Implementation method of visitor system based on two-dimensional code recognition
A technology of visitor system and implementation method, which is applied in the direction of instruments, time registers, single input port/output port registers, etc., can solve the problems of access control cards that are easy to be lost, not returned in time, and labor-intensive, so as to avoid loss and non-timely return, reduce workload, and ensure the effect of enterprise safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
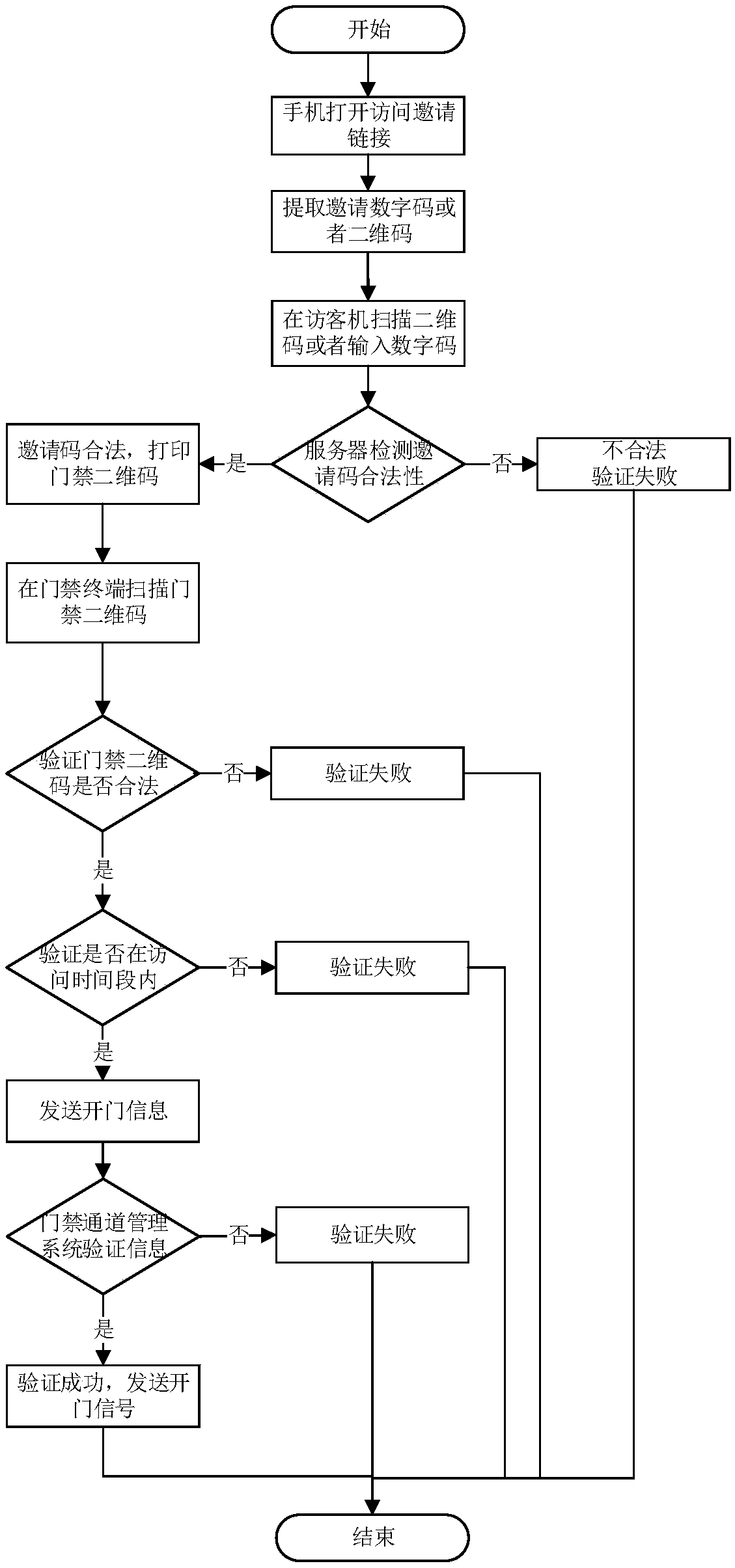
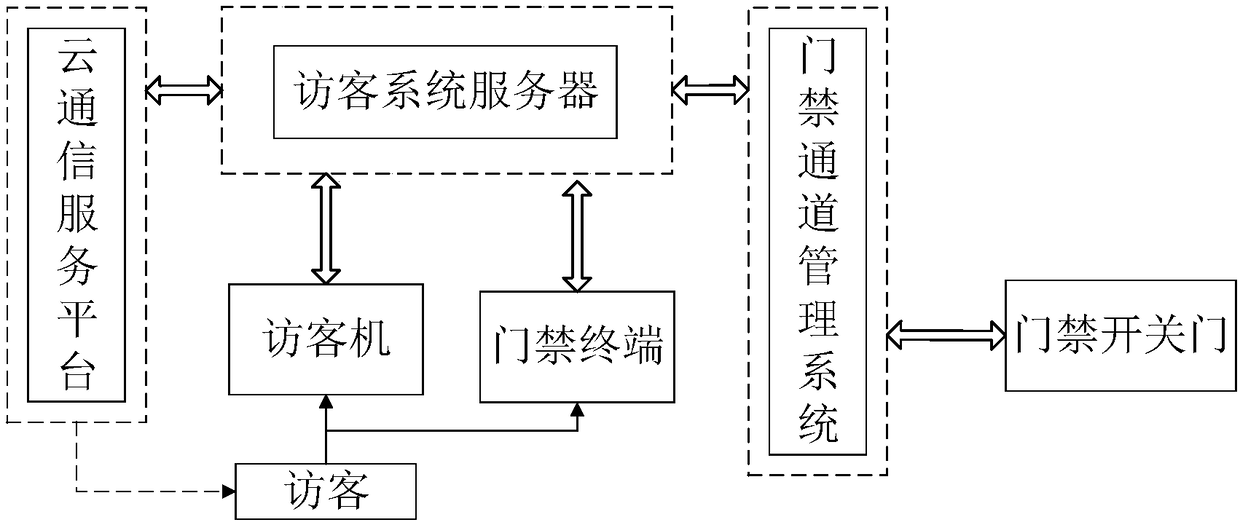
[0033] This application proposes a method for implementing a visitor system based on two-dimensional code identification, such as figure 1 shown, including the following steps:
[0034] S1. Send the invitation information to the visitor in the form of a short message;
[0035] S2. The visitor obtains the access control QR code according to the invitation information;
[0036] S3. Verify at the access control whether the two-dimensional code of the access control meets the requirements for opening the access control. If yes, the verification is successful, and a door opening signal is sent to the corresponding access control; otherwise, the verification fails.
[0037] The invitation information includes at least one of an invitation two-dimensional code and an invitation digital code. In this embodiment, the short message sent to the visitor includes a link of the visit invitation, and the link is clicked to extract the invitation information, and the invitation information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com