A websocket-based ssh multi-channel tcp proxy method
A multi-channel, channel technology, applied in the field of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
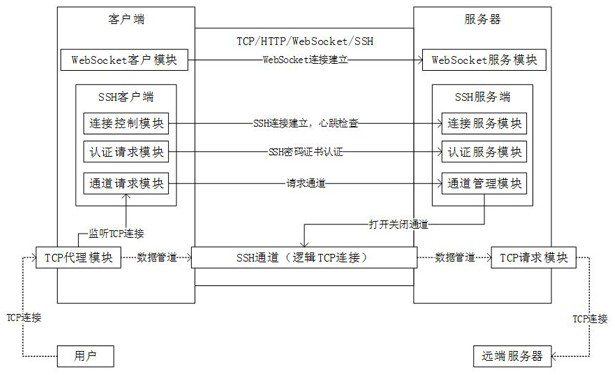
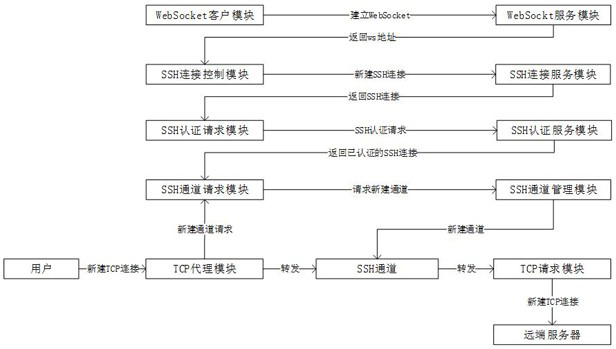
[0055]The present invention is realized through the following technical solutions, as Figure 1-Figure 2 As shown, a WebSocket-based SSH multi-channel TCP proxy method specifically includes the following steps:
[0056] Step F1: the client establishes a WebSocket connection with the server;
[0057] Step F2: the client and the server use the established WebSocket connection to establish an SSH connection;
[0058] Step F3: The client establishes a TCP proxy according to the configuration and waits for the TCP connection;
[0059] Step F4: The user accesses the address and port of the client for TCP access, creates a new TCP connection and opens the SSH channel, and the client sends the TCP connection data stream to the server through the SSH channel;
[0060] Step F5: The server monitors the sending and receiving information, creates a new channel, and receives the transfer proxy configuration rules of the client; sends out a TCP connection request according to the proxy con...
Embodiment 2
[0066] This embodiment is further optimized on the basis of the above embodiments, such as Figure 1-Figure 2 As shown, the step F1 specifically includes the following steps:
[0067] Step F11: the HTTP server on the server monitors and supports WebSocket upgrade;
[0068] Step F12: The client connects to the HTTP server listening port of the server, and the client and the server negotiate to upgrade to a WebSocket connection.
[0069] The client includes a WebSocket client module, and the server includes a WebSocket service module; the function of the WebSocket client module is: responsible for creating a new WebSocket connection, providing cache for the data stream carried, copying the data stream, and connecting to the SSH client; The functions of the WebSocket service module described above are: monitor and be responsible for receiving WebSocket connection requests, provide cache for the carried data stream, copy the data stream, and connect to the SSH server.
[0070] I...
Embodiment 3
[0073] This embodiment is further optimized on the basis of the above embodiments, such as Figure 1-Figure 2 As shown, the step F2 specifically includes the following steps:
[0074] Step F21: After the server successfully establishes the WebSocket connection, use the WebSocket connection to establish an SSH server on the server;
[0075] Step F22: The SSH server establishes and loads an SSH connection service module, an SSH authentication service module, and an SSH channel management module;
[0076] Step F23: the SSH authentication service module loads the authentication configuration information of the server, and waits for a connection request from the client;
[0077] Step F24: After successfully establishing the WebSocket connection, the client uses the WebSocket connection to establish an SSH client at the client;
[0078] Step F25: The SSH client establishes and loads an SSH connection control module, an SSH authentication request module, and an SSH channel request ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com