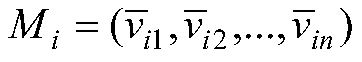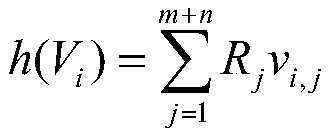Method for elliptic curve signature in single-source network coding environment
A network coding and elliptic curve technology, applied in the field of network information security, can solve the problems of intra-generation pollution and inter-generation pollution, unstable network communication transmission, and system pollution without using elliptic curve signatures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
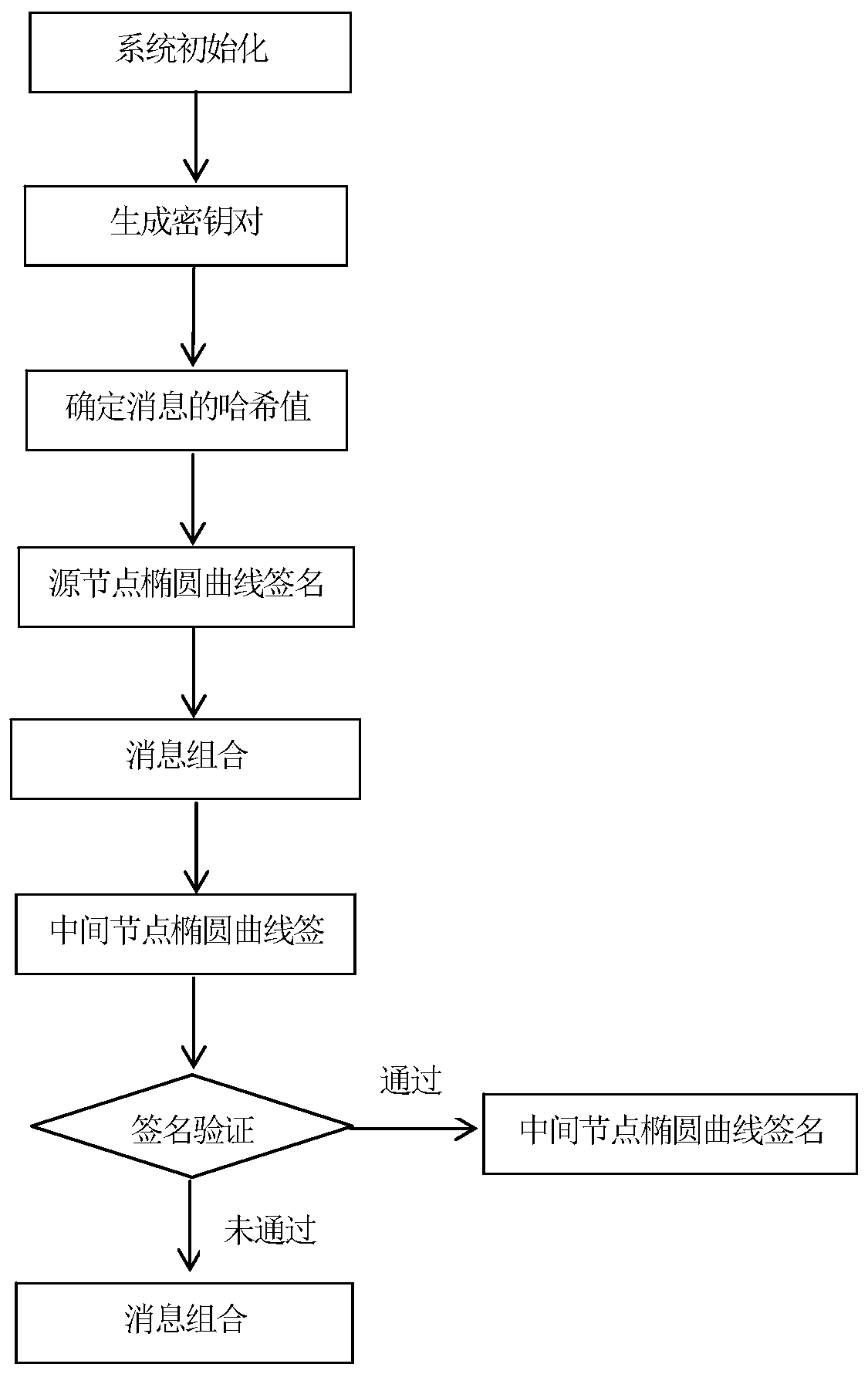
[0085] In this embodiment, the elliptic curve y 2 ≡x 3 +ax+b mod q, the large prime number q is 1229388206666334394638158784063623508484129267643 as an example, the method of elliptic curve homomorphic signature of single-source network coding consists of the following steps (such as figure 1 shown):
[0086] A. System initialization
[0087] (A1) The trusted party defines a finite field F q Elliptic curve E on:
[0088] the y 2 ≡x 3 +ax+b
[0089] where a,b∈F q , q is a large prime number among finite positive integers, q is 1229388206666334394638158784063623508484129267643, satisfying 4a 3 +27b 2 ≠0 constant.
[0090] (A2) The trusted party sends the identifier I of the designated generation in the single-source network coding to the source node of the single-source network coding through a secure channel:
[0091] I={I 1 ,I 2 ,...,I n}
[0092] where n is a finite positive integer.
[0093] (A3) The trusted party selects a cryptographically secure Hash funct...
Embodiment 2
[0162] In this embodiment, the elliptic curve y 2 ≡x 3 +ax+b mod q, the large prime q is 1449849246051449679173689466738734355356891578223 as an example, the method of elliptic curve homomorphic signature of single-source network coding consists of the following steps:
[0163] A. System initialization
[0164] (A1) The trusted party defines a finite field F q Elliptic curve E on:
[0165] the y 2 ≡x 3 +ax+b
[0166] where a,b∈F q , q is a large prime number among finite positive integers, q is 1449849246051449679173689466738734355356891578223, satisfying 4a 3 +27b 2 ≠0 constant.
[0167] (A2) The trusted party sends the identifier I of the designated generation in the single-source network coding to the source node of the single-source network coding through a secure channel:
[0168] I={I 1 ,I 2 ,...,I n}
[0169] where n is a finite positive integer.
[0170] (A3) The trusted party selects a cryptographically secure Hash function H G :
[0171] {0,1} * →G ...
Embodiment 3
[0185] In this embodiment, the elliptic curve y 2 ≡x 3 +ax+bmodq, the large prime q is 1366294046726635493399336680549214898319268492501 as an example, the method of elliptic curve homomorphic signature of single-source network coding consists of the following steps:
[0186] A. System initialization
[0187] (A1) The trusted party defines a finite field F q Elliptic curve E on:
[0188] the y 2 ≡x 3 +ax+b
[0189] where a,b∈F q , q is a large prime number among finite positive integers, q is 1366294046726635493399336680549214898319268492501, satisfying 4a 3 +27b 2 ≠0 constant.
[0190] (A2) The trusted party sends the identifier I of the designated generation in the single-source network coding to the source node of the single-source network coding through a secure channel:
[0191] I={I 1 ,I 2 ,...,I n}
[0192] where n is a finite positive integer.
[0193] (A3) The trusted party selects a cryptographically secure Hash function H G :
[0194] {0,1} * →G 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com