Method and system for protecting data stream differential privacy based on edge calculation
A differential privacy and edge computing technology, applied in digital data protection, digital transmission systems, computing, etc., can solve the contradiction between data availability and privacy security, can not meet high real-time requirements, can not meet low-latency services and other problems, Achieve the effect of improving system throughput, reducing data transmission, and reducing computing load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, but the protection scope of the present invention is not limited thereby.
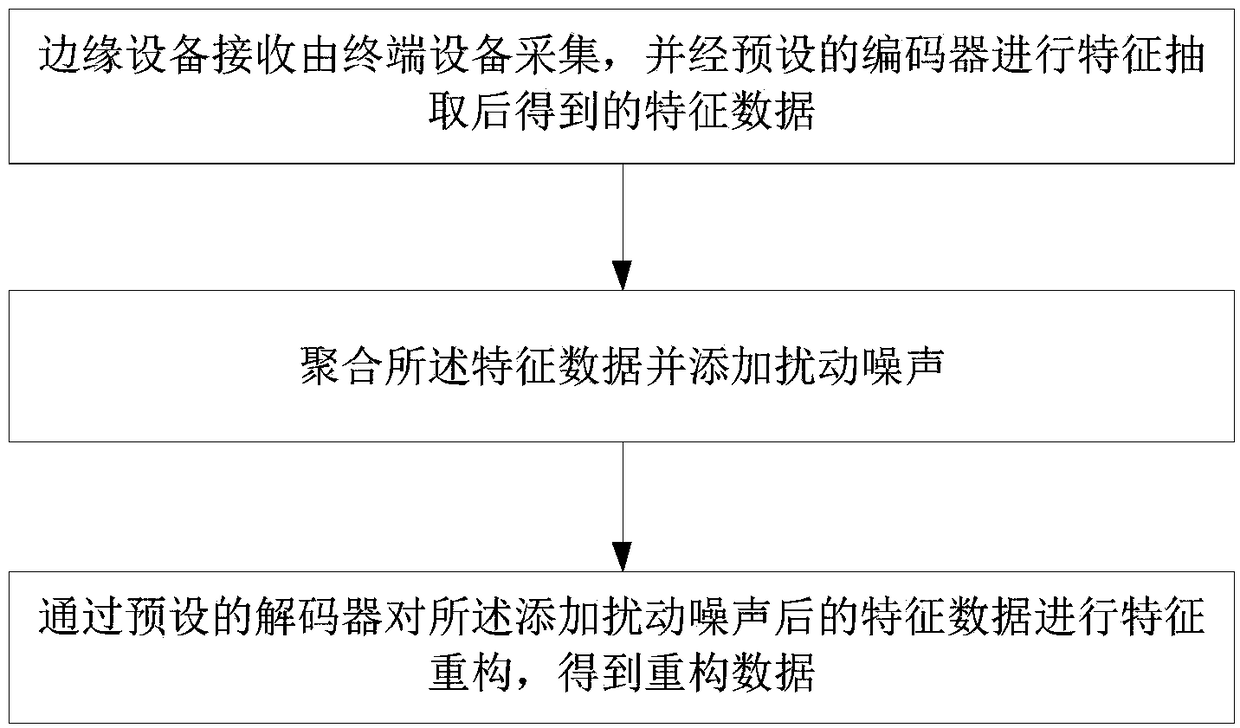
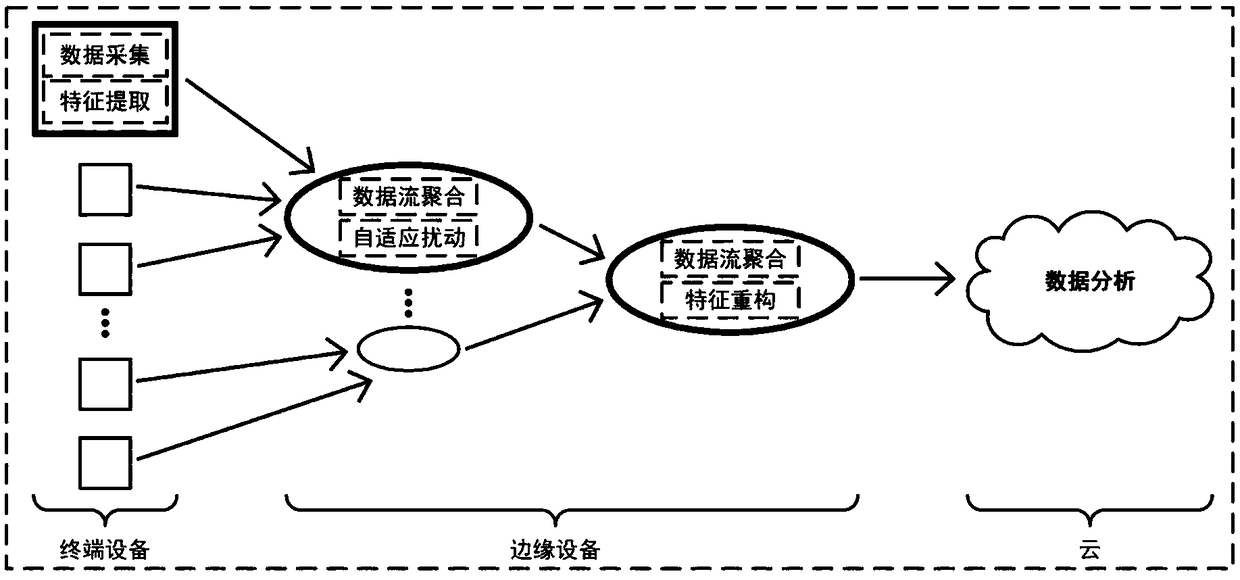
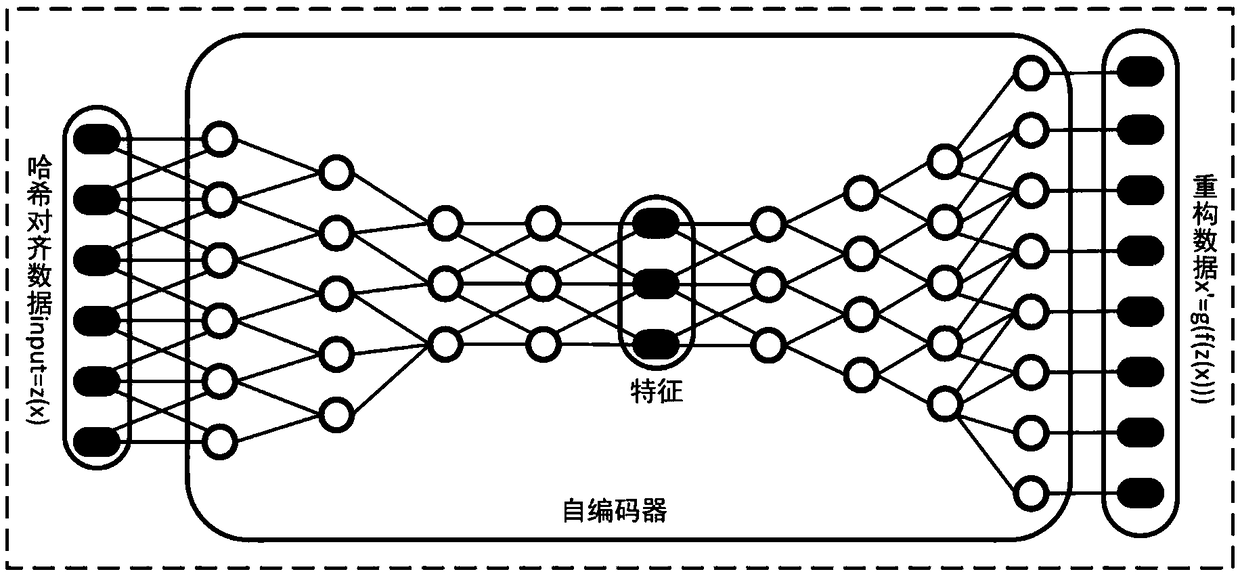
[0044] like figure 1 As shown, the edge computing-based differential privacy protection method for data streams in this embodiment includes: S1. The edge device receives the feature data collected by the terminal device and extracted by a preset encoder; S2. The aggregate The above feature data and add disturbance noise; S3. Perform feature reconstruction on the feature data after adding disturbance noise through a preset decoder to obtain reconstructed data; the encoder and the decoder are for the same self-encoder Encoder and decoder obtained after training.
[0045] In this embodiment, the feature data in step S1 is obtained by the terminal device according to the preset collection time window as a unit, collected within one collection time window, and obtai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com