Bullet screen verification method and apparatus based on different modes, terminal and storage medium
A verification method and barrage technology, applied in the field of barrage, can solve problems such as inconvenient expansion and maintenance, low maintainability of barrage verification function, complex logic function of barrage verification function, etc., to improve scalability and maintainability, the effect of simplifying logic functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
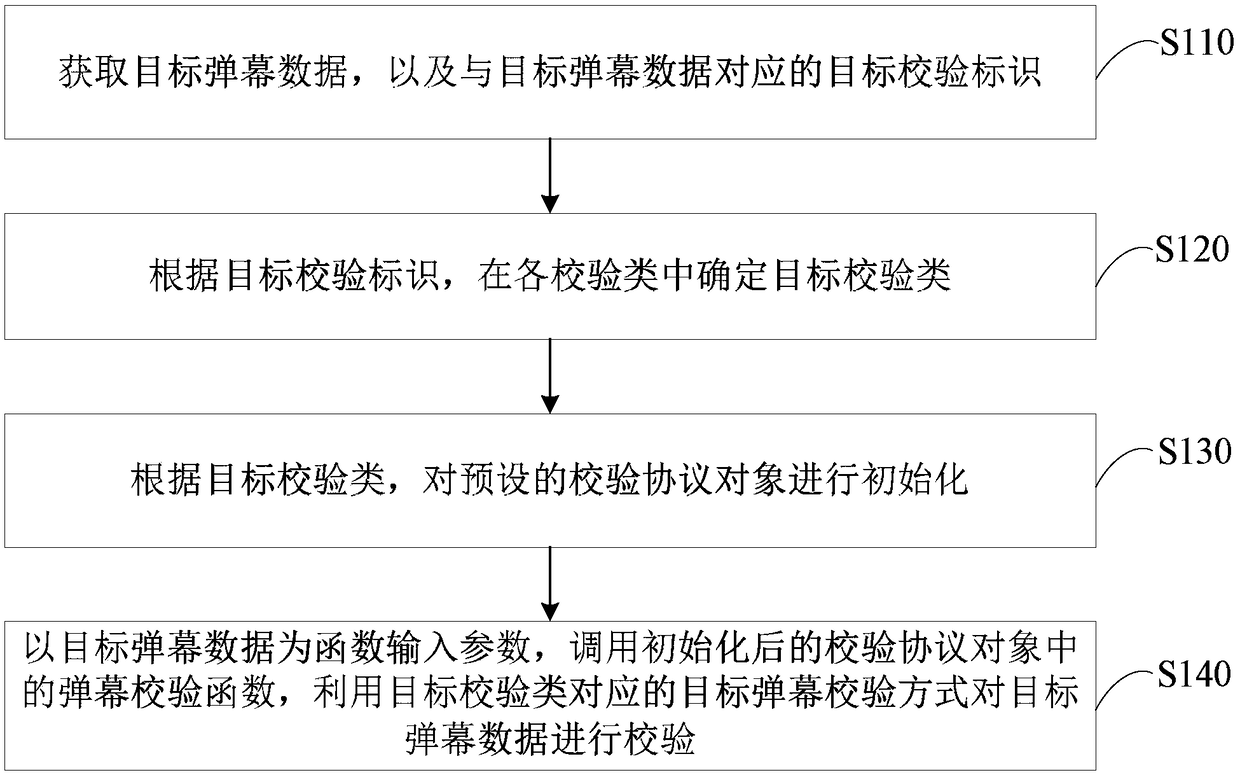
[0030] figure 1 A flow chart of a bullet chatting verification method based on different methods provided in Embodiment 1 of the present invention. This embodiment is applicable to performing bullet chatting data using the target bullet chatting verification method in different bullet chatting verification methods. Integrity verification, especially in the application scenario where the bullet chat data is generated according to the preset bullet chat protocol in the bullet chat server, and the generated bullet chat data is verified, and it can also be used in the Android client In the application scenario where the bullet chat data delivered by the bullet chat server is verified. The method can be performed by a barrage verification device based on different methods, the device can be implemented by software and / or hardware, and can be integrated in a barrage server or a terminal with a barrage function equipped with an Android system, For example, intelligent terminals such...
Embodiment 2
[0064] figure 2 It is a flow chart of a bullet chat verification method based on different methods provided by Embodiment 2 of the present invention. On the basis of the above embodiments, the target data structure corresponding to the target bullet chat data is the first preset character in this embodiment The verification process of the target barrage data is described in detail when the string structure is used. The explanations of terms that are the same as or corresponding to those in the foregoing embodiments are not repeated here.
[0065] see figure 2 The barrage verification method based on different methods provided in this embodiment includes the following steps:
[0066] S210. Obtain target barrage data and a target verification identifier corresponding to the target barrage data.
[0067] Wherein, the target data structure corresponding to the target barrage data is the first preset string structure, and the first preset string structure is: the preset start ch...
Embodiment 3
[0095] image 3 A flow chart of a bullet chat verification method based on different methods provided by Embodiment 3 of the present invention. On the basis of the above-mentioned embodiments, the target data structure corresponding to the target bullet chat data is a preset character string embedding When setting the structure, the verification process of the target barrage data is described in detail. The explanations of terms that are the same as or corresponding to those in the foregoing embodiments are not repeated here.
[0096] see image 3 The barrage verification method based on different methods provided in this embodiment includes the following steps:
[0097] S310. Obtain target barrage data and a target verification identifier corresponding to the target barrage data.
[0098]Wherein, the target data structure corresponding to the target barrage data is a preset string nesting structure, and the preset string nesting structure includes: a nesting structure form...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com