JPEG asymmetric digital image steganography method
A digital image, asymmetric technology, applied in the field of JPEG asymmetric digital image steganography, can solve problems affecting the security performance of the algorithm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
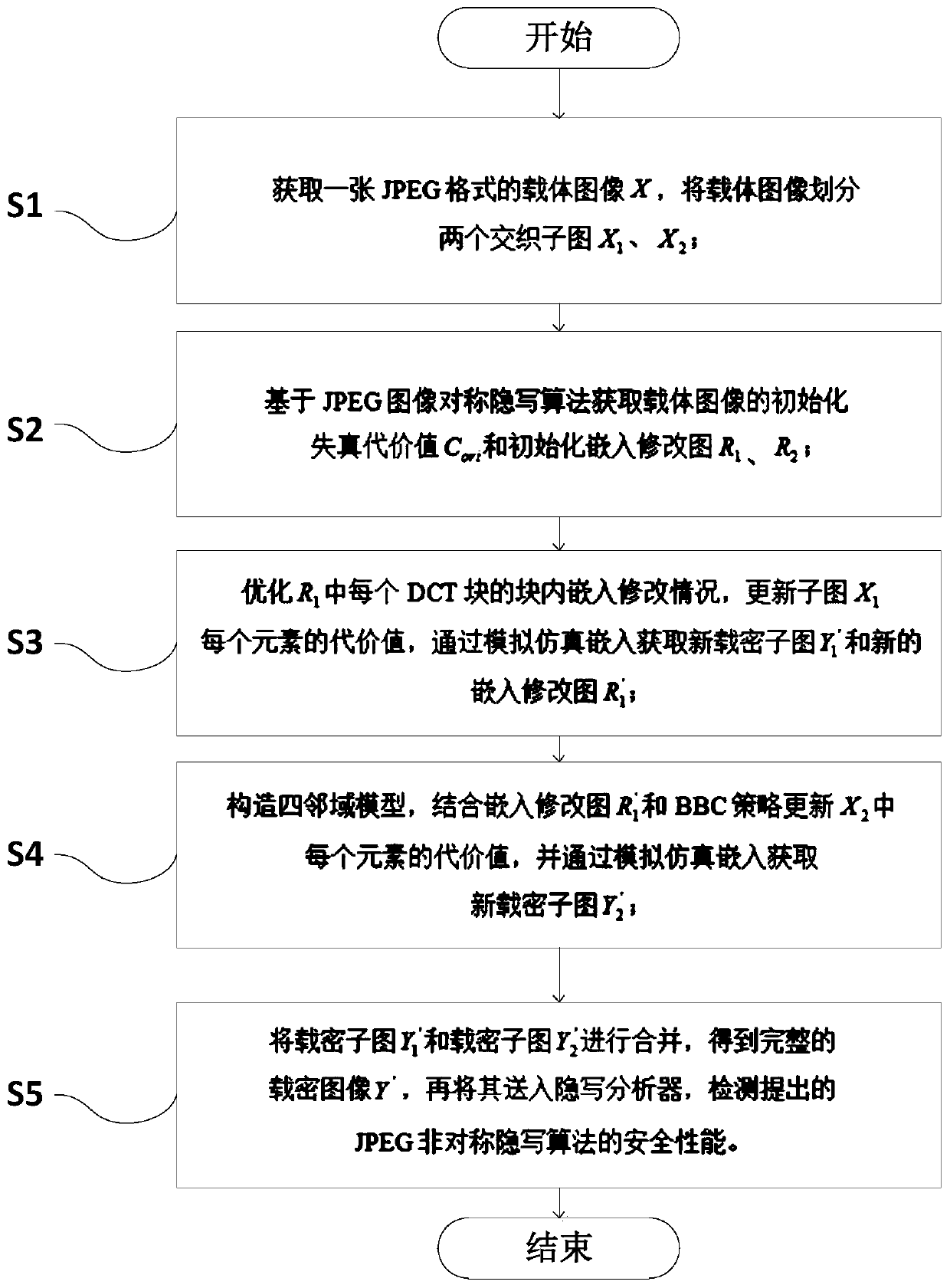
[0081] Such as figure 1 Shown, a kind of JPEG asymmetric digital image steganography method, comprises the following steps:
[0082] S1: Using BOSSbase ver1.01, a representative database of digital image steganography, as the data source, JPEG compression is performed on it with quality factors 75 and 95 respectively to obtain the carrier image X, and the carrier image is divided into two interleaved sub-images X 1 、X 2 ;
[0083] S2: Obtain the initial distortion cost value C of the carrier image based on the JPEG image symmetric steganography algorithm ori and initialize the embedding modification graph in R 1 , R 2 ;
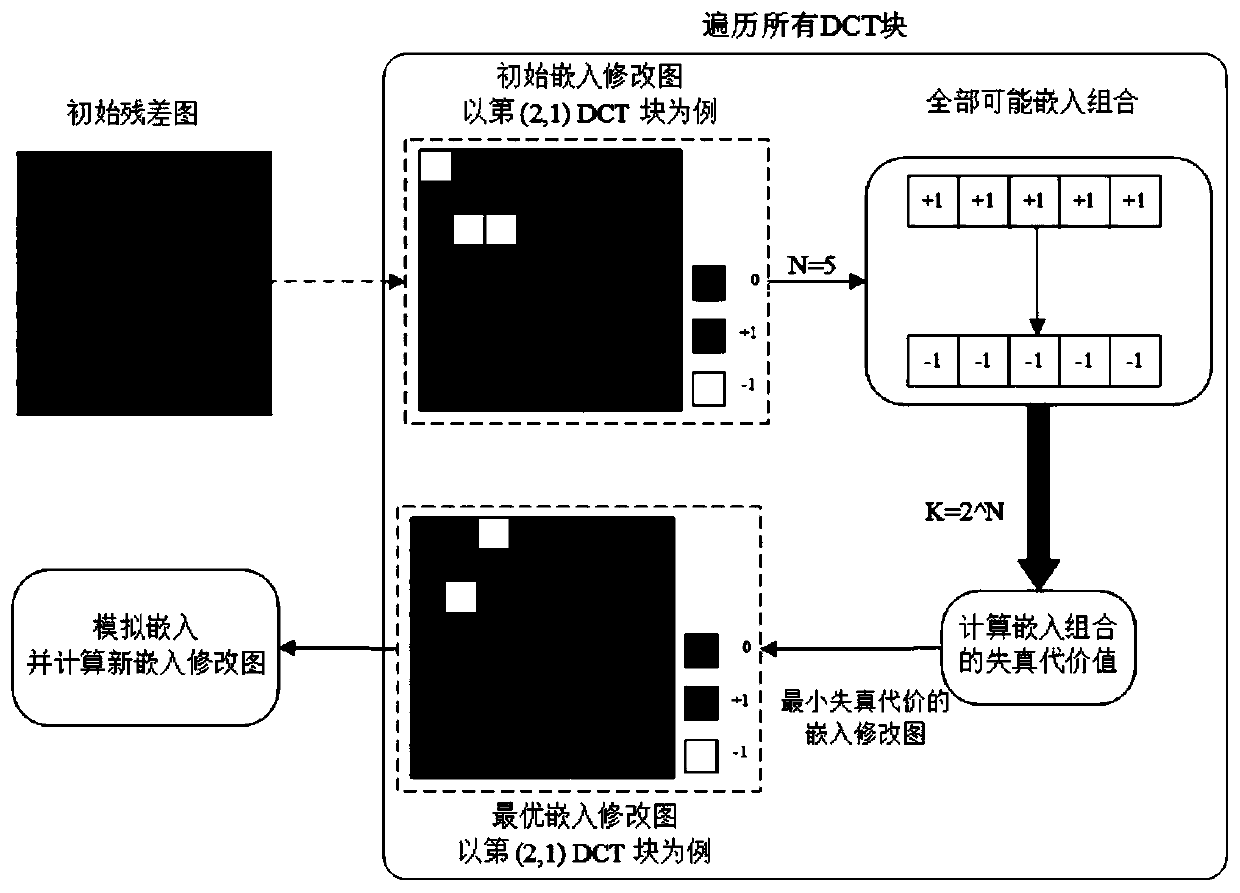
[0084] S3: Optimizing R 1 The embedded modification of each DCT block in the block, update the subgraph X 1 The cost value of each element, through simulation embedding to obtain a new charge carrier graph Y′ 1 and the new embedding modification graph R′ 1 ;
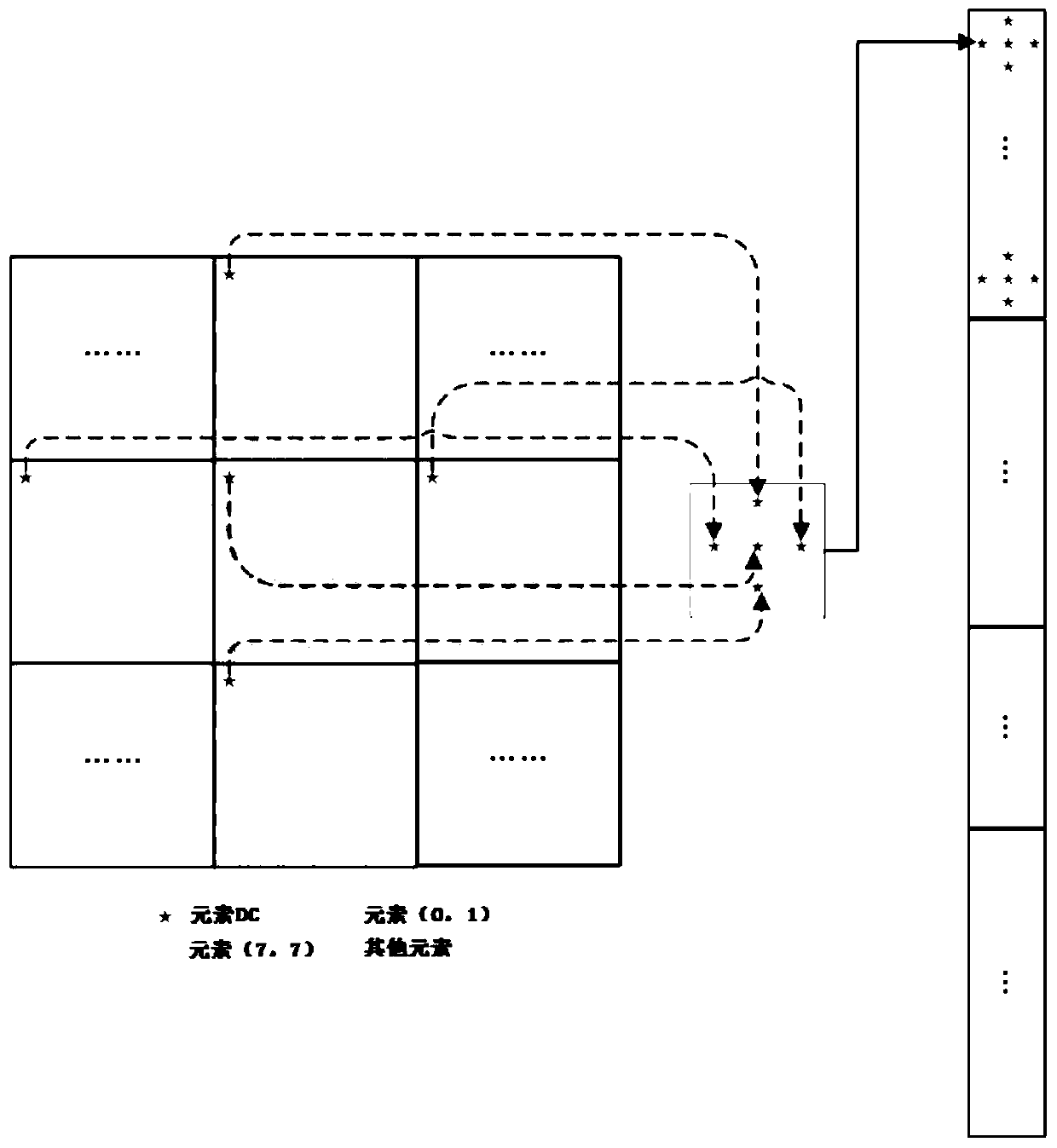
[0085] S4: Construct a four-neighborhood model, and modify the graph R′ in combination wit...
Embodiment 2
[0150] On the basis of Embodiment 1, further, in order to compare the security performance of the JPEG asymmetric digital image steganography method mentioned in the present invention, this embodiment conducts a performance test.
[0151] More specifically, all performance tests in the present invention are based on Bossbase ver1.01, an image library commonly used in digital image steganography, with 10,000 grayscale images with a size of 512×512. First, to construct the cover images, the above images are compressed into JPEG images with quality factors 75 and 95, respectively. Next, choose the three safest JPEG digital image steganography algorithms, respectively J-UNIWARD, GUED, and BET, to initialize the cost value. Then, select the three steganalysis algorithms GFR with the highest performance for JPEG steganalysis detection [9] ,CC-JRM [10] and SCA-GFR [11] . Classification error rate P E As an index to measure the performance of the algorithm, the classification err...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com