Power terminal and information security protection method and system of embedded system thereof
An embedded system and information security technology, applied in computer security devices, electronic digital data processing, platform integrity maintenance, etc., can solve problems such as lagging protection technology, affecting real-time performance of control services, and security function constraints, so as to improve information security. The effect of security capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] It should be noted that, in the case of no conflict, the embodiments of the present invention and the features in the embodiments can be combined with each other. The present invention will be described in detail below with reference to the accompanying drawings and examples.
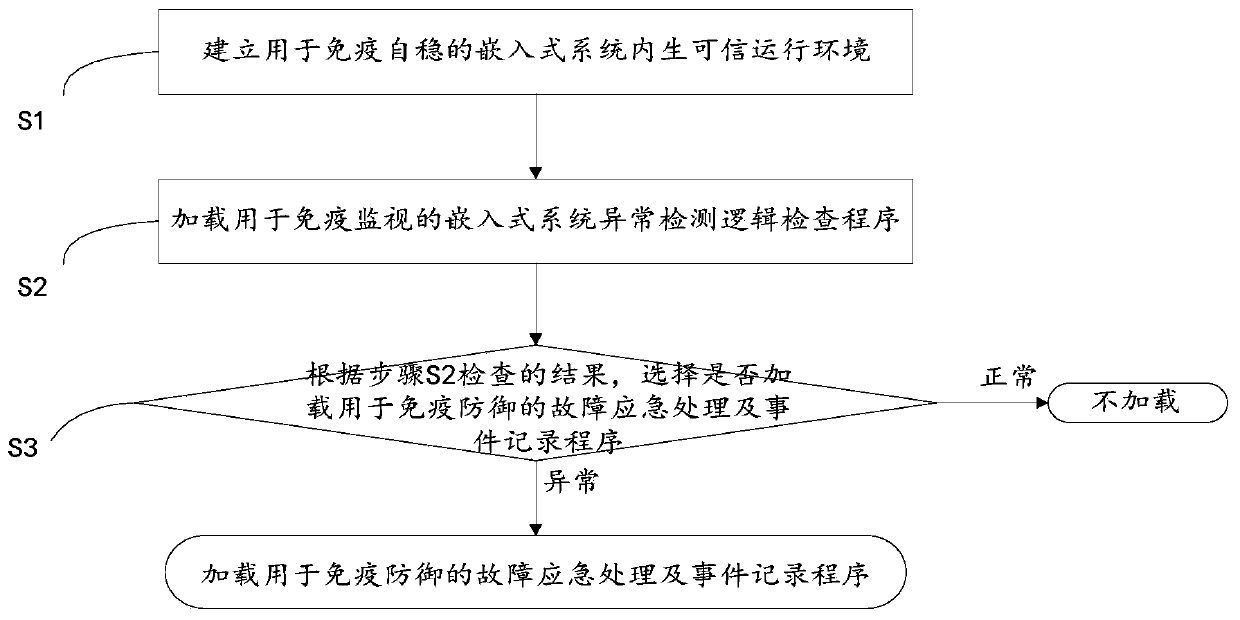
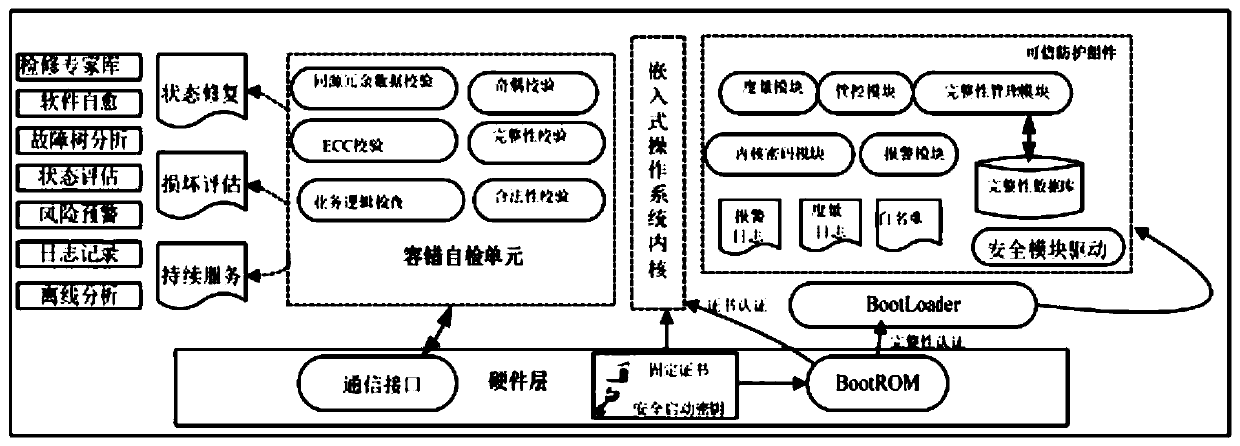
[0061] like figure 1 As shown, an information security protection method for an embedded system of a power terminal, which actively performs information security protection through immune self-stabilization, immune monitoring, and immune defense methods based on the principle of artificial immunity, includes the following steps:
[0062] S1, establish an embedded system endogenous trusted operating environment for immune self-stabilization;
[0063] S2, loading an embedded system anomaly detection logic check program for immune monitoring;
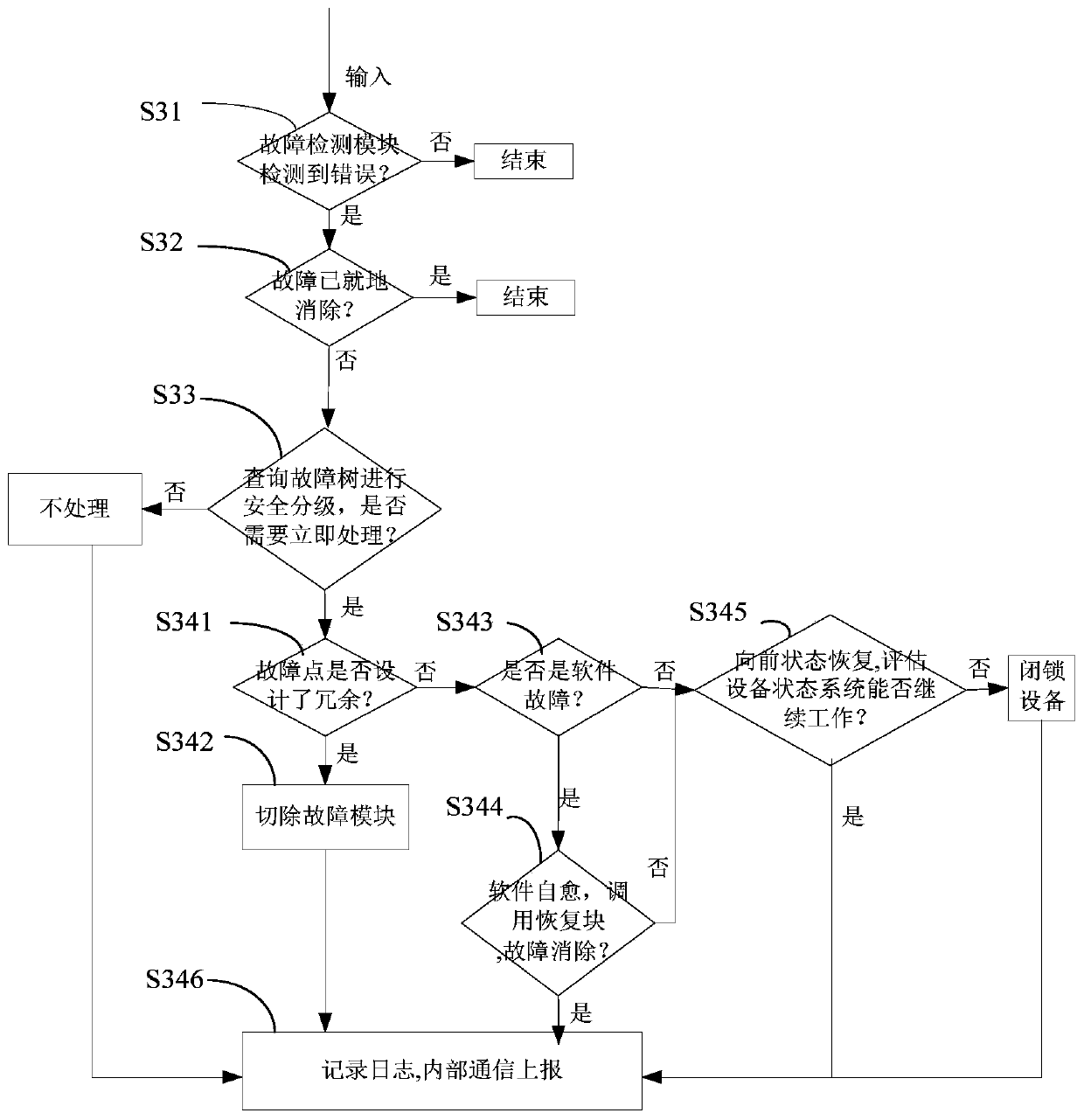
[0064] S3, according to the result of the check in step S2, choose whether to load the fault emergency handling and event recording program for immune defe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com