A control method of an information processing device
A technology of an information processing device and a control method, which is applied in the field of information security, can solve problems such as the inability of users to process abnormal data in a targeted manner, and achieve the effect of preventing abnormal deletion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
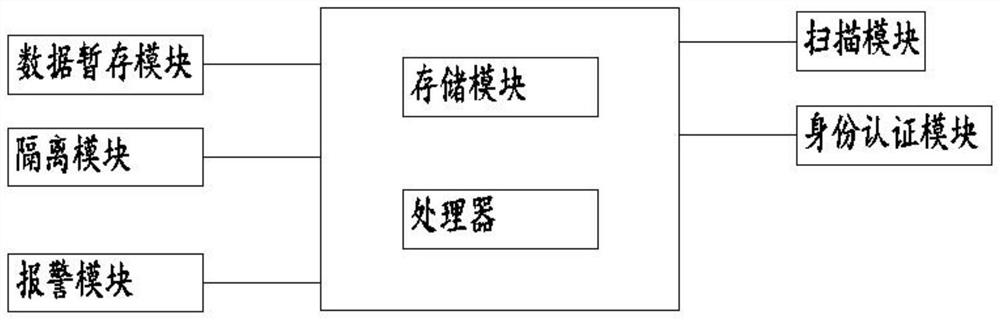
[0028] see figure 1 , in Embodiment 1 of the present invention, an information processing device includes a data temporary storage module for temporarily storing data.
[0029] The scanning module is configured to scan the data in the temporary data storage module, and deliver the scanning result to the processor.
[0030] The processor is used for receiving signals sent by each module, and issuing instructions according to the signals of each module.
[0031] The isolation module is used to save part of the suspicious data in the data temporary storage module, so as to facilitate the analysis of the data in the later stage; the isolation module also includes a firewall, and the firewall is set to facilitate the isolation of the data.
[0032] Setting up the isolation module facilitates the processing of abnormal data in the later stage, prevents abnormal deletion caused by system problems, and facilitates targeted measures for the abnormal data in the later stage.
[0033] ...
Embodiment 2
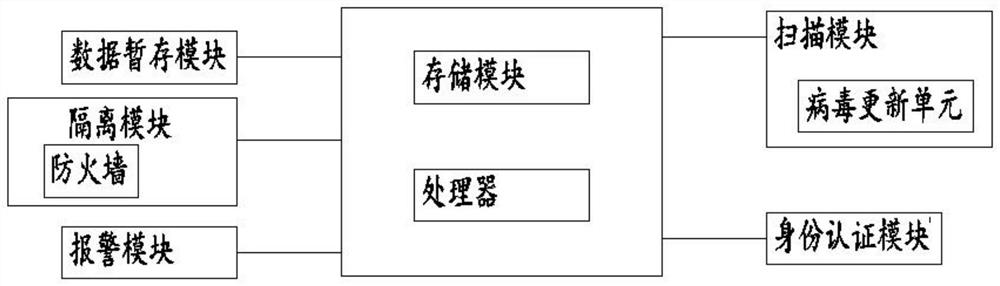
[0040] see figure 2 , in Embodiment 2 of the present invention, an information processing device includes a data temporary storage module for temporarily storing data;
[0041] A scanning module, configured to scan the data in the data temporary storage module, and pass the scanning result to the processor;
[0042] The scanning module also includes a virus update unit, which is convenient for virus update and ensures safe processing of data.
[0043] The processor is used for receiving the signals sent by each module, and issuing instructions according to the signals of each module;
[0044] The isolation module is used to save part of the suspicious data in the data temporary storage module, so as to facilitate the analysis of the data in the later stage; the isolation module also includes a firewall, and the firewall is set to facilitate the isolation of the data.
[0045] Setting up the isolation module facilitates the processing of abnormal data in the later stage, pre...
Embodiment 3
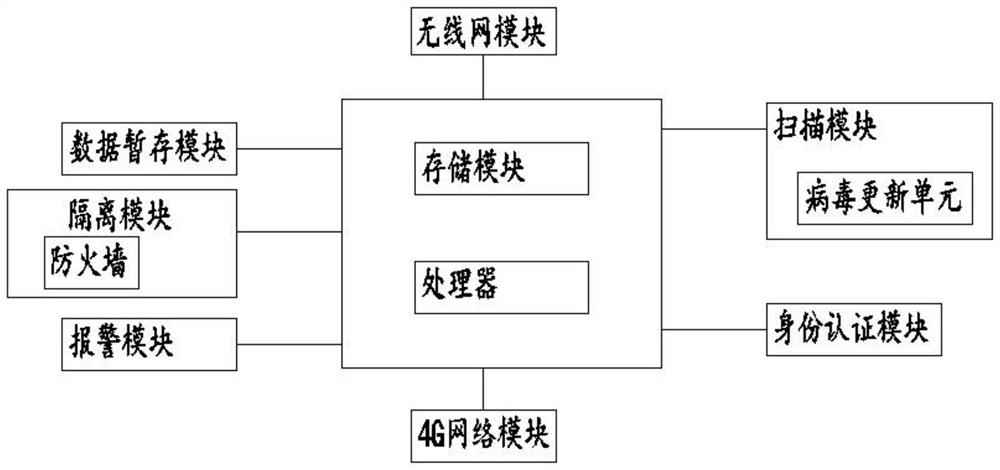
[0053] see image 3 , in Embodiment 3 of the present invention, an information processing device includes a data temporary storage module for temporarily storing data;
[0054] A scanning module, configured to scan the data in the data temporary storage module, and pass the scanning result to the processor;
[0055] The scanning module also includes a virus update unit, which is convenient for virus update and ensures safe processing of data.
[0056] The processor is used for receiving the signals sent by each module, and issuing instructions according to the signals of each module;
[0057] The isolation module is used to save part of the suspicious data in the data temporary storage module, so as to facilitate the analysis of the data in the later stage; the isolation module also includes a firewall, and the firewall is set to facilitate the isolation of the data.
[0058] Setting up the isolation module facilitates the processing of abnormal data in the later stage, prev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com