model, when the fully connected layer near the input uses the Sigmoid function, it is not good for the weight update of the mo...
Embodiment 3
[0056] This embodiment discloses a fuzzy key communication system based on deep learning. This embodiment performs the following processing on the basis of Embodiment 1 or 2. In the second fully connected layer and the third fully connected layer of the second neural network model Both the connection layer and the first fully connected layer of the first neural network model are processed by batch normalization, and the processing of batch normalization is as follows: normalize the input so that the average value of the input is 0 and the variance is 1, and then Output to the next layer through the activation function.
[0057] After batch normalization processing in this embodiment, the stability of the communication system is greatly improved, and the probability that the model cannot find the lowest loss point due to different initialization conditions is reduced. During the training process, the learning rate can be increased without affecting the training of the model, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com