Host device vulnerability scanning method and system
A host device and vulnerability scanning technology, applied in the field of information security, can solve the problems of increasing the load risk of the host device and affecting the performance of the host, and achieve the effects of avoiding repeated collection, reducing load and risk, and small occupancy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
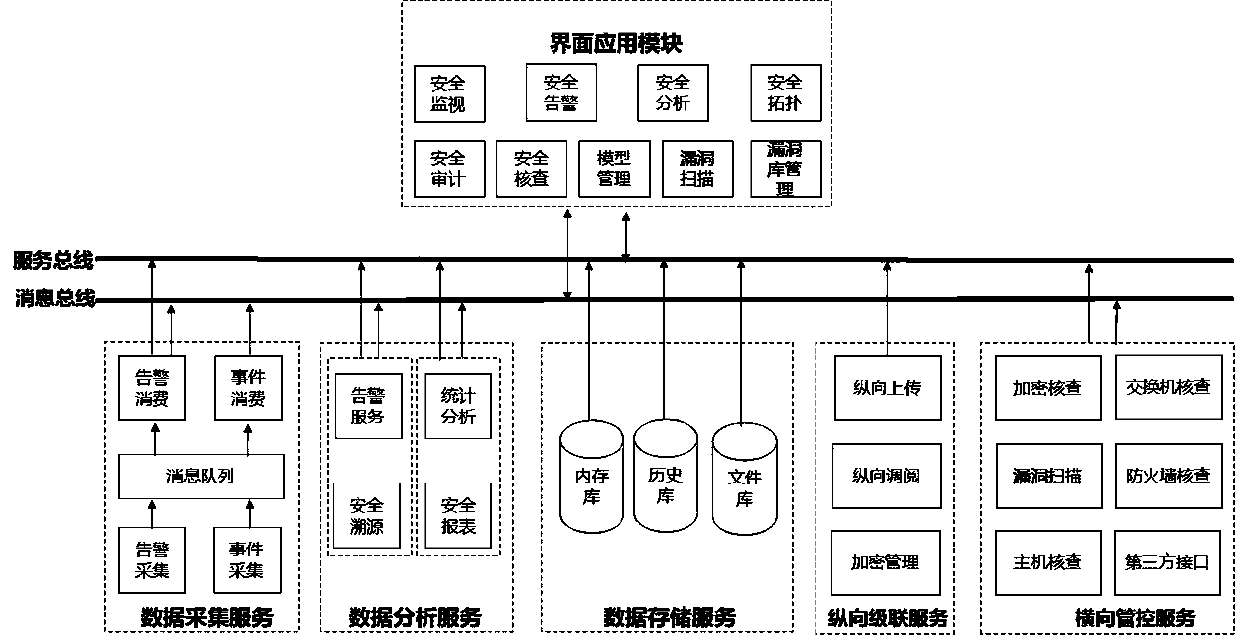
Image
Examples
Embodiment Construction
[0041] The present invention will be further described below in conjunction with the accompanying drawings.
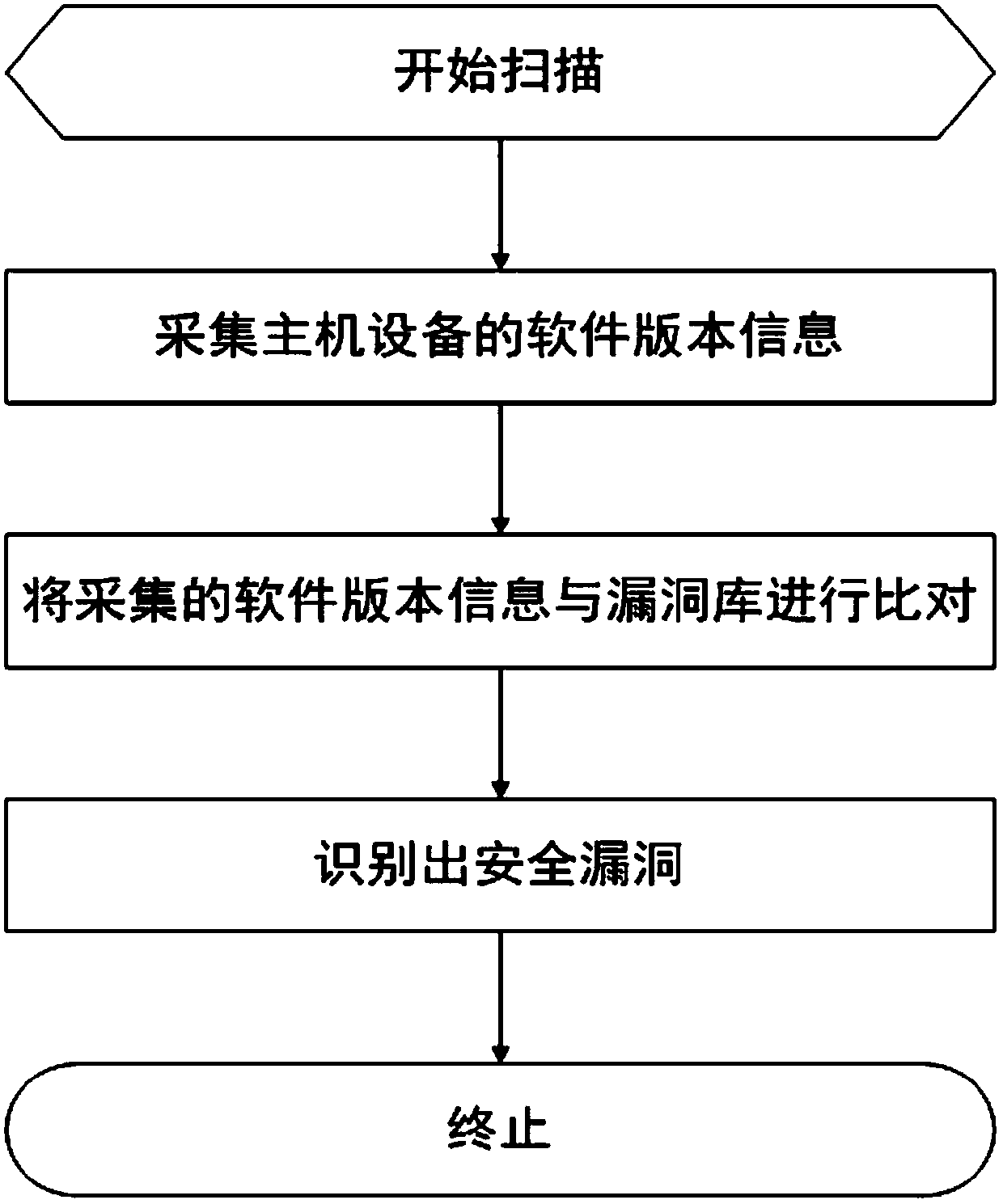
[0042] Such as figure 1 As shown, it is a working flow chart of a host device vulnerability scanning method for a power monitoring system provided by a specific embodiment of the present invention. The method includes the following steps:
[0043] Step 1, collecting software version information of the host device.
[0044] The host device includes any one of a server, a gateway machine, and a workstation;
[0045] The method for collecting the software version information includes the following steps:
[0046] (1) Deploy the vulnerability scanning script and the host operating system security monitoring program Agent on the target host device at the same time. The Agent supports the operating systems commonly used in host devices in power monitoring systems such as Meditation, Kirin, Linux, Unix, and Windows;
[0047] (2) Call the Agent, and use dpkg and rpm to find...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com