Mobile communication method for linear credible token
A mobile communication and trusted technology, which is applied in wireless communication, secure communication devices, and key distribution, can solve problems that affect the security performance of the physical layer and cannot achieve results, and achieve simplified design and implementation difficulty, good secure communication performance, and protection The effect of identity security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
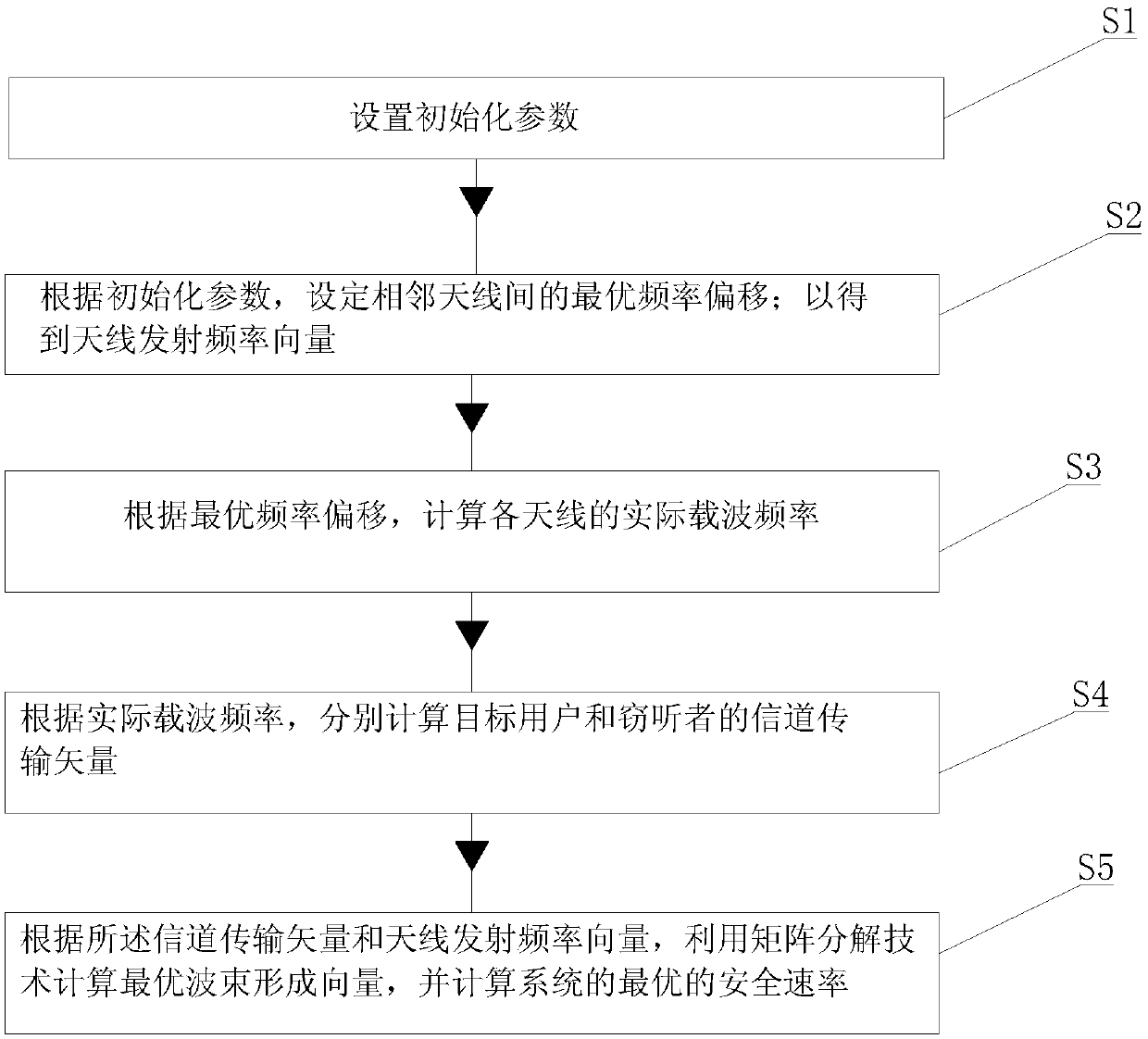
[0020] Such as figure 1 as shown, figure 1 It is a schematic structural diagram of a linear trusted token mobile communication method proposed by the present invention.
[0021] 2. Reference figure 1 , a mobile communication method of a linear trusted token proposed by the present invention, comprising the following specific steps:
[0022] S1, setting initialization parameters;
[0023] First, a master key and network public parameters are generated through a PKG; wherein, the master key is kept by the PKG itself; the network public parameters are disclosed to all nodes in the network; The public key and private key of node; And described public key is disclosed to all nodes; Described private key is disclosed to corresponding node; Shared key agreement step: adopt IBE agreement to realize the shared secret between source node and destination node Key and communication sequence number negotiation, wherein said shared key is called key; Routing discovery step: according to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com