A security detection method and system for remote login risk control
A technology of security detection and risk control, applied in the field of network security, can solve problems such as being easily logged in by others, email security issues, and inability to judge, so as to reduce the risk of theft and improve the user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0066] refer to Figure 1-8 .
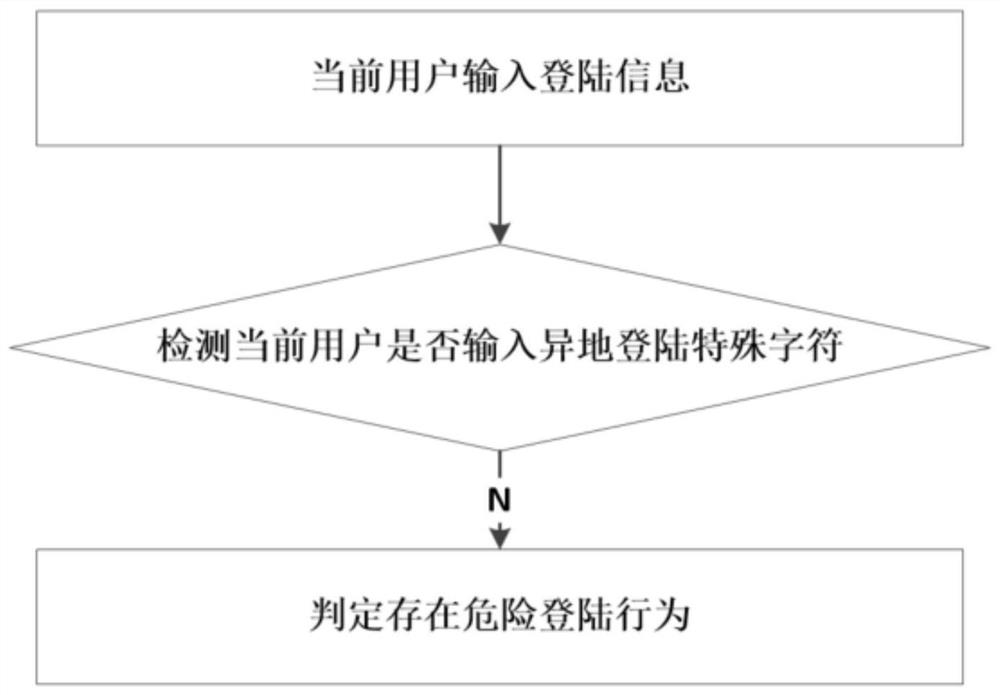
[0067] A safety detection method for remote login risk control, comprising:
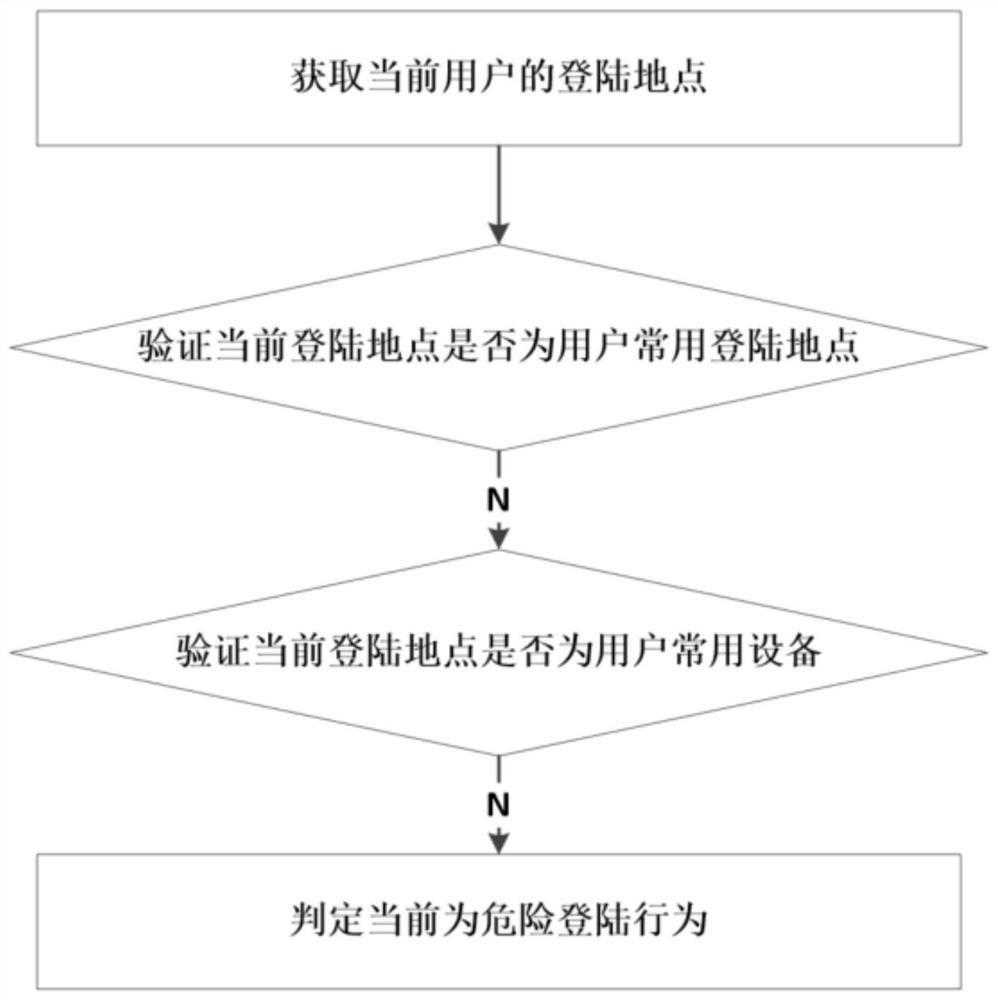
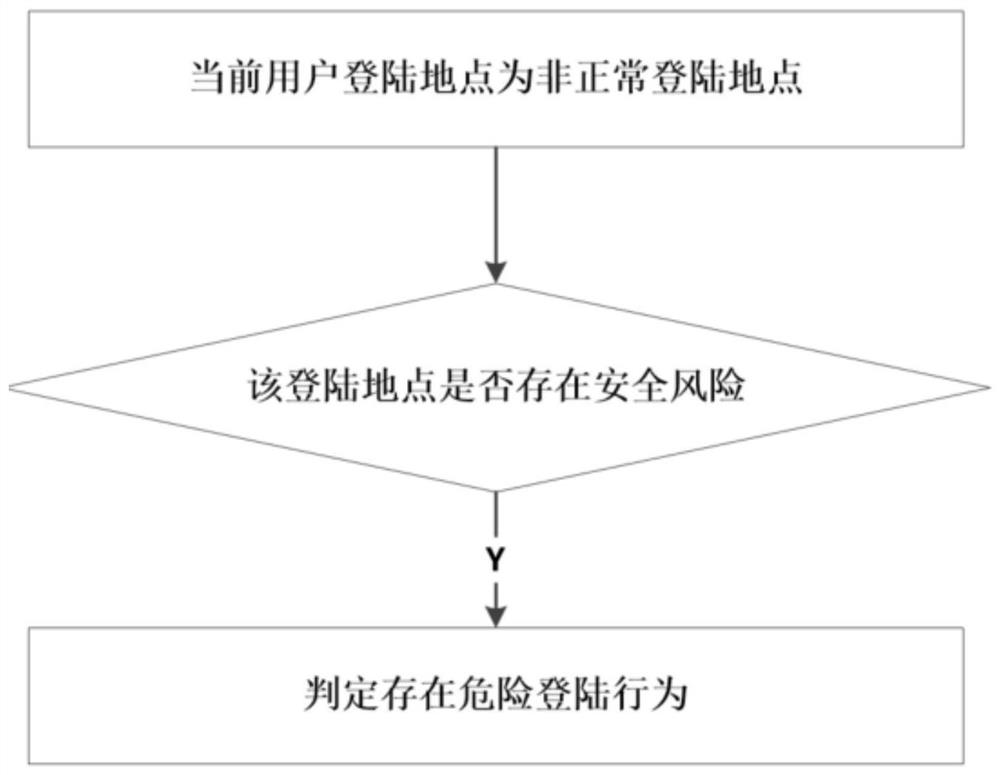
[0068] Obtain the login location of the current user, and verify whether the current login location is the user's usual login location. The login location includes the user's login IP address. If the user's current login IP address is inconsistent with the usual address, it is a remote login. As an implementation, the current location of the device can be verified, and if the current location is inconsistent with the usual login location, it is a remote login.
[0069] If it is not the user's usual login location, it is detected whether the user's login device is a commonly used device. Commonly used equipment detection is the identification code of the detection equipment, and the equipment has a unique identification code.
[0070] If it is not the user's frequently used device, obtain the current location of the user's frequently used device. If there is no use...
Embodiment 2
[0099] A safety detection method and system for remote login risk control, comprising:
[0100] The login location obtaining module is configured to obtain the user's login location.
[0101] The device detection module is used to detect whether the currently logged-in device is a common device.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com