E-mail communication limiting method and system
A technology of e-mail and mail, applied in the direction of instruments, data processing applications, office automation, etc., can solve the problems of difficult black and white lists, failure to proceed normally, exhaustive enumeration, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
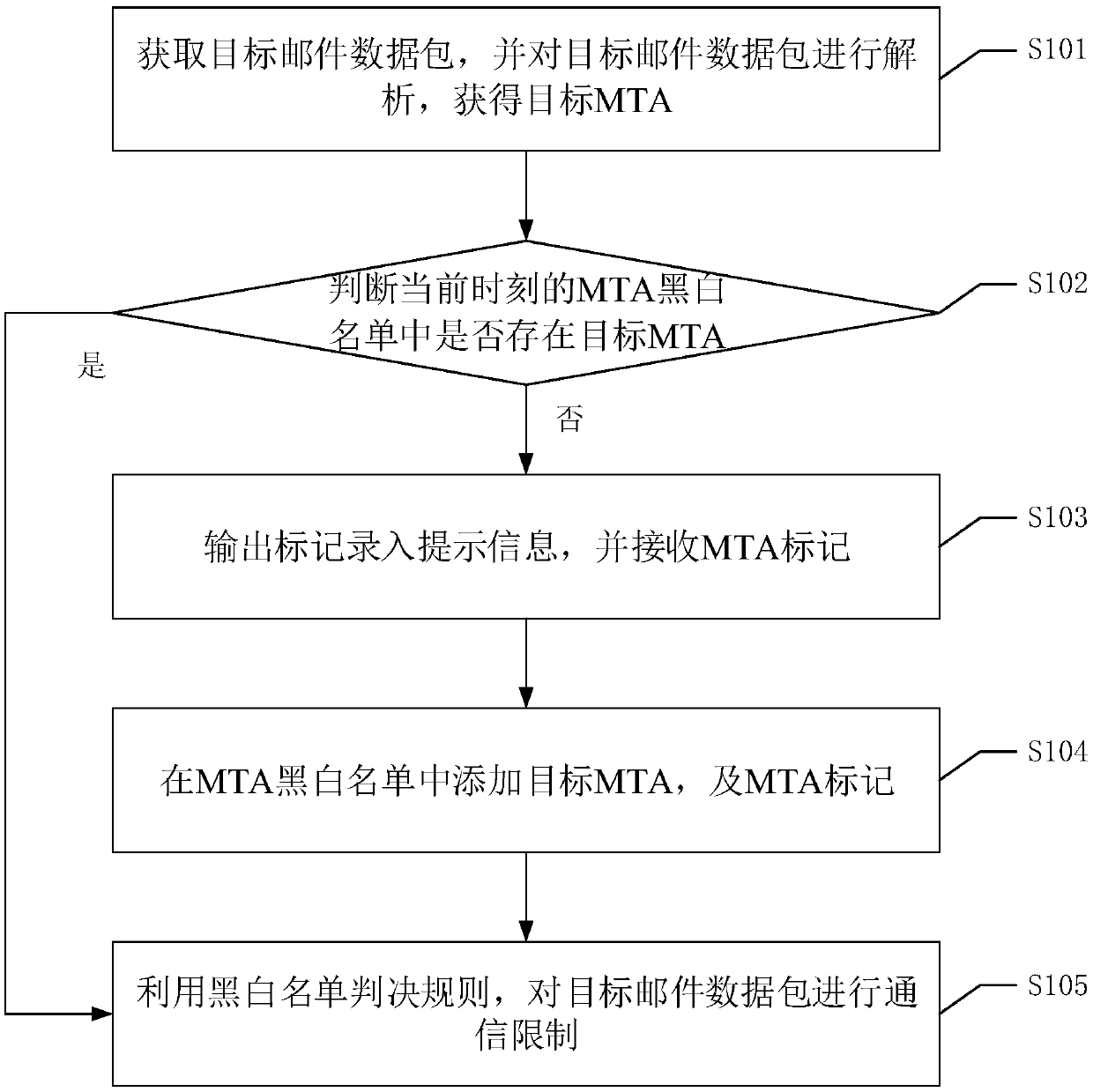
[0048] Please refer to figure 1 , figure 1 It is a flow chart of an e-mail communication restriction method in an embodiment of the present invention, and the method includes the following steps:
[0049] S101. Obtain a target mail data packet, and analyze the target mail data packet to obtain a target MTA.
[0050] In the embodiment of the present invention, the mail server to be protected can be configured, specifically, the IP of the mail server to be detected, the service port, and the MTA of the mail server can be configured. Programs used to send and receive mail are generally referred to as mail user agent MUA (Mail User Agent). The program that forwards letters from MUA to designated users is generally called MTA (Mail Transfer Agent, Internet mail transfer agent). On linux / Unix systems, the most famous MTAs include programs such as sendmail and qmail. That is, the MTA is an email transmission agent, which is specifically represented by the part after @ in an email...
Embodiment 2
[0076] In order to facilitate those skilled in the art to better understand the email communication restriction method provided by the embodiment of the present invention, the email communication restriction method provided by the embodiment of the present invention will be described in detail below with reference to specific application scenarios as examples.
[0077] First, configure the mail server information: configure the mail server IP, service port, and mail server MTA to be detected. For the convenience of subsequent expression, set the mail server MTA of the protected object to M.
[0078] If M is abc, that is, the part after @ in the e-mail is aaa.
[0079] After the configuration is complete, traffic mirroring can be used to obtain the traffic passing through the mail server to be detected according to the configuration information of the mail server.
[0080] Analyze the obtained traffic. Specifically, according to the mail protocol, the recipient and sender inf...
Embodiment 3
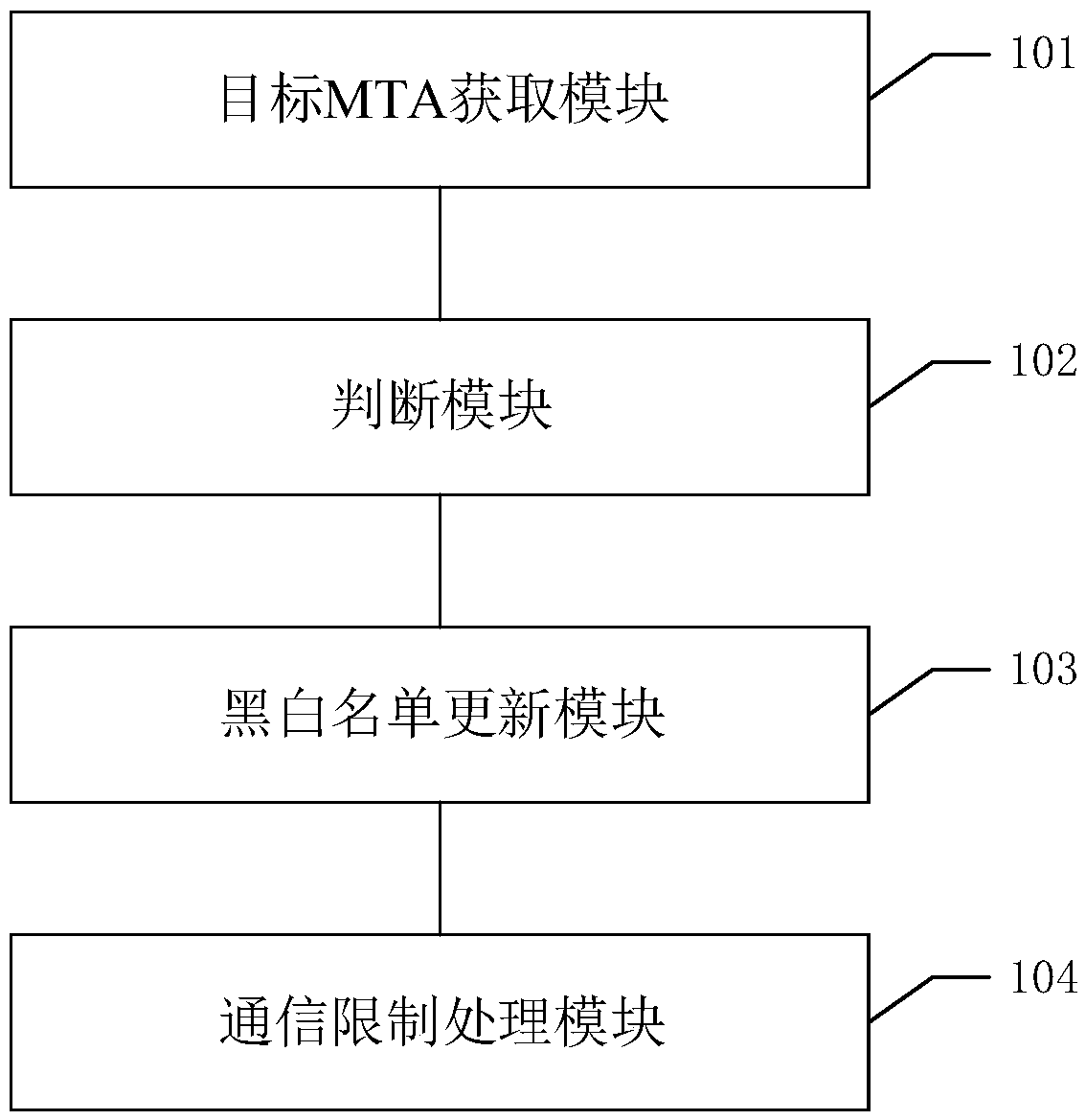
[0090] Corresponding to the above method embodiment, the embodiment of the present invention also provides an email communication restriction system, and the email communication restriction system described below and the email communication restriction method described above can be referred to in correspondence with each other.
[0091] see figure 2 As shown, the system includes the following modules:
[0092] The target MTA acquisition module 101 is used to obtain the target mail data packet, and analyze the target mail data packet to obtain the target MTA;
[0093] Judgment module 102, for judging whether there is target MTA in the MTA black and white list of current moment;
[0094] Black and white list update module 103, for when there is no target MTA in the MTA black and white list, then output the mark entry prompt information, and receive the MTA mark; Add the target MTA and the MTA mark in the MTA black and white list;
[0095] The communication restriction process...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com