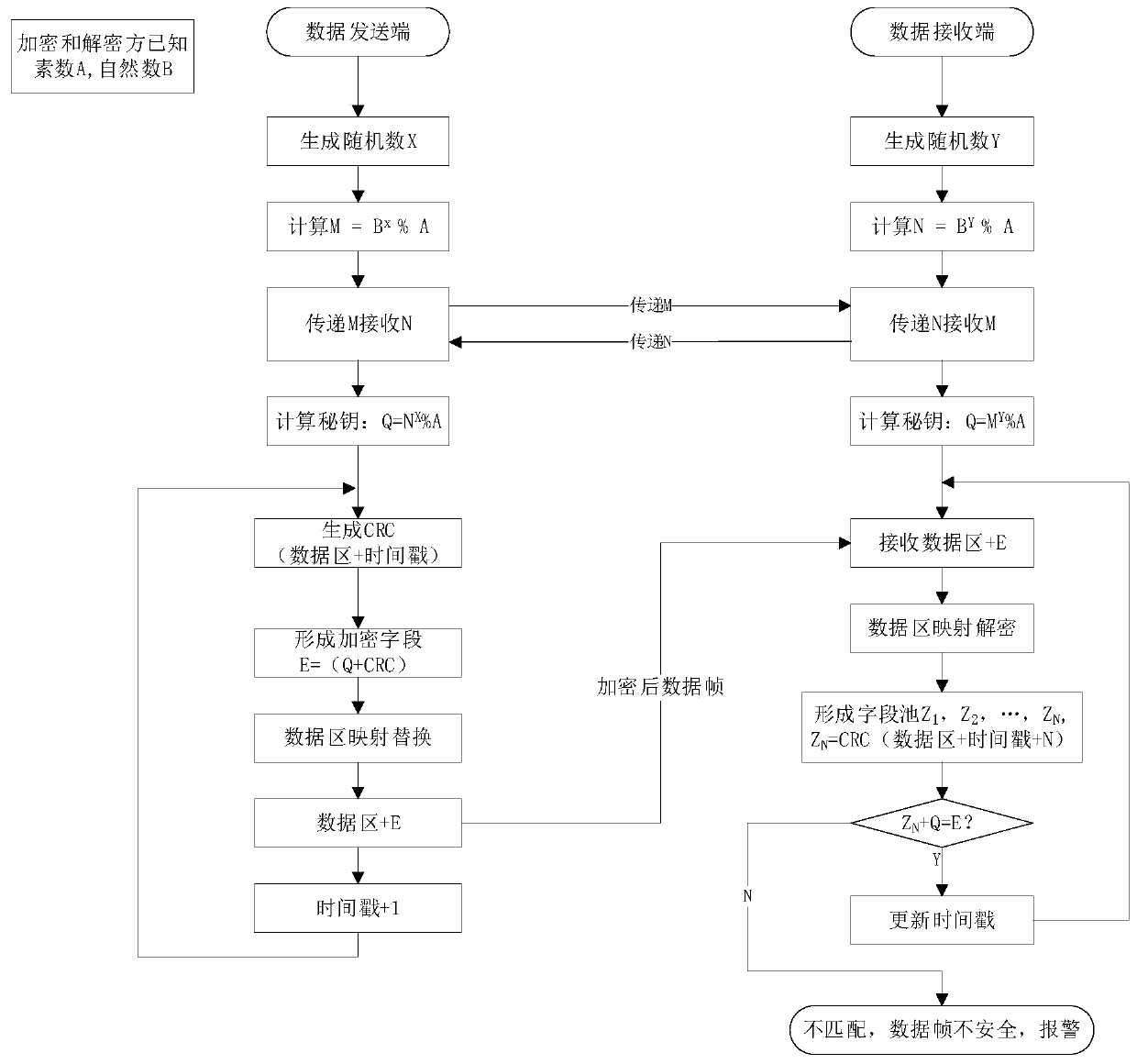
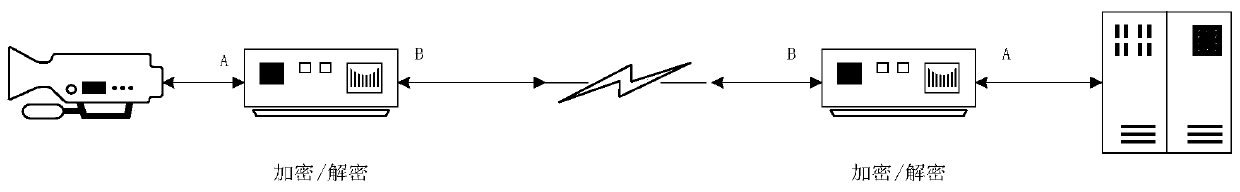
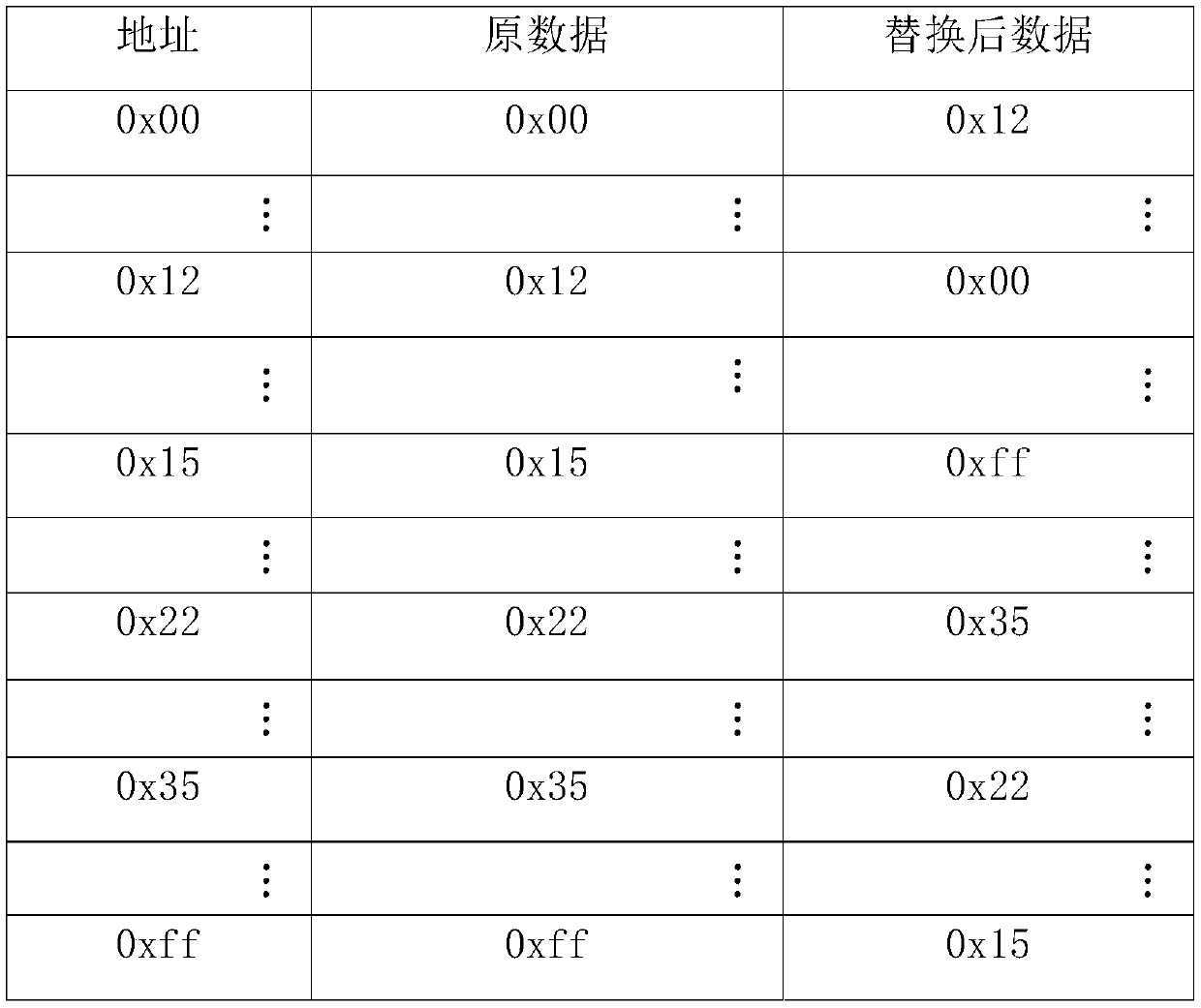
Data block association encryption algorithm based on timestamps
An encryption algorithm and data block technology, applied in the field of data communication, to achieve the effect of simple calculation, guaranteed reliability and integrity, and small insertion delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0069] In the public security video surveillance system, public or private network transmission is used between the video capture front end and the control center. For ease of description, the encryption decryptor near the video sending end is called an encryptor, and the encryption decryptor near the video receiving end is called a decryptor. The network port that the encryptor connects to the video source is called port A, the port that connects to the public network is called port B, the port that the decryptor connects to the public network is called port B, and the port that connects to the local area network is called port A.
[0070] The data collected by the video capture front end is transmitted to the server in the form of UDP packets. The UDP packet format is shown in Table 1. In this application example, the encryption / decryption device uses the algorithm of the present invention to encrypt and decrypt. In order not to affect the normal transmission of data packets on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com