Data access method and device, server and storage medium
A data access and server technology, applied in the computer field, can solve problems such as performance degradation and concurrent performance impact, and achieve the effects of reducing blocking conflicts, improving concurrent performance, and reducing fierce competition.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
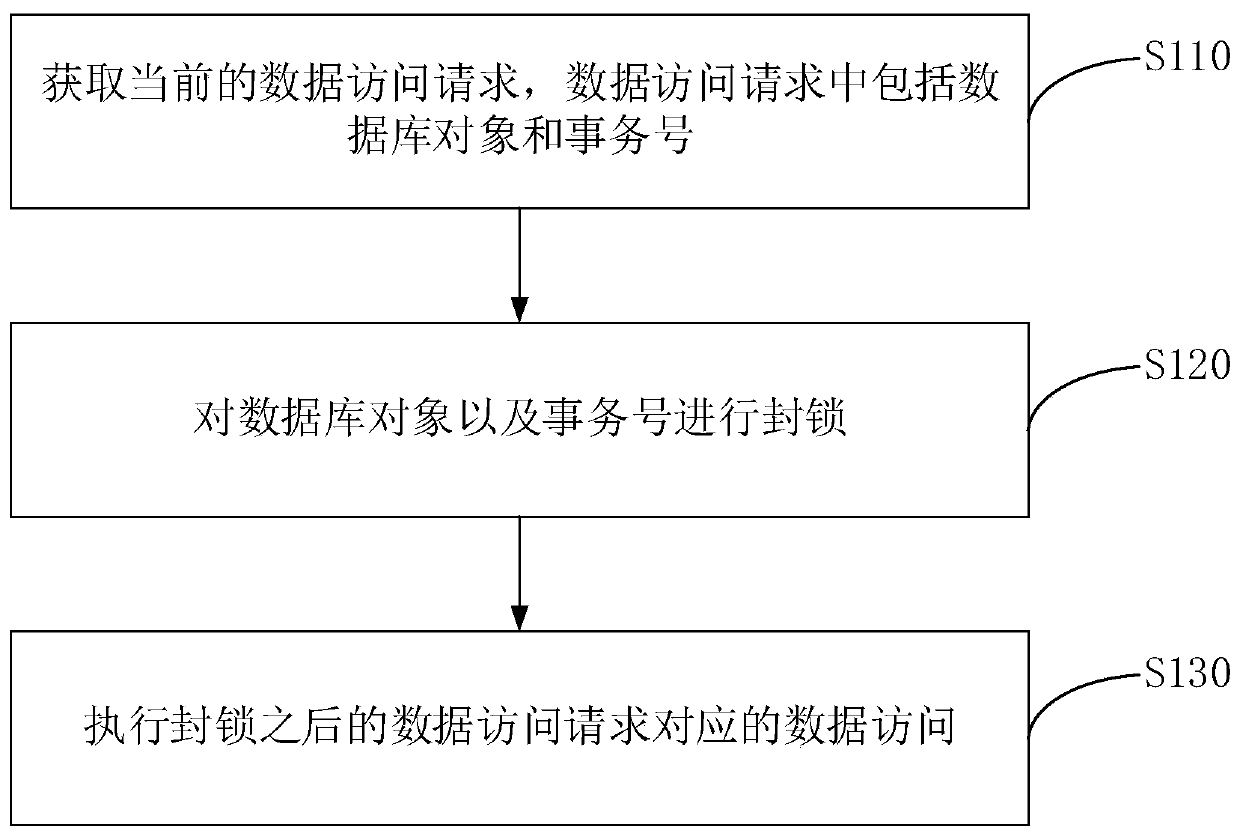
[0037] figure 1 It is a flow chart of the data access method in Embodiment 1 of the present invention. This embodiment is applicable to the situation of implementing data access in a database. The method can be executed by a data access device, which can be implemented in the form of software and / or hardware , for example, the device may be configured in a server. Such as figure 1 As shown, the method may specifically include:
[0038] S110. Obtain a current data access request, where the data access request includes a database object and a transaction number.
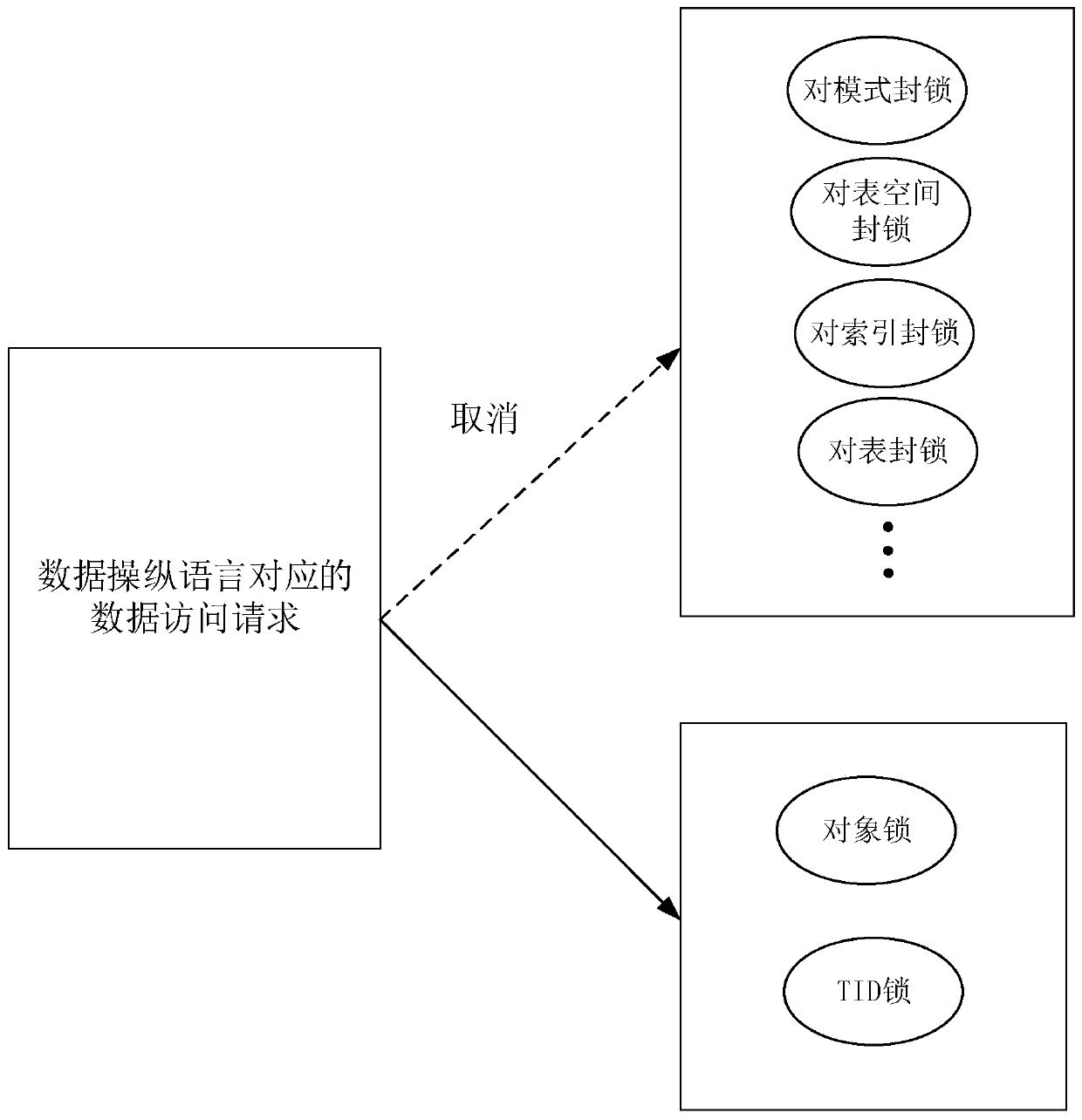
[0039] Wherein, the data access request is an access request to resources in the database, and the data access request in this embodiment may include an access request corresponding to a Data Manipulation Language (Data Manipulation Language, DML) and a Data Definition Language (Data Definition Language, DDL) corresponding to the access request. The database object is the main component of the database. In this emb...
Embodiment 2
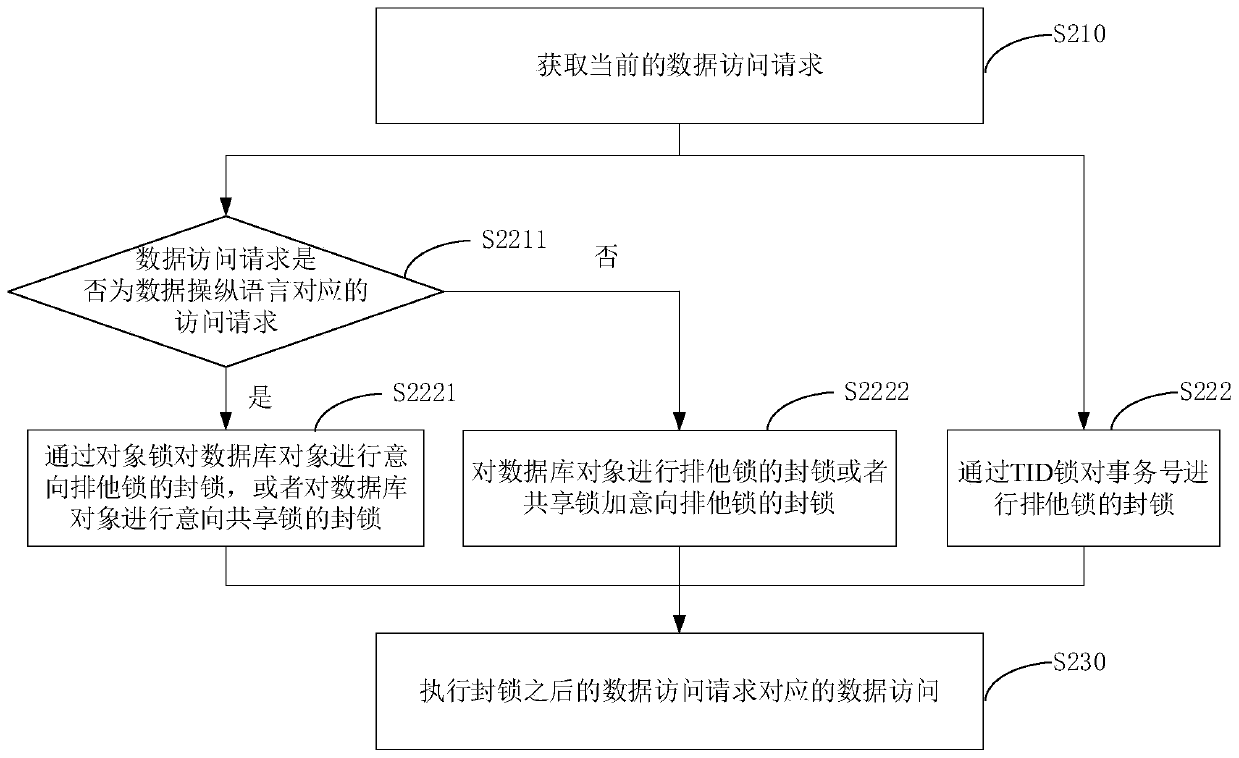
[0054] image 3 It is a flow chart of the data access method in Embodiment 2 of the present invention. On the basis of the foregoing embodiments, this embodiment further specifically describes the foregoing data access method. Correspondingly, such as image 3 As shown, the method of this embodiment specifically includes:
[0055] S210. Obtain a current data access request.
[0056] Wherein, the data access request includes the database object and the transaction number. The data access request in this embodiment may include an access request corresponding to a Data Manipulation Language (Data Manipulation Language, DML) and an access request corresponding to a Data Definition Language (Data Definition Language, DDL). The database object is the main component of the database. In this embodiment, the database object may include tables, table spaces, schemas, indexes, views, rules, and so on. The transaction number is an identifier created for each active transaction in the...
Embodiment 3
[0077] Figure 5 It is a schematic structural diagram of a data access device in Embodiment 3 of the present invention, and this embodiment is applicable to the situation of implementing data access in a database. The data access device provided by the embodiment of the present invention can execute the data access method provided by any embodiment of the present invention, and has corresponding functional modules and beneficial effects for executing the method. The device specifically includes a request acquisition module 310, a blocking module 320 and an execution module 330, wherein:
[0078] A request obtaining module 310, configured to obtain a current data access request, where the data access request includes a database object and a transaction number;
[0079] Blocking module 320, configured to block database objects and transaction numbers;
[0080] The executing module 330 is configured to execute data access corresponding to the blocked data access request.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com