Sensitive information detection method and device and electronic device
A technology for sensitive information and detection methods, applied in the computer field, can solve problems such as false positives of detection results, achieve the effects of reducing data volume, improving screening efficiency, and reducing quantity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
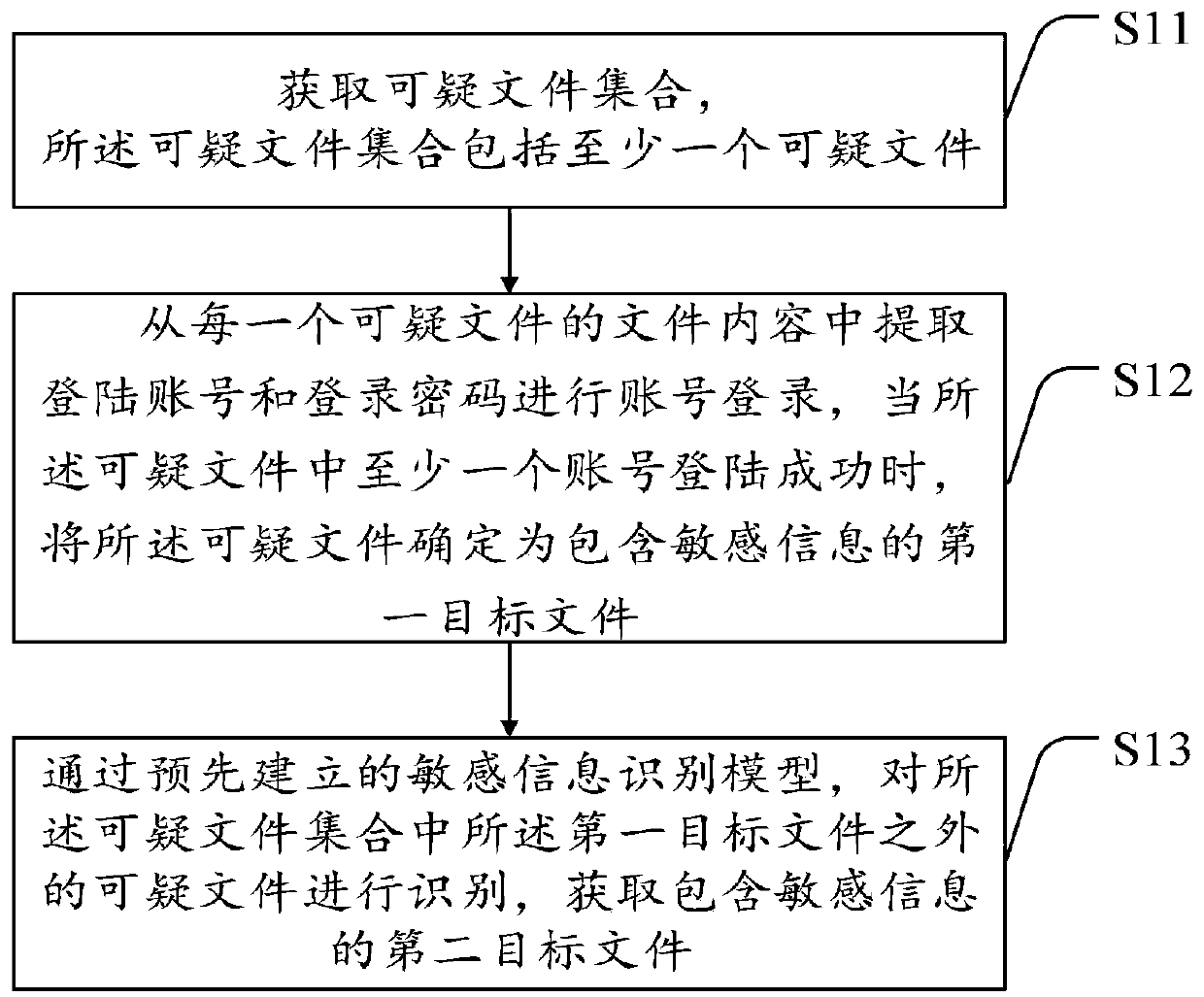
[0055] As mentioned above, leaks of sensitive information on the Internet are not uncommon. For example, GitHub has been the hardest hit area for leaks of sensitive information. Some staff who lack security awareness may submit sensitive information such as the company's important program codes, managed accounts and passwords to various platforms, resulting in the leakage of sensitive information, thus bringing a series of security risks to enterprises and individuals. Therefore, a scanning tool is needed to detect whether the information submitted by the staff of the enterprise contains sensitive information of the enterprise.
[0056]The currently commonly used scanning tools, in the whole detection process, first use the scanning tool to perform fuzzy query of sensitive information keywords to determine the suspected items related to the keywords; then further screen the suspected items to obtain information related to sensitive A collection of suspicious files matching inf...
Embodiment 2
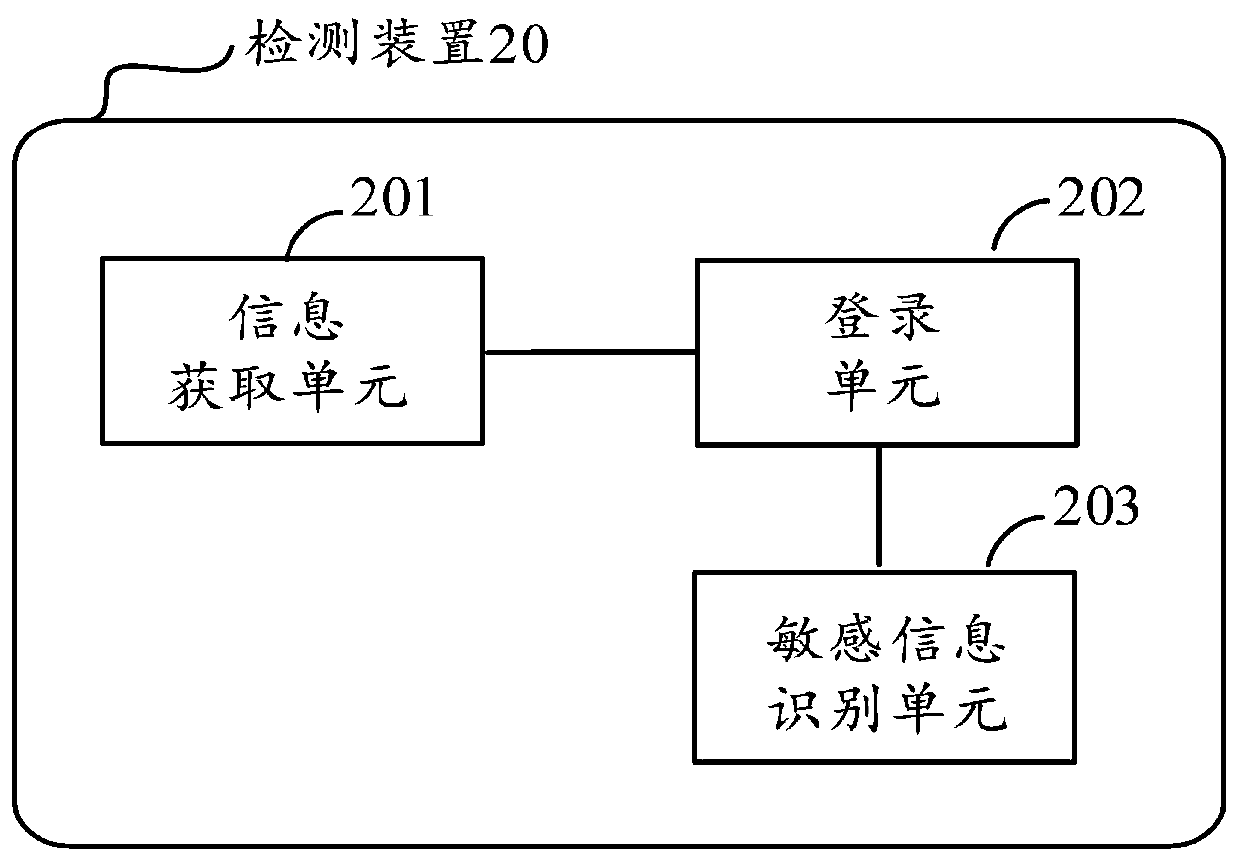
[0091] Based on the same inventive concept as that of Embodiment 1, Embodiment 2 of the present invention provides a sensitive information detection device. For the description of each word mentioned in Embodiment 2, if there is any unclear, you can refer to Embodiment 1 . like figure 2 As shown, the device 20 includes: an information acquisition unit 201, a login unit 202, and a sensitive information identification unit 203, wherein:
[0092] An information acquiring unit 201, configured to acquire a set of suspicious files, where the set of suspicious files includes at least one suspicious file;
[0093] The login unit 202 is configured to extract the login account number and login password from the file content of each suspicious file to log in the account, and when at least one account in the suspicious file logs in successfully, determine the suspicious file as the first file containing sensitive information an object file;
[0094] The sensitive information identific...
Embodiment 3
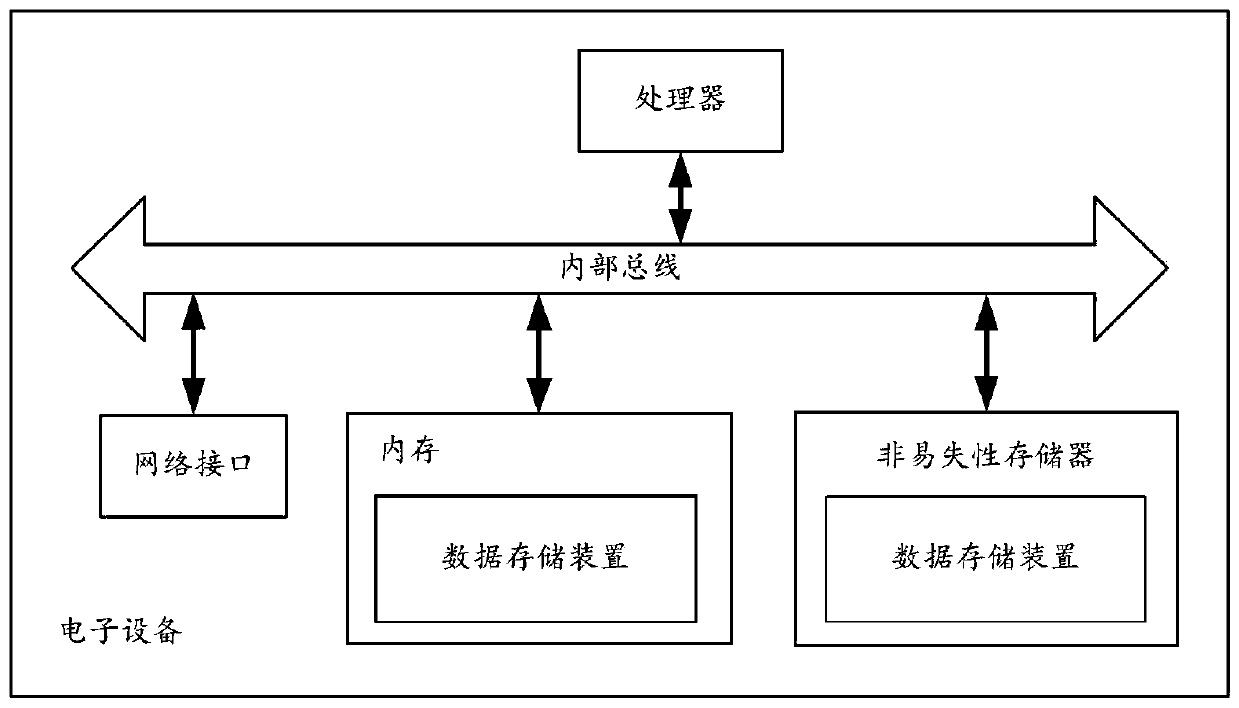
[0105] Based on the same inventive concept as that of Embodiment 1, Embodiment 3 of the present invention provides a schematic structural diagram of an electronic device of an embodiment. Please refer to image 3 , at the hardware level, the electronic device includes a processor, and optionally also includes an internal bus, a network interface, and a memory. Wherein, the memory may include a memory, such as a high-speed random-access memory (Random-Access Memory, RAM), and may also include a non-volatile memory (non-volatile memory), such as at least one disk memory. Of course, the electronic device may also include hardware required by other services.
[0106] The processor, the network interface and the memory can be connected to each other through an internal bus, which can be an ISA (Industry Standard Architecture, industry standard architecture) bus, a PCI (Peripheral Component Interconnect, peripheral component interconnection standard) bus or an EISA (Extended Indust...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com