Method, device and system for capturing network attack behavior, equipment and medium
A network attack and behavioral technology, applied in the network field, can solve the problems that relational databases are not suitable for query and analysis, and achieve the effects of increasing availability, reducing IO consumption, and solving downtime
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
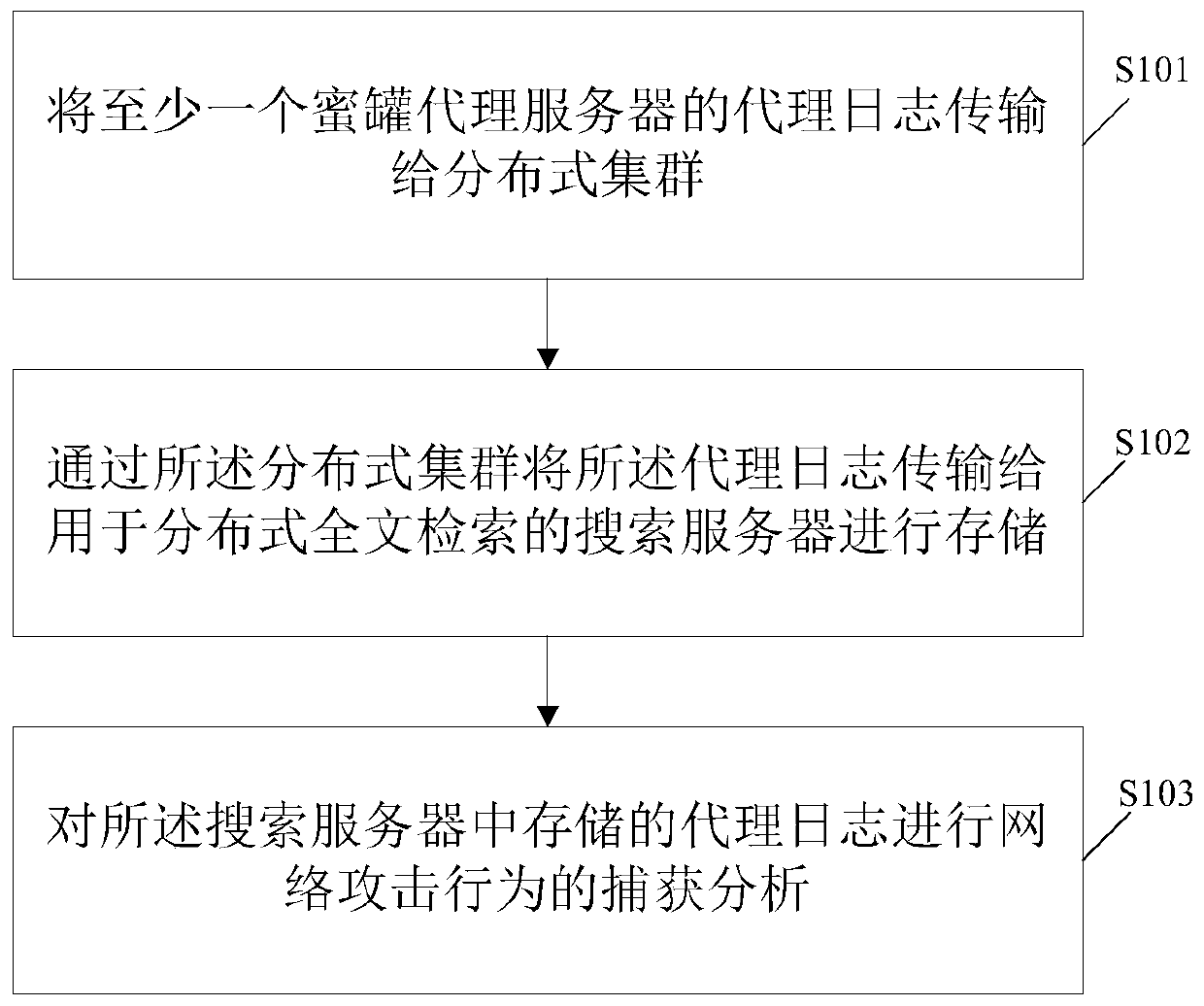
[0049] An embodiment of the present invention provides a method for capturing network attack behavior, such as figure 1 As shown, the method includes:
[0050] S101, transmitting the proxy log of at least one honeypot proxy server to the distributed cluster;
[0051] S102. Transmitting the proxy log to a search server for distributed full-text retrieval through the distributed cluster for storage;
[0052] S103, capturing and analyzing network attack behaviors on the proxy logs stored in the search server.
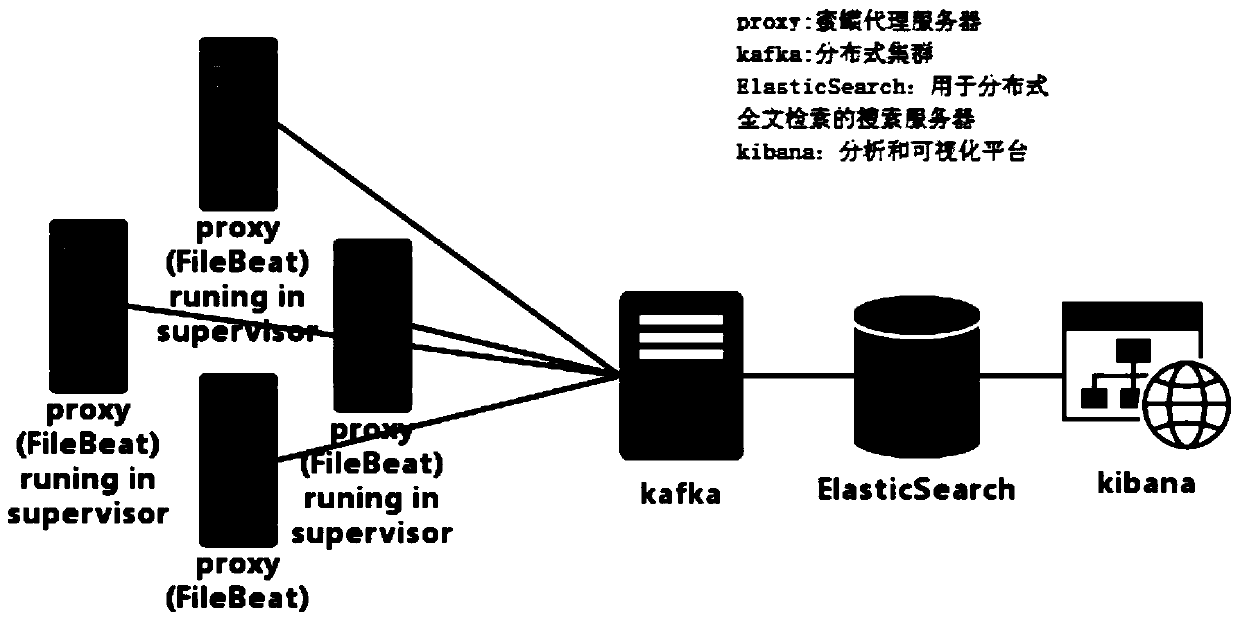
[0053] Among them, the proxy log is used to access the data source of the honeypot proxy server; for example, the IP of the host computer accessing the honeypot proxy server, HTTP request header, response header, POST content, resources and parameters of URL requests, etc. Distributed clusters can be Kafka clusters. Network attack behaviors may include web crawler behaviors and credential stuffing behaviors.
[0054]Web crawler: This is a kind of "friendly" behavior. I...
Embodiment 2
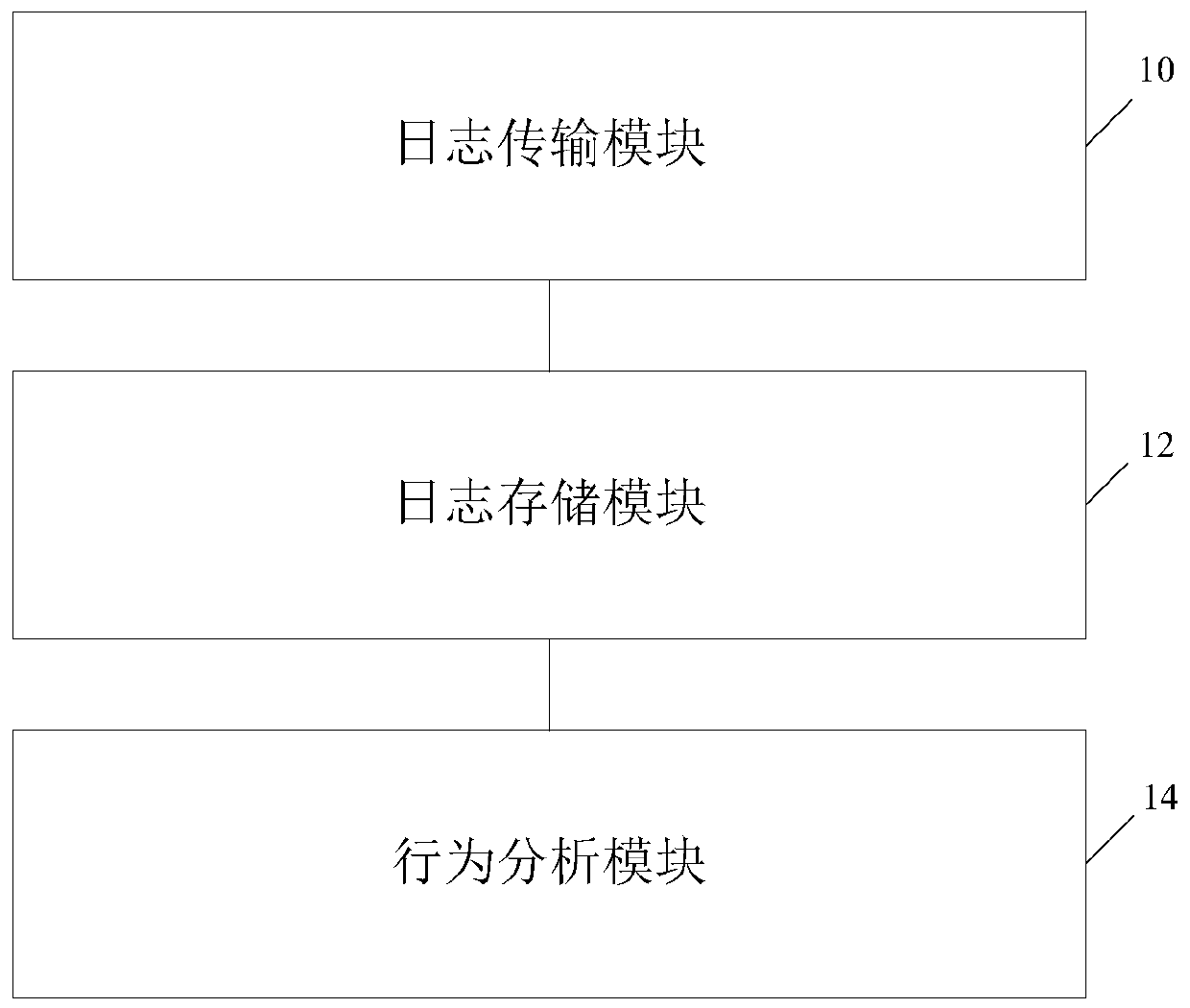
[0083] An embodiment of the present invention provides a device for capturing network attack behavior, such as image 3 As shown, the device is a device embodiment corresponding to Embodiment 1, which includes:
[0084] The log transmission module 10 is used to transmit the proxy log of at least one honeypot proxy server to the distributed cluster;
[0085] A log storage module 12, configured to transmit the proxy log to a search server for distributed full-text retrieval through the distributed cluster for storage;
[0086] The behavior analysis module 14 is configured to capture and analyze network attack behaviors on the proxy logs stored in the search server.
[0087] In some embodiments, the device may also include:
[0088] The proxy management module is used to manage the operation of the honeypot proxy service of each honeypot proxy server through the supervisor of the server proxy service program.
[0089] Wherein, the agent management module is specifically used t...
Embodiment 3
[0099] An embodiment of the present invention provides a proxy honeypot system, which includes at least one honeypot proxy server, a distributed cluster, a search server for distributed full-text search, and the capturing device according to claim 9 .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com