A searchable database security encryption system
A security encryption and database technology, applied in digital data protection, electronic digital data processing, special data processing applications, etc., can solve the problem that ciphertext cannot directly execute SQL operations, and achieve the effect of protecting data privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in further detail below in conjunction with specific examples, but the scope of the present invention is not limited in any way.
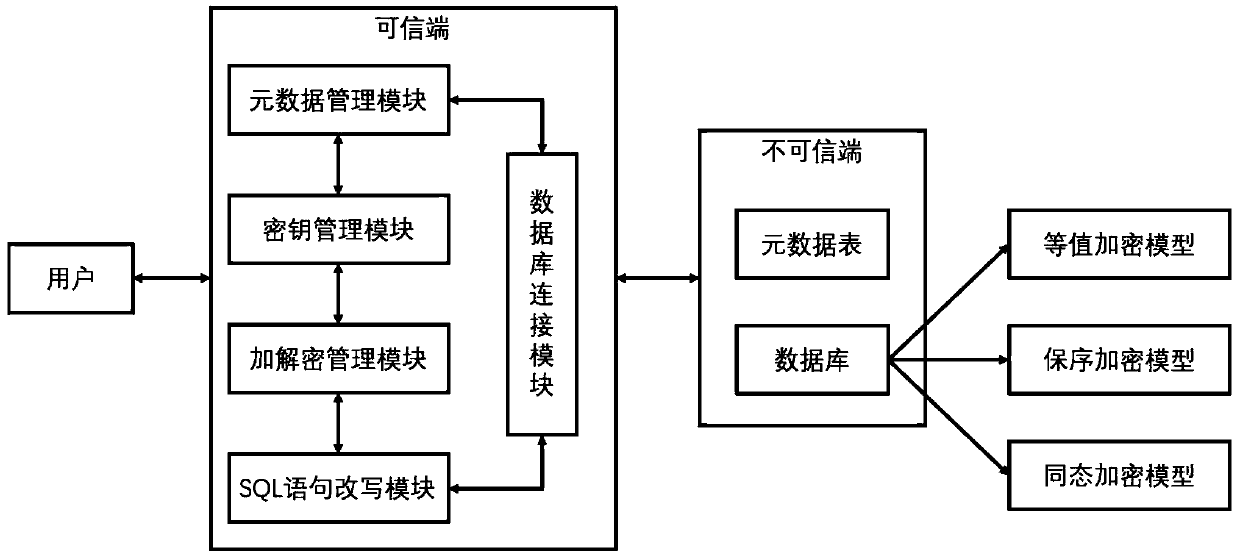
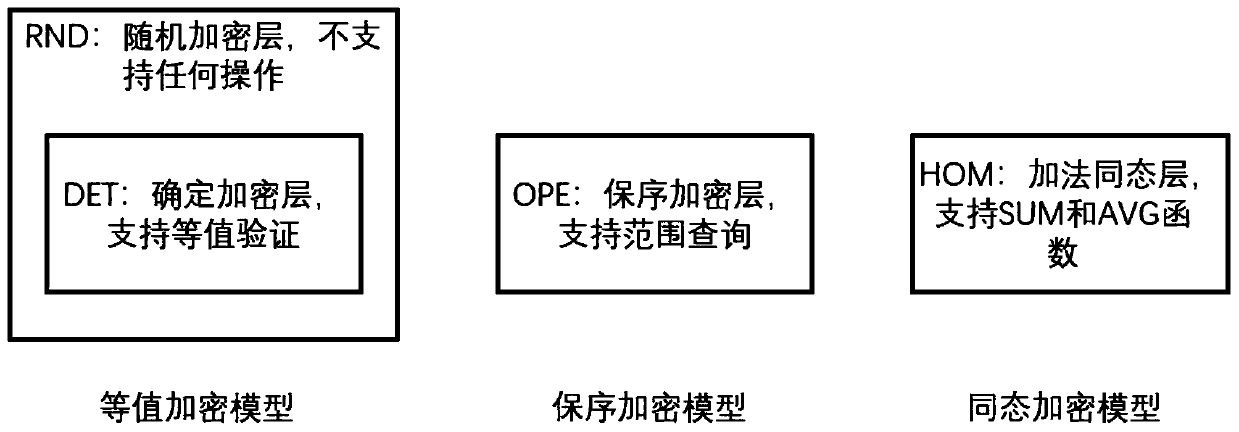
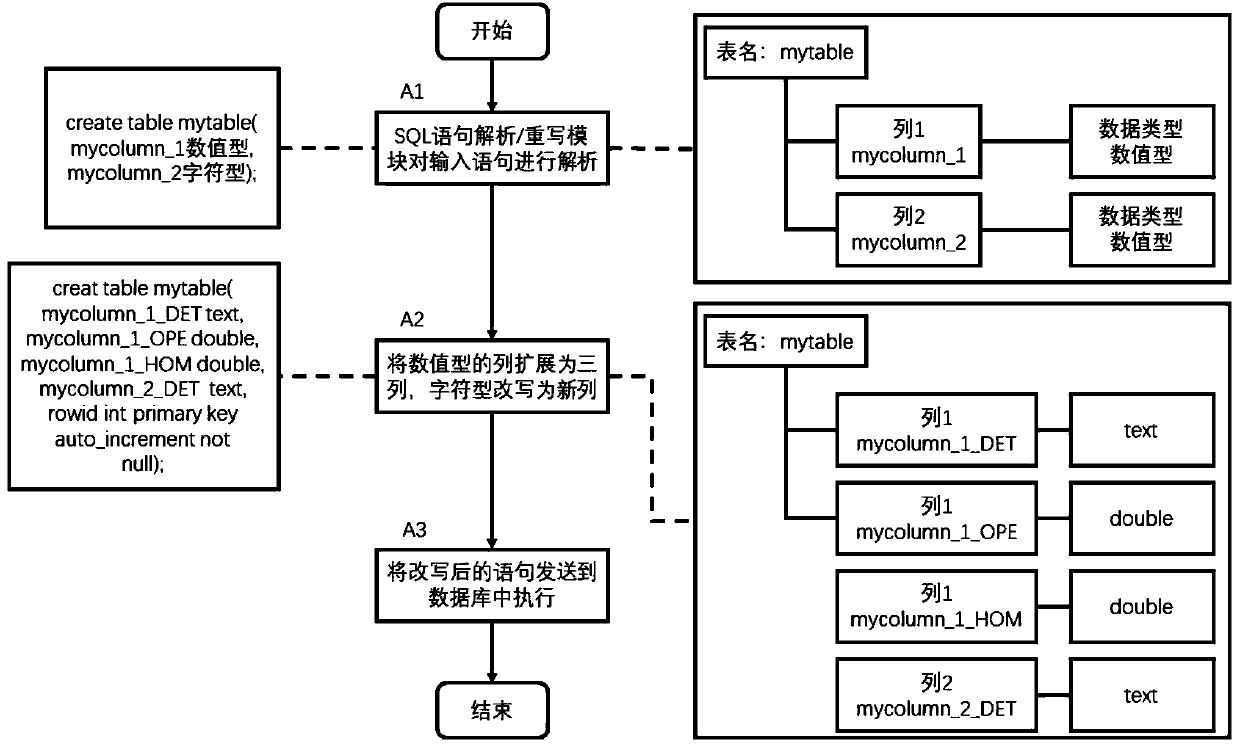
[0036] Design idea of the present invention: the searchable database security encryption system regards the database server as an untrusted terminal. The user enters the SQL statement, and the system encrypts the secret-related plaintext data into ciphertext and stores it on the server side. When the SQL statement is executed, the system rewrites the statement, hides the column names and encrypts the plaintext in it, and at the same time dynamically adjusts the encryption model in the database so that the rewritten statement can be directly executed on the ciphertext.
[0037] figure 1 Architecture diagram for a searchable database security encryption system. The system consists of five core modules: metadata management module, key management module, encryption and decryption module, SQL statement ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com