Face recognition database construction method, face recognition method, device and equipment
A face recognition and database technology, applied in the field of face recognition database construction, can solve the problems of complicated, inefficient and difficult face recognition process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
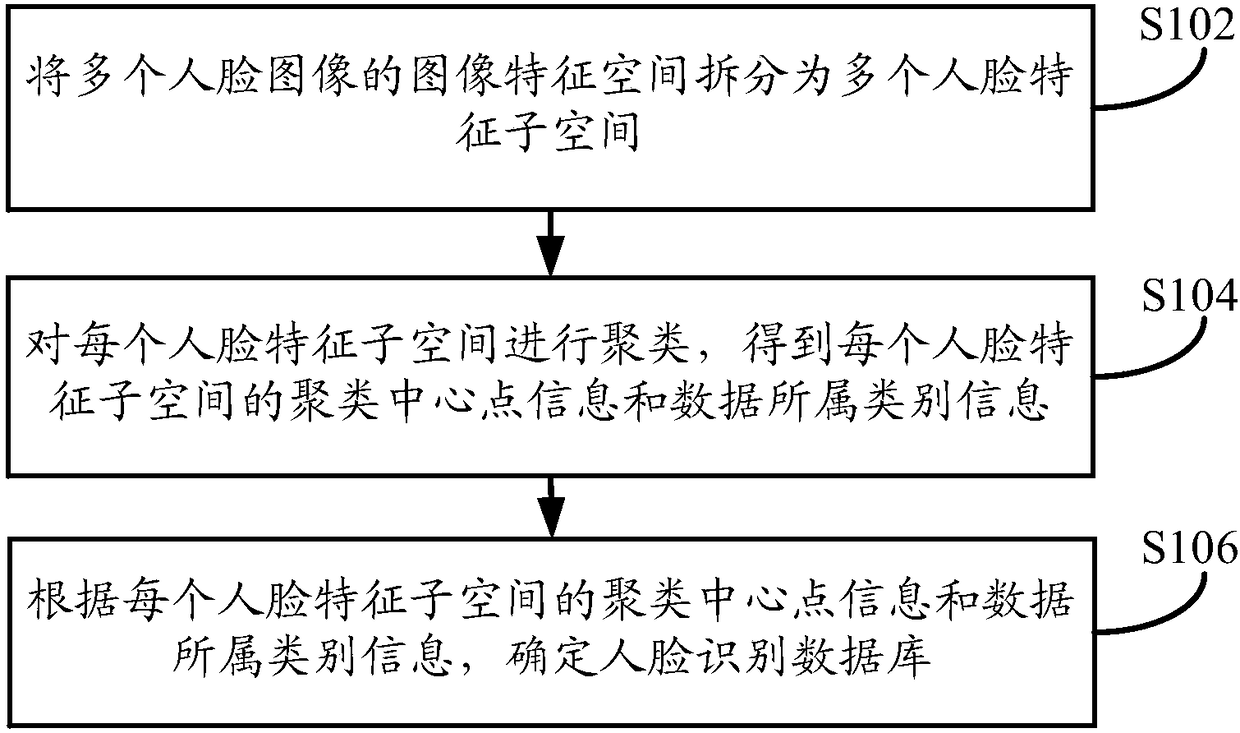
[0112] Such as figure 1 As shown, the embodiment of the present application provides a method for constructing a face recognition database. The execution subject of the method can be a terminal device or a server. The terminal device can be a personal computer, etc., and the server can be an independent server or It is a server cluster composed of multiple servers. In order to improve the construction efficiency of the face recognition database in the embodiments of the present application, the execution subject of the method takes a server as an example for detailed description. The method may specifically include the following steps:
[0113] In step S102, the image feature space of the multiple face images is split into multiple face feature subspaces.
[0114] Among them, multiple facial images may be multiple facial images of different users, and the number of facial images for any user may be one or multiple, such as 10 or 15 facial images. The image feature space can be a ...
Embodiment 2
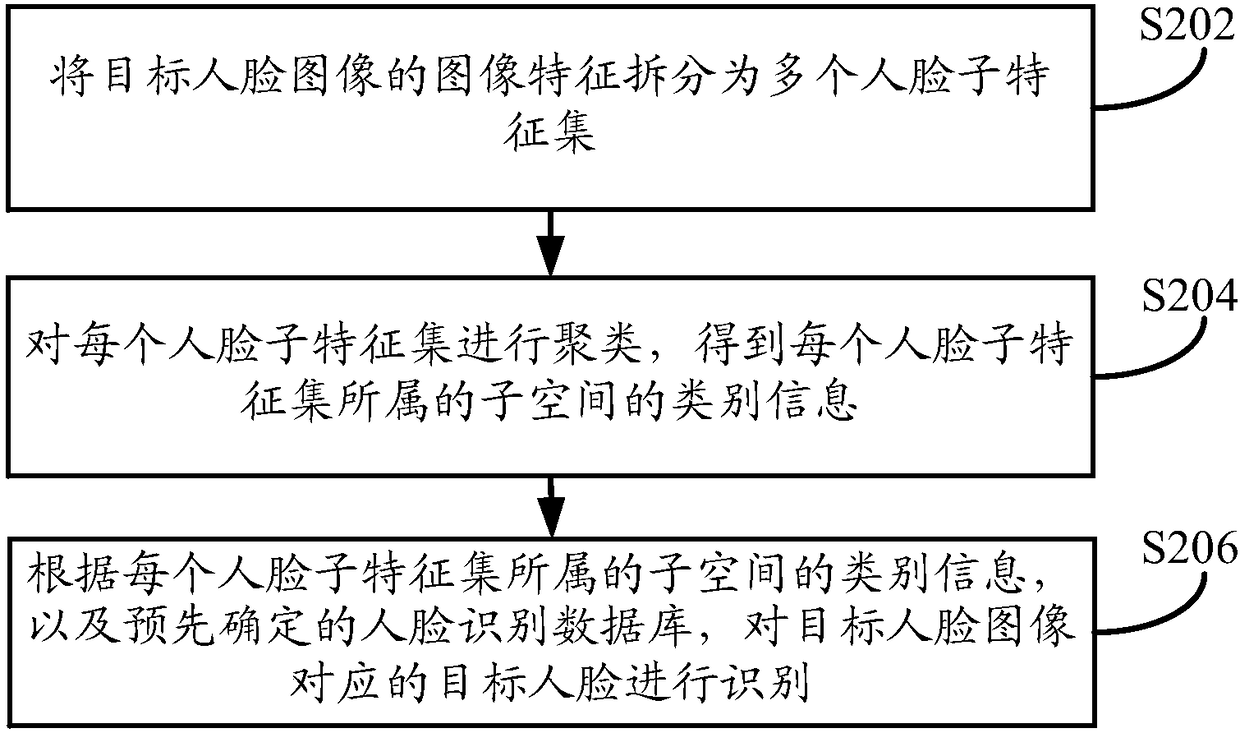
[0136] Such as Figure 4 As shown, the embodiment of the present application provides a face recognition method. The execution body of the method may be a server or the method may be implemented by a terminal device and a server. The terminal device may be a personal computer, etc., and the server may be an independent A server in the, can also be a server cluster composed of multiple servers. In order to improve the construction efficiency of the face recognition database in the embodiments of the present application, the execution subject of the method takes the server as an example for detailed description. For the implementation by the terminal device and the server according to the situation, you can refer to the following related content. Repeat it again. The method specifically includes the following:
[0137] At present, face recognition is a new way for users to verify their identities. Face recognition technology has been used more and more widely due to its higher rec...
Embodiment 3
[0198] The above is the face recognition method provided by the embodiment of the application. Based on the same idea, the embodiment of the application also provides a device for constructing a face recognition database, such as Figure 7 Shown.
[0199] The device for constructing the face recognition database includes: a feature space splitting module 801, a clustering module 802, and a database construction module 803, wherein:
[0200] The feature space splitting module 801 is configured to split the image feature space of multiple face images into multiple face feature subspaces;
[0201] The clustering module 802 is used to cluster each face feature subspace to obtain cluster center point information and data category information of each face feature subspace;
[0202] The database construction module 803 is used to construct a face recognition database according to the cluster center point information of each face feature subspace and the category information of the data.
[020...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com