Android malicious application detection method based on improved gray wolf algorithm
A malicious application and detection method technology, applied in computing, computing models, computer components and other directions, can solve the problems of high feature dimension, misclassification of malicious samples, huge workload of machine learning classifiers, etc. The effect of search ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
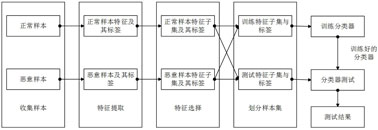
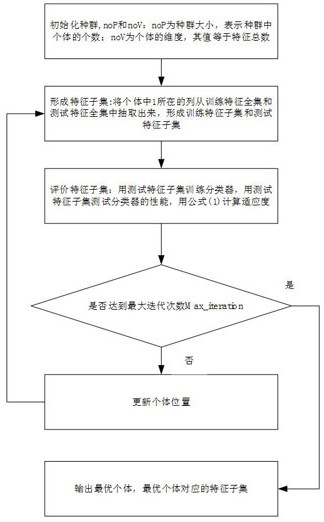
[0046] The Android malicious application detection method based on the improved gray wolf algorithm includes the following steps:
[0047] Step 1: Collect sample sets, namely Android applications (APK for short), including benign APKs and malicious APKs;
[0048]Step 2: Decompile the APK, extract its API call information and permission application information as features, and vectorize it into a feature set to form a sample feature set; specifically:
[0049] 2a) use the decompilation tool apktool to decompile the collected APK, obtain the *.smali file, scan the "invoke-virtual" statement in each smali file in turn, and obtain the API call information of the APK;
[0050] 2b) Use the tool in the Android SDK - appt to extract the permission applied by the APK, and obtain the permission information of the APK;
[0051] 2c) Take the complete set of API call information and permission information of all APKs as the feature set; each row represents an APK file, each column represe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com