A double-agent cross-domain authentication system based on identification password and alliance chain
A technology for identifying passwords and authentication systems, applied in the field of dual-agent cross-domain authentication systems, can solve problems such as application restrictions, and achieve the effects of alleviating workload, alleviating computing overhead, and alleviating throughput bottlenecks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
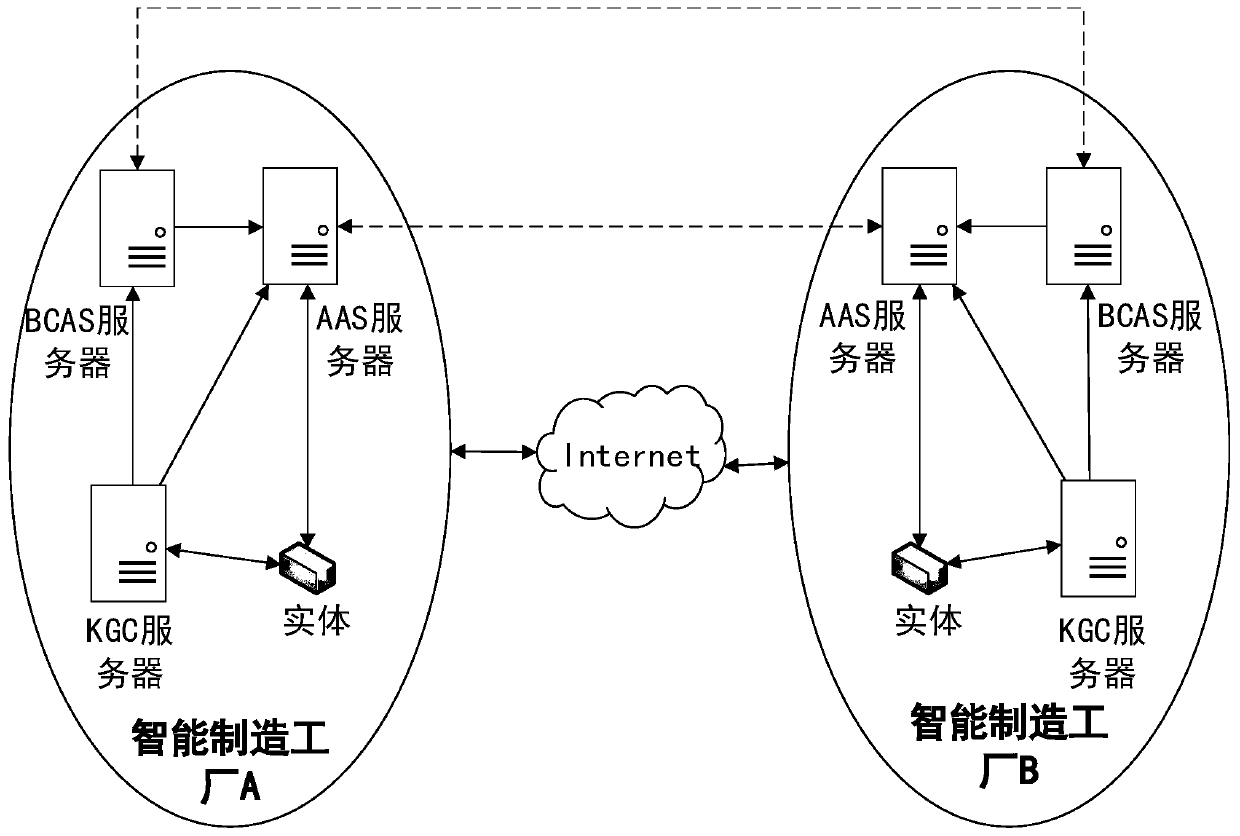
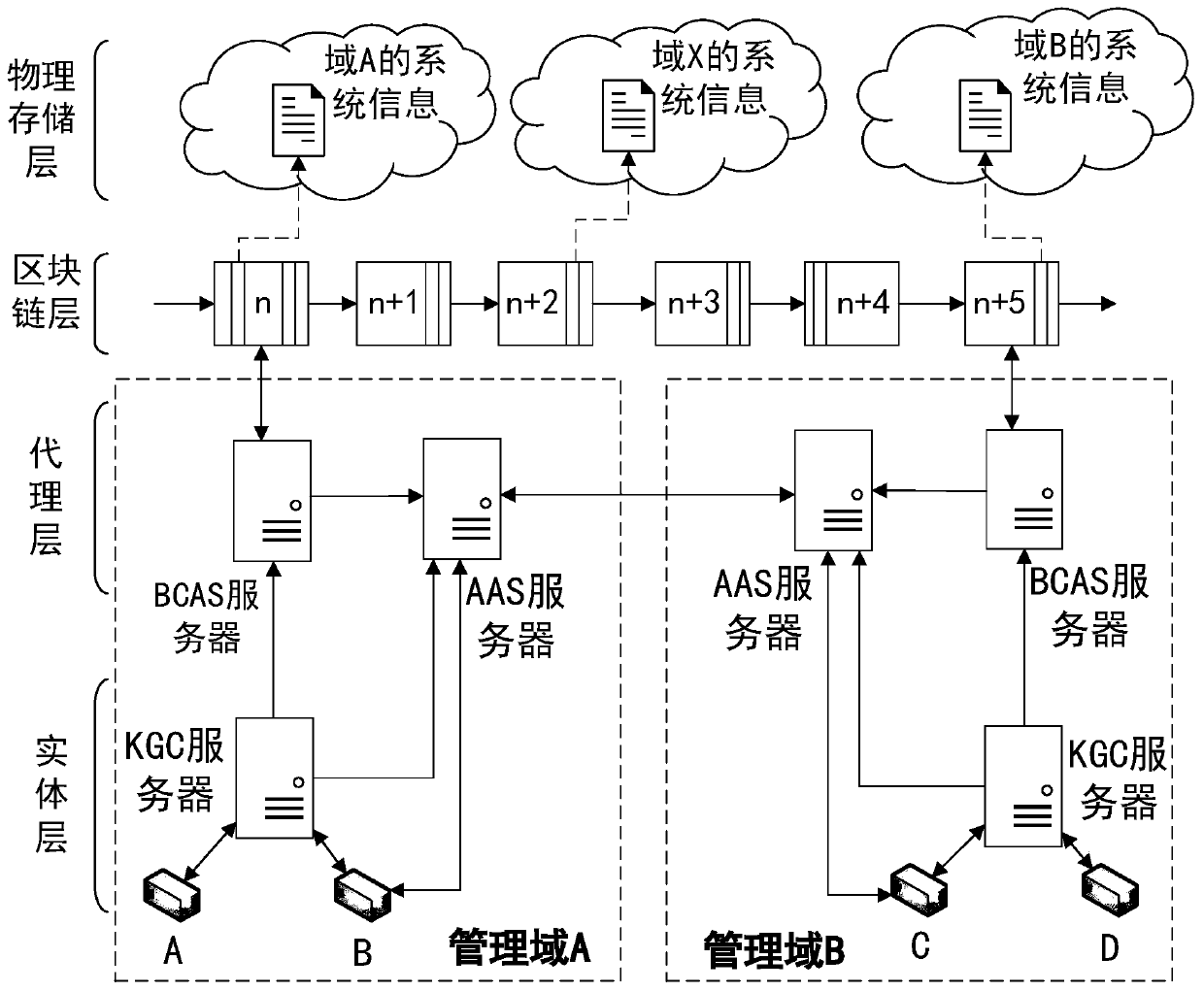
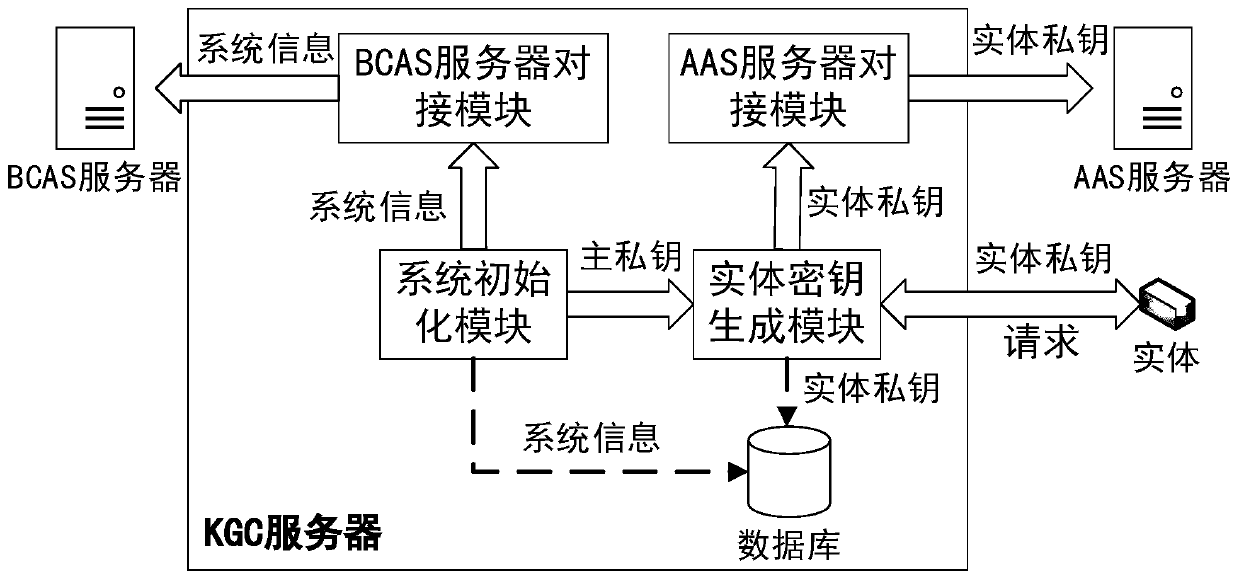
[0064] This embodiment describes the implementation topology, architecture, components contained in the architecture and their functions of the dual-agent authentication system based on identification passwords and consortium chains.
[0065] The dual-agent authentication system based on identification password and alliance chain can be deployed in cross-domain application scenarios of the Internet of Things. This embodiment takes an application scenario of a smart manufacturing factory as an example. To simplify the description, two smart manufacturing factories are taken as examples. There are two smart manufacturing factories: smart manufacturing factory A and smart manufacturing factory B, their management is independent of each other, but they have a business cooperation relationship. Several smart manufacturing devices are deployed in each smart manufacturing factory, which have the capabilities of perception, storage, processing and execution, which is equivalent to an ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com