Trusted platform connection method
A connection method and platform technology, applied in the field of computer security, can solve problems such as unguaranteed reliability of access platform behavior, unknown vulnerabilities, and unguaranteed reliability of connection platform
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
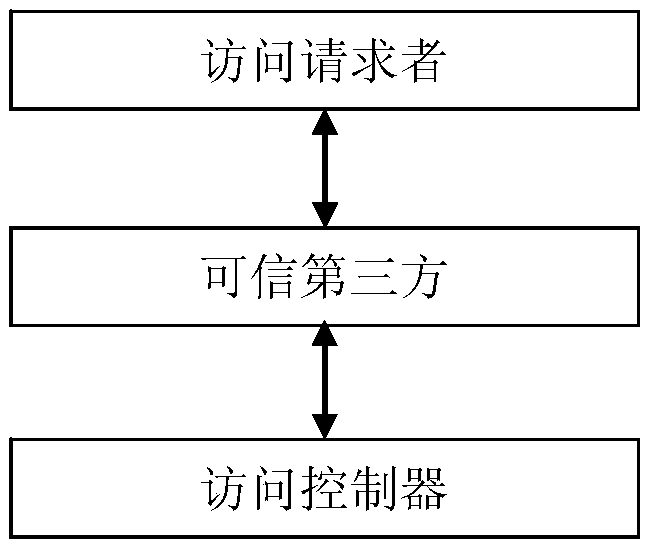
[0035] This embodiment proposes a trusted platform connection system, such as figure 1 As shown, it includes an access requester, an access controller, and a trusted third party, wherein the access requester and the access controller perform two-way identity authentication and trusted platform evaluation through the trusted third party, and the system specifically include:
[0036] (1) Access requester
[0037] The functions of the access requester mainly include: initiating a network access request, realizing two-way identity authentication with the access controller; collecting the integrity of the Windows access terminal, generating an integrity measurement report, and completing the two-way platform integrity evaluation with the access controller ; At the same time, collect Windows application behavior, generate a corresponding measurement report, and send it to the policy manager.
[0038] The access requester includes the following functional modules: Windows access re...
Embodiment 2
[0068] Based on a trusted platform connection system proposed in Embodiment 1, this embodiment describes its software system architecture level, the system includes a network access control layer, a trusted platform evaluation layer, an integrity measurement layer and a behavior collection layer , the above system architecture layer specifically includes:
[0069] (1) Network access control layer
[0070] The functions of the network access control layer mainly include the two-way identity authentication of the Windows access requester and the Windows access controller with the help of the trusted authentication center, and the access control is realized according to the authentication result and the evaluation strategy of the evaluation layer.
[0071] (2) Trusted platform evaluation layer
[0072] The trusted platform evaluation layer mainly realizes platform integrity evaluation and verification of Windows access terminals and server access points. A trusted certificate a...
Embodiment 3
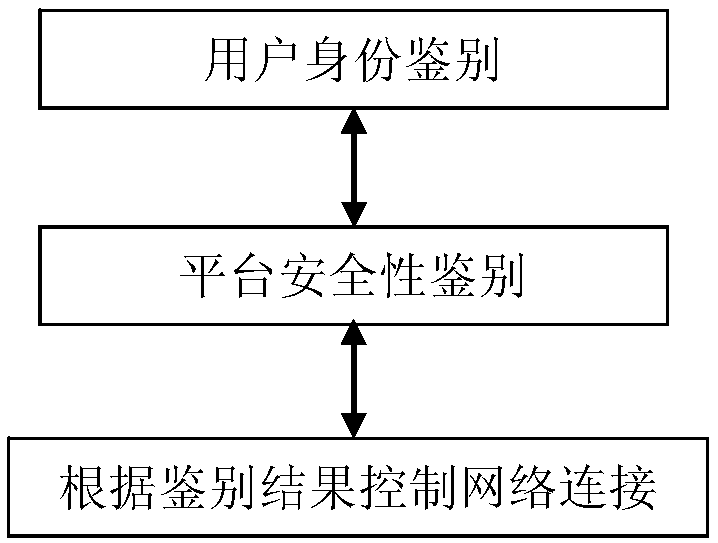
[0078] Based on the trusted platform connection system in Embodiment 1 and the system software architecture in Embodiment 2, this embodiment proposes a trusted platform connection method, such as figure 2 As shown, it includes three major steps of user identity authentication, platform security authentication, and network connection control according to the authentication result. The detailed flow of the method is as follows:
[0079] 1) Connection preparation: Before the connection starts, the Windows terminal and the server access end perform integrity collection by binding TPCM-related interfaces;
[0080] 2) The user sends a network access request to the gateway;
[0081] 3) The user and the gateway perform user identification. Based on the trusted third-party certification center through the key negotiation protocol, the communication key Key is established. After the communication key is established, the user encrypts the relevant information U(id, password) through th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com