Malicious domain name detection method based on tag and attribute similarity of DOM tree
A DOM tree and domain name detection technology, applied in the field of malicious domain name detection of label and attribute similarity, can solve problems such as poor accuracy and low detection rate, and achieve the effects of high accuracy, improved accuracy, and high judgment efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the examples.
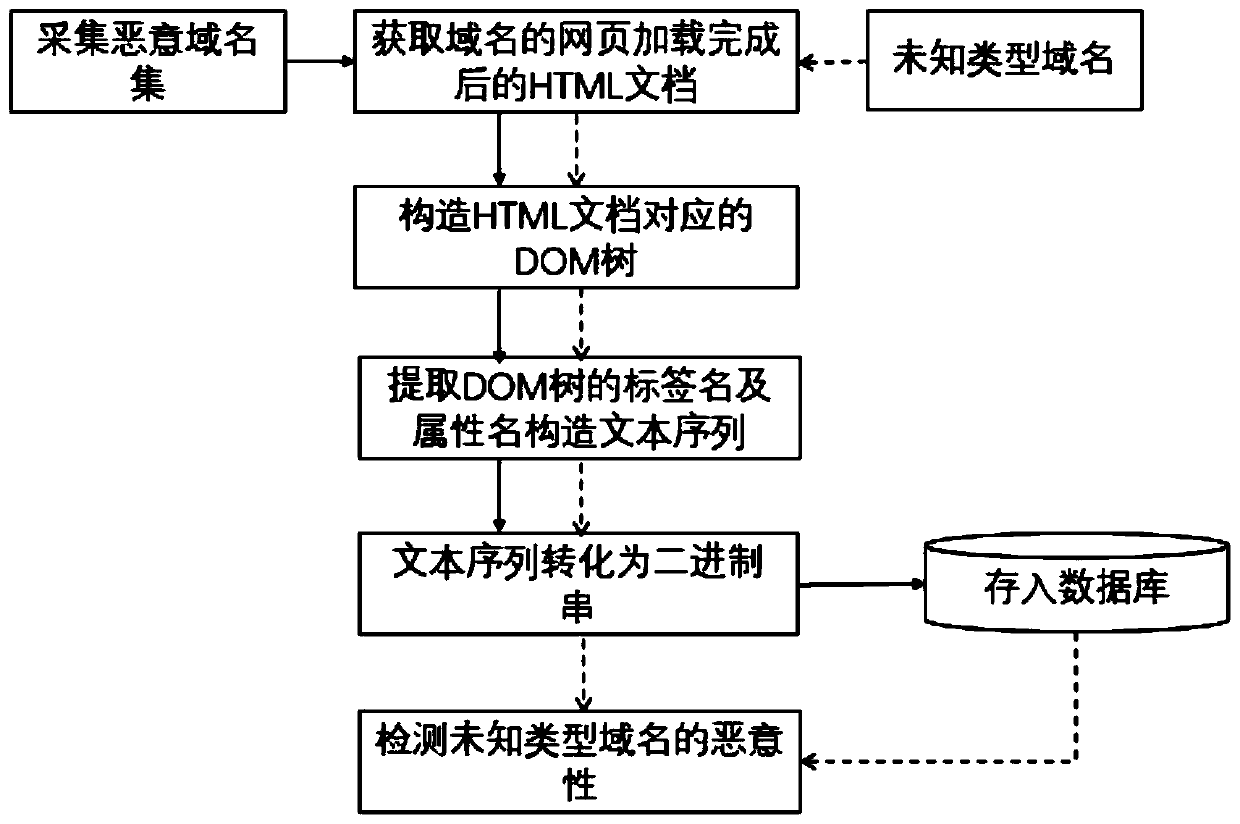
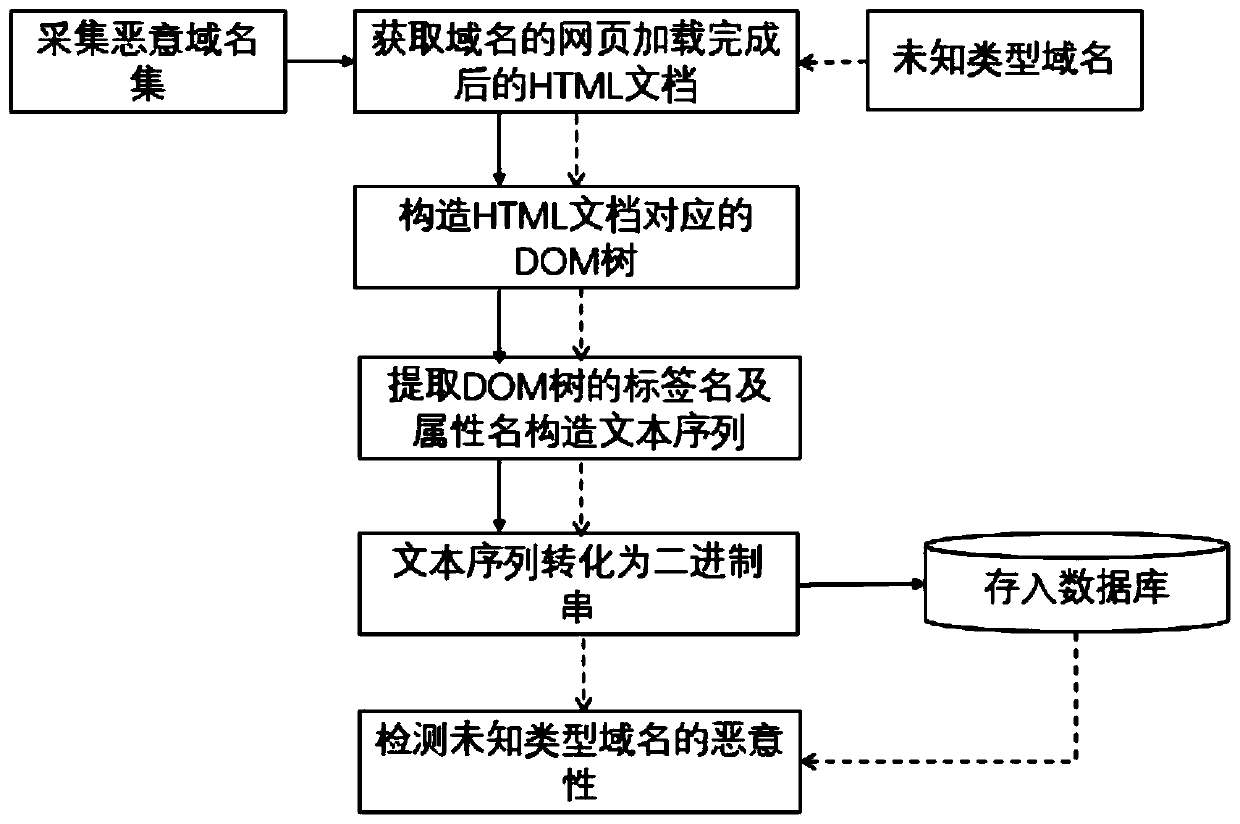
[0031] figure 1 It shows the flow chart of the malicious domain name detection method based on the label and attribute similarity of the DOM tree. The process formed by the solid line in the figure is the processing process of the domain name set of known type, and the process formed by the dotted line in the figure is the malicious domain name of the unknown type. sex testing process.
[0032] By analyzing the DOM tree, it is found that the shallow nodes of the tree have a great influence on the structure of the web page: if the web pages are not similar, the shallow node information will be very different; if the web pages are similar, the shallow label information is close, but the deeper the level, the greater the difference . In order to measure the similarity of the webpage structure from the DOM tree structure of the malicious domain name, a detection method of malicious d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com