Security test method and device for Web API, electronic equipment and storage medium
A technology of security testing and storage paths, applied in the Internet field, can solve problems such as difficult to ensure no omissions, huge costs, and high risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
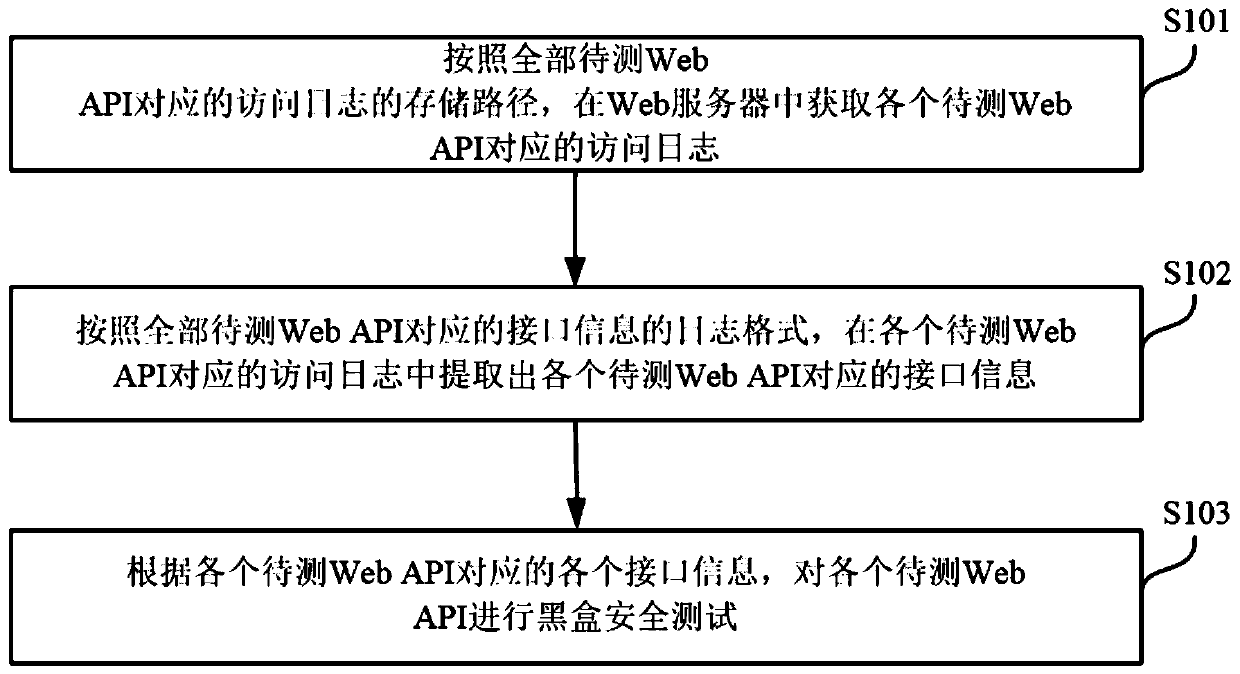
[0047] figure 1 This is a schematic flow chart of the Web API security testing method provided by the first embodiment of the present invention. The method can be executed by a Web API security testing device or electronic equipment, which can be implemented by software and / or hardware. The device or electronic device can be integrated in any smart device with network communication function. Such as figure 1 As shown, the security testing method of Web API can include the following steps:
[0048] S101. Obtain the access log corresponding to each Web API to be tested from the Web server according to the storage path of the access log corresponding to all Web APIs to be tested.
[0049] In a specific embodiment of the present invention, the electronic device may obtain the access log corresponding to each Web API to be tested from the Web server according to the storage path of the access log corresponding to all Web APIs to be tested. Preferably, the access log corresponding to ea...
Embodiment 2
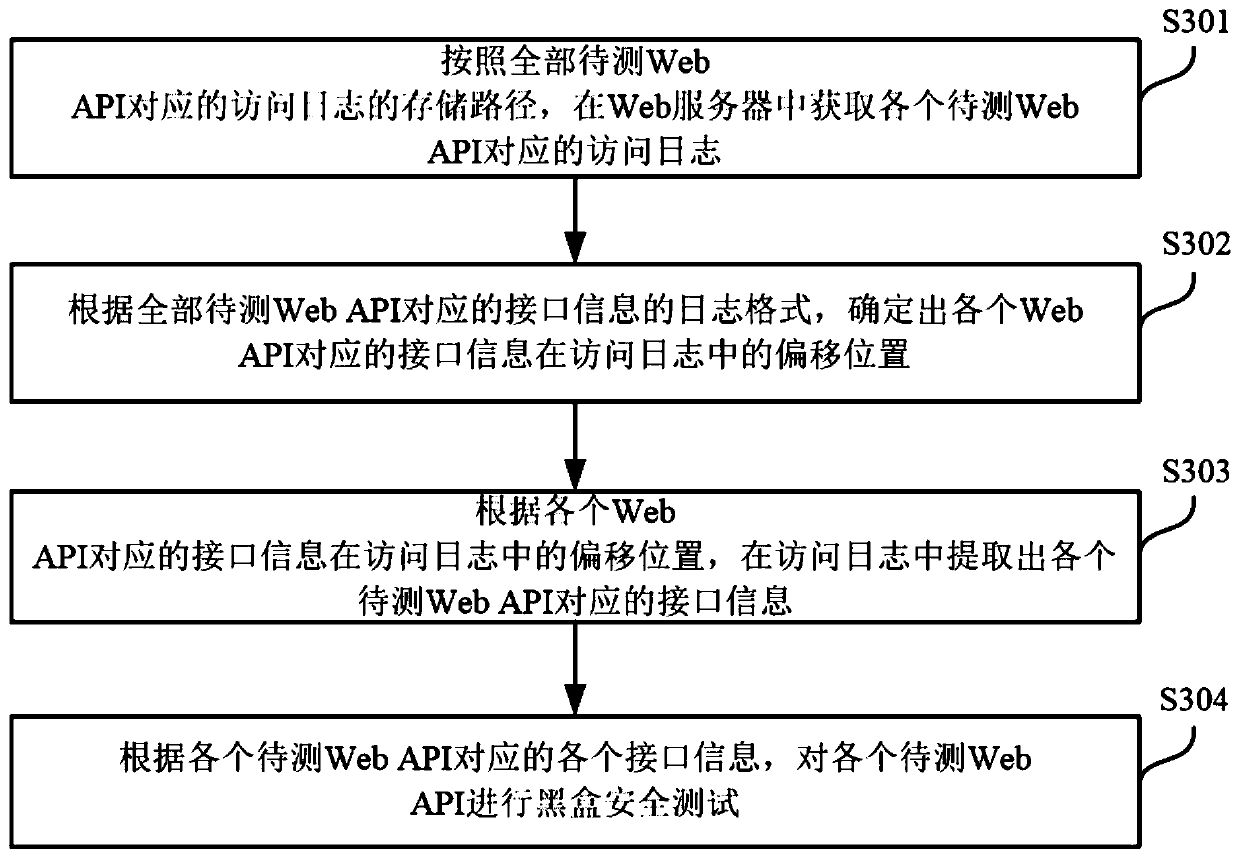
[0059] image 3 It is a schematic flow diagram of a Web API security testing method provided in the second embodiment of the present invention. Such as image 3 As shown, the security testing method of Web API can include the following steps:
[0060] S301. Obtain the access log corresponding to each Web API to be tested from the Web server according to the storage path of the access log corresponding to all Web APIs to be tested.
[0061] In a specific embodiment of the present invention, the electronic device may obtain the access log corresponding to each Web API to be tested from the Web server according to the storage path of the access log corresponding to all Web APIs to be tested. Preferably, the access log corresponding to each WebAPI to be tested may be an access_log log or other types of access logs, which is not limited here.
[0062] S302: Determine the offset position of the interface information corresponding to each Web API in the access log according to the log form...
Embodiment 3
[0071] Figure 4 It is a schematic flow diagram of a Web API security testing method provided in the third embodiment of the present invention. Such as Figure 4 As shown, the security testing method of Web API can include the following steps:
[0072] S401. Obtain the access log corresponding to each Web API to be tested from the Web server according to the storage path of the access log corresponding to all Web APIs to be tested.
[0073] In a specific embodiment of the present invention, the electronic device may obtain the access log corresponding to each Web API to be tested from the Web server according to the storage path of the access log corresponding to all Web APIs to be tested. Preferably, the access log corresponding to each WebAPI to be tested may be an access_log log or other types of access logs, which is not limited here.
[0074] S402: Determine the offset position of the interface information corresponding to each Web API in the access log according to the log for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com