DNS hijacking detection method based on Internet of Things equipment
A technology of Internet of Things equipment and detection methods, which is applied in the field of information security, can solve problems such as false positives and false positives, and achieve the effect of increasing accuracy and reducing false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
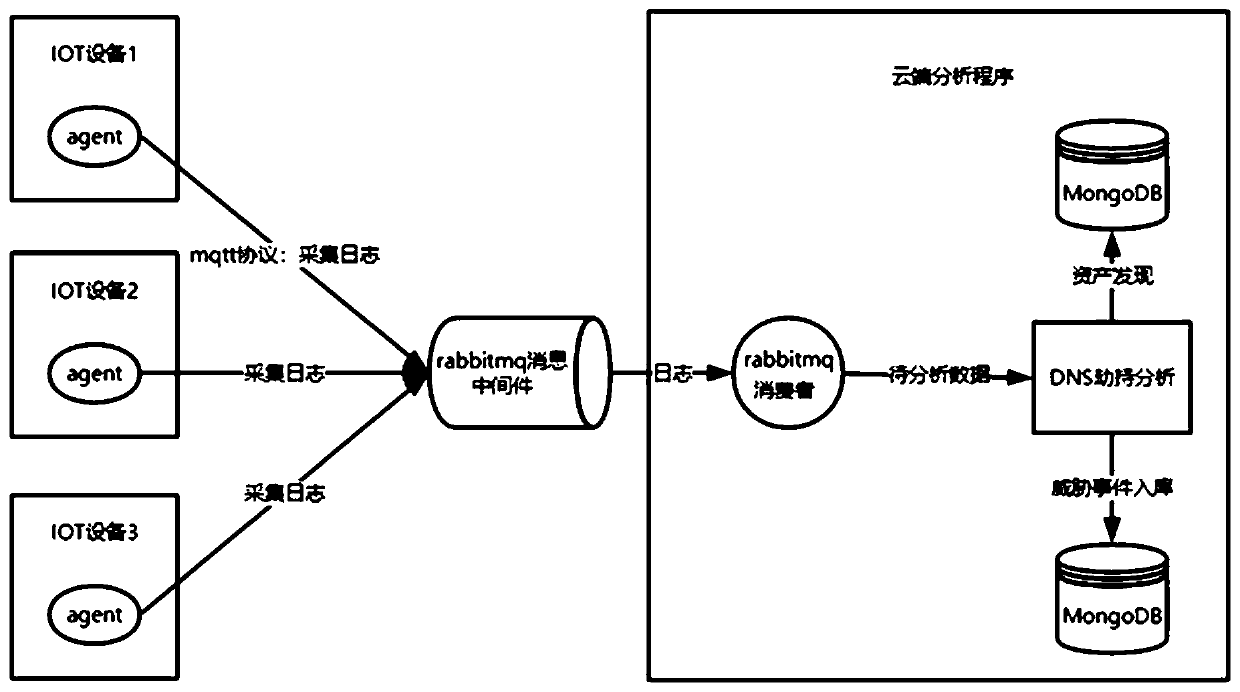
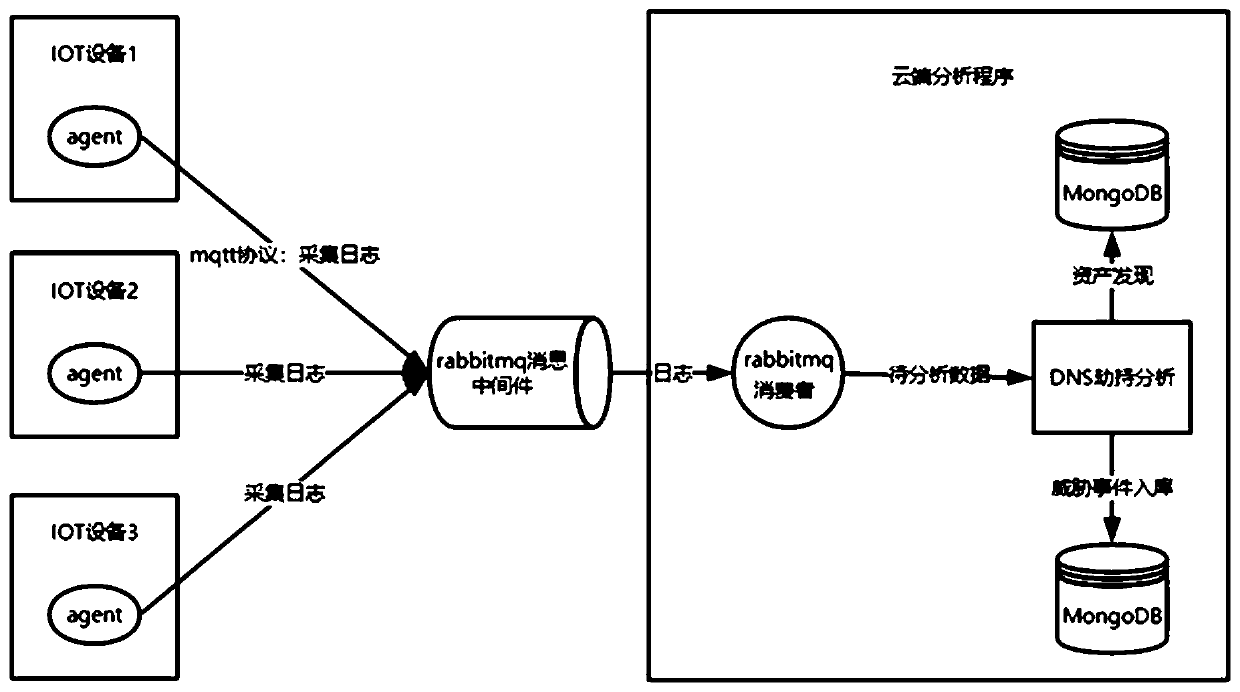
[0029] combined with figure 1 As shown, a DNS hijacking detection method based on IoT devices, including:
[0030] Step S100: Install the agent program on the Internet of Things device, that is, the IOT device. The Agent program adopts the Service form and performs data collection as a background service of the Internet of Things device, and regularly sends messages to the message queue of the rabbitmq message middleware through the mqtt protocol. The data includes device fingerprint information and terminal DNS resolution information, the device fingerprint information is used to uniquely identify the terminal asset device during asset discovery; the terminal DNS resolution information is used to analyze whether DNS hijacking occurs.
[0031] Step S200: The cloud server consumes the rabbitmq message middleware message, analyzes and calculates the detection result, and judges whether DNS hijacking occurs, and saves the original log, and stores the device information of the fir...
Embodiment 2
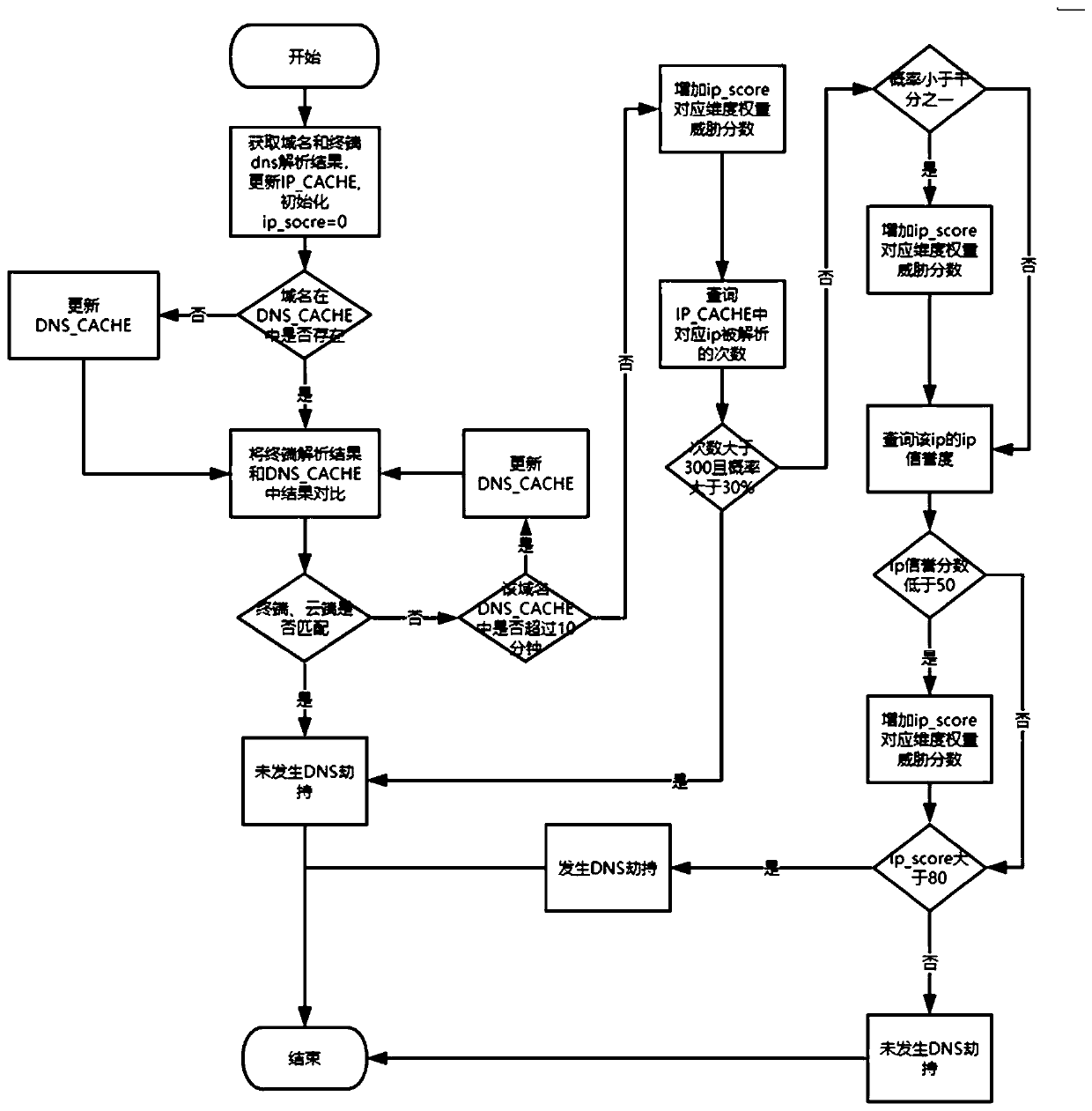
[0039] On the basis of Example 1, in conjunction with the attached figure 1 and figure 2 As shown, the step S200 includes:
[0040] Step S210: After the cloud server obtains the data collected by the agent from rabbitmq, it finds the asset and judges the source of the log according to the fingerprint information of the device;
[0041] Step S220: storing the device fingerprint information into the MongoDB of the cloud server as a device asset set;
[0042] Step S230: Perform DNS hijacking analysis, specifically including:
[0043] Step A: 1) The cloud analysis program parses the log to be analyzed, obtains the domain name and the terminal DNS resolution result, traverses the DNS resolution set, and obtains the domain name to be analyzed. Traverse the domain name result list to be analyzed, obtain the ip to be analyzed, and update the IP_CACHE. The IP_CACHE is used to cache the historical times when the terminal domain name is resolved to the corresponding IP; as the basis ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com